Category Archives: Uncategorized
It finally happened

I have the feeling this story could get convoluted. Let me sum up right at the beginning: I have finally received a threatening letter accusing me of copyright infringement, from the Entertainment Software Association (ESA). Some background:
I have been playing vanilla WoW, off and on, for months on a private server known as Elysium-Project. I wrote about the experience not too long ago right here on this site (we’ll get to Felmyst later in this post). The thing about this server is that in order to download the client you have to do so through a torrent, which right away gives the impression of impropriety. I had downloaded it once before, using the uTorrent client, to use on my desktop, and everything seemed above the board.
Recently, though, I downloaded it again, using the exact same torrent client, however this time it was on my laptop. Immediately, even before the file finished downloading, I received the following email from my ISP, Cox Communications:
Dear Customer,
We are forwarding a notice received by Cox Communications which claims that someone using your Cox High Speed Internet service has violated U.S. Copyright law by copying or distributing the copyrighted work listed in the attached complaint. THIS COMPLAINT IS FROM A THIRD PARTY AND NOT FROM COX COMMUNICATIONS. We have included a copy of the complaint, which identifies the party making the claim, the title or work they claim was infringed, and the date of the alleged infringement.
We ask that you review the complaint and, if you believe it is valid, promptly take steps to remove or disable access to the infringing material (typically movies, music, books, or TV shows). If other parties are using your account, such as through your WiFi connection, you should ask them to disable file-sharing in peer to peer applications such as BitTorrent, or delete the copyrighted works.
If you disagree with the claims and believe that no one using your Internet service could have been the source of the alleged infringement, please do not contact Cox Communications to resolve this matter. Cox is simply forwarding the notice to you. However, if you have WiFi, please make sure your WiFi connection is secured with a strong password to prevent unauthorized use of your Internet service. In addition, make sure anti-virus software is installed and up to date to help prevent malware infections.
PLEASE NOTE: THE ATTACHED NOTICE MAY CONTAIN A SETTLEMENT DEMAND FOR MONEY OR OTHER TYPE OF OFFER FOR YOU TO CONSIDER. YOU MAY WANT TO CONSULT WITH AN ATTORNEY REGARDING YOUR RIGHTS AND RESPONSIBILITIES BEFORE CLICKING ON ANY LINK OR VISITING A WEBSITE LISTED IN THE NOTICE.
The material that you share online or make available for sharing is your responsibility. Cox encourages responsible Internet use, but we do not monitor nor control the information you transmit. We have a policy, however, consistent with the Digital Millennium Copyright Act, to take steps when we receive notifications of claimed infringement. We also have a policy of terminating repeat infringers in compliance with the Digital Millennium Copyright Act Safe Harbor for online service providers.
If we continue to receive infringement claims notices for your account, we may in appropriate circumstances suspend your account, disable your Internet connection, and/or terminate your Internet service.
For information about Cox’s Acceptable Use Policy, including copyright infringement, please refer to:
https://www.cox.com/aboutus/policies.htmlTo learn more about your responsibilities concerning copyrighted material, please refer to our help article at:
https://www.cox.com/copyrightGeneral information & FAQs about DMCA notices:
http://www.respectcopyrights.org/
http://www.riaa.com/toolsforparents.php?content_selector=resources-music-copyright-notices
If you would like to reply to this email, please keep the subject line intact for tracking purposes.
Sincerely,
Cox Customer Safety
— Original Message —
[Part 0:0 (plain text)]
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA12017-10-07T03:15:10Z
Entertainment Software Association
601 Massachusetts, NW, Suite 300, West
Washington, DC 20001 USAAttention:
Intellectual Property Enforcement
Website: http://www.theesa.com/wp-content/uploads/2014/12/DMCA-FAQs-Updated-12-2014.pdf
E-mail:
[email protected]Cox Communications
Re: Copyright Infringement by Cox Communications Subscriber
Using IP 98.164.255.62 on 2017-10-07T03:14:58Z (the “Subscriber”)
Reference Number c7ed1b3845618ac0d707Dear Cox Communications:
The Entertainment Software Association (“ESA”) is the U.S. trade association that represents the intellectual property interests of companies that publish interactive games for video game consoles, personal computers, handheld devices, and the Internet (hereinafter collectively referred to as “ESA members”).
A list of ESA members can be found at http://www.theesa.com/about-esa/members/.
Under penalty of perjury, we affirm that ESA is authorized to act on behalf of ESA members whose exclusive copyright rights we believe to have been infringed as described below.ESA is providing this notice pursuant to the Digital Millennium Copyright Act (“DMCA”), 17 U.S.C. section 512, to request that you take immediate action with respect to infringement of ESA member copyrighted works by your Subscriber.
Using the IP address on the date and time referenced in the subject line of this notice, the Subscriber or someone using their account employed a peer-to-peer service or software to distribute one or more infringing copies of ESA members’ games, including the following title:Warcraft (franchise)
Courts in the United States have held consistently that the unauthorized distribution of copyrighted works using peer-to-peer or similar services constitutes copyright infringement.
E.g., MGM Studios, Inc. v. Grokster, Ltd., 545 U.S. 913 (2005); BMG Music v. Gonzalez, 430 F.3d 888, 891 (7th Cir. 2005); Arista Records LLC v. Lime Group LLC, 2010 U.S. Dist. LEXIS 46638, *49 (S.D.N.Y. May 11, 2010This Subscriber should understand clearly that there are serious consequences for infringement.
The Copyright Act in the United States provides for statutory damages of up to $30,000 per work infringed, and up to $150,000 per work for willful infringement.
17 U.S.C. section 504(c).We ask that you work with us to protect the intellectual property rights of ESA members by:
1. Providing the Subscriber with a copy of this notice of copyright infringement, and warning the Subscriber that his or her conduct was unlawful and could be subject to civil or even criminal prosecution.
2. Promptly taking steps to stop the Subscriber’s infringing activity.
3. Pursuant to 17 U.S.C. section 512(i)(1)(A), as appropriate, terminating the account of the Subscriber if your records show that he or she is a repeat copyright infringer.ESA has a good faith belief that the Subscriber’s reproduction and/or distribution of these copyrighted works as set forth herein is not authorized by the copyright owners, their agents, or the law.
The information in this notification is accurate.
Neither ESA nor its members waive any claims or remedies, or their right to engage in other enforcement activities, and all such claims, rights and remedies are expressly reserved.If your Subscriber has additional questions about this notice, we would encourage them to visit http://www.theesa.com/wp-content/uploads/2014/12/DMCA-FAQs-Updated-12-2014.pdf to learn how to delete the infringing material and avoid receiving future notices.
Thank you for your prompt attention to this matter.
Sincerely,
Intellectual Property Enforcement
Entertainment Software Association
Website: http://www.theesa.com/wp-content/uploads/2014/12/DMCA-FAQs-Updated-12-2014.pdf– ————- Infringement Details ———————————-
Title: Warcraft (franchise)
Timestamp: 2017-10-07T03:14:58Z
IP Address: 98.164.255.62
Port: 33768
Type: BitTorrent
Torrent Hash: 2b32e64f6cd755a9e54d60e205a9681d6670cfae
Filename: World of Warcraft 1.12 Client.rar
Filesize: 5197 MB
– ———————————————————————<?xml version=”1.0″ encoding=”UTF-8″?>
<Infringement xmlns=”http://www.acns.net/ACNS” xmlns:xsi=”http://www.w3.org/2001/XMLSchema-instance” xsi:schemaLocation=”http://www.acns.net/ACNS http://www.acns.net/v1.2/ACNS2v1_2.xsd“>
<Case>
<ID>c7ed1b3845618ac0d707</ID>
<Status>Open</Status>
<Severity>Normal</Severity>
</Case>
<Complainant>
<Entity>Blizzard Entertainment, Inc.</Entity>
<Contact>IP-Echelon – Compliance</Contact>
<Address>6715 Hollywood Blvd
Los Angeles CA 90028
United States of America</Address>
<Phone>+1 (310) 606 2747</Phone>
<Email>[email protected]</Email>
</Complainant>
<Service_Provider>
<Entity>Cox Communications</Entity>
<Email>[email protected]</Email>
</Service_Provider>
<Source>
<TimeStamp>2017-10-07T03:14:58Z</TimeStamp>
<IP_Address>98.164.255.62</IP_Address>
<Port>33768</Port>
<Type>BitTorrent</Type>
<SubType BaseType=”P2P” Protocol=”BITTORRENT”/>
<Number_Files>1</Number_Files>
</Source>
<Content>
<Item>
<TimeStamp>2017-10-07T03:14:58Z</TimeStamp>
<Title>Warcraft (franchise)</Title>
<FileName>World of Warcraft 1.12 Client.rar</FileName>
<FileSize>5450407230</FileSize>
<Hash Type=”SHA1″>2b32e64f6cd755a9e54d60e205a9681d6670cfae</Hash>
</Item>
</Content>
</Infringement>
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1iQEcBAEBAgAGBQJZ2Ea9AAoJEN5LM3Etqs/WBF0H/jpN7FftxC1K3kUH9j6jG4IZ
A7abndRK8UZISWGRCmT0Tj7+itlRmvzwo9/ggZl9RxiuIPR8KCr/cHTgIbcimjni
ycdjkB6kLOi6FHOA8FybJCVdLK/hMlVvKum/WG4j4oaYBf0LEtowXM1DT1XU7GEy
0F8gUaL5waoJjXuZsA/p88LUhb3Wpmx4BQ6CpzXo96We/JDd+rIApkUsEq56m71s
4Qy5gK3VQVvd3DxqEFZEfU984RBYB3j8i3RCRrHssLUUa4L02Gp3AYpc0szmcOQ8
ZZAtJTOjkCmBUllxo9LNCwgDDQwtybL/QedED4+amO2h7tlLoYfZtuH6qRshpLM=
=iSCJ
—–END PGP SIGNATURE—–
There’s a lot there, but essentially what it is saying is that I committed a copyright infringement not by downloading the Warcraft client, but by also allowing it to be seeded and therefore distributing it. It’s like drug enforcement; the dealers are the problem much more so than the users.
I also have to say I find some amusement in the otherwise serious nature of this email, in that while the complaint from the ESA was very serious and implied significant fines, federal crime, even possible jail sentences, the portion from Cox essentially says “Hey, this is what we were told, now keep us out of it.”
The fact that it came in late on a Friday night while the file was still downloading also makes it quite clear the whole process was automated, both the email to Cox and their forwarding it on to me.
I blame myself for part of this as I never thought to switch off seeding, and when I tried to connect to the private Elysium server after the client download was complete, I neglected to modify what’s known as a realmlist.wtf file to point to Elysium’s server as opposed to the stock Warcraft server. That means that I was attempting to connect directly to Blizzard at first. That’s not what the complaint was about, it was about the redistribution of their client via torrent, but the fact I made that connection error at first was not lost on me.
I don’t anticipate any major problem from this. The second the file was done downloading I deleted the original torrent file and shut down the torrent client. I don’t like to use my limited bandwidth to seed the downloads of others, and I don’t have anything they would want anyway, especially not on my laptop.
So I am ignoring it for now, and in fact I have done what they asked (demanded) I do. It also leads to an interesting legal issue: If you read my previous post about my early experiences on Elysium, you would know that there had been another private server, Felmyst, that was shut down on its very first day, apparently because they were distributing the client along with the game files (or something like that). Elysium, on the other hand, is able to stay up and running because they don’t distribute the client, and therefore no copyright violations are taking place. That seems strange to me since we are playing on a server that uses entirely Blizzard-created assets, but who knows. A quick Google search indicates I’m far from the only one experiencing this, and the issue of monetary gain versus non-profit can have serious implications and Blizzard’s perspective isn’t always so black and white. They’re both very interesting reads.
What I can surmise is, and as I stated earlier, using the client/game once downloaded, even downloading the client itself, is not illegal; it’s the redistribution that’s the problem.
Don’t redistribute clients via torrent, people.
Cleaning battery terminals the easy and mostly-but-not-completely safe way

In my Human-Computer Interaction class, one of the in-class exercises students complete is a usability evaluation that requires them to evaluate a device randomly selected from a list of devices that I bring to class. The devices are nothing overwhelming: they include a numbered Rubik’s Cube, a water ring game, a backscratcher, a ping pong-ball gun to name but a few, and I have included a picture below of a select yet completely random few. In choosing devices for this exercise, which I am always hunting for in places like thrift stores, flea markets, swap meets, discount aisles, etc. (my rule is that I never pay more than $5.00 for an item I intend to use for this class exercise), I have to ensure they possess sufficient functionality to encourage a successful analysis yet are not overly complex.
Because of where I find many of these items, they are occasionally in need of some repair, or at least a vigorous cleaning. For the electronic devices, however, the problem can be more serious with the presence of corrosion from leaking or damaged batteries. If you read the manual for any electronic device, they always contain a section strongly advising that you remove the batteries if you intend to store the item for any length of time, yet few of us ever do, which references both reading the manual and removing the batteries. Because of that, corrosion is an issue I am faced with regularly.
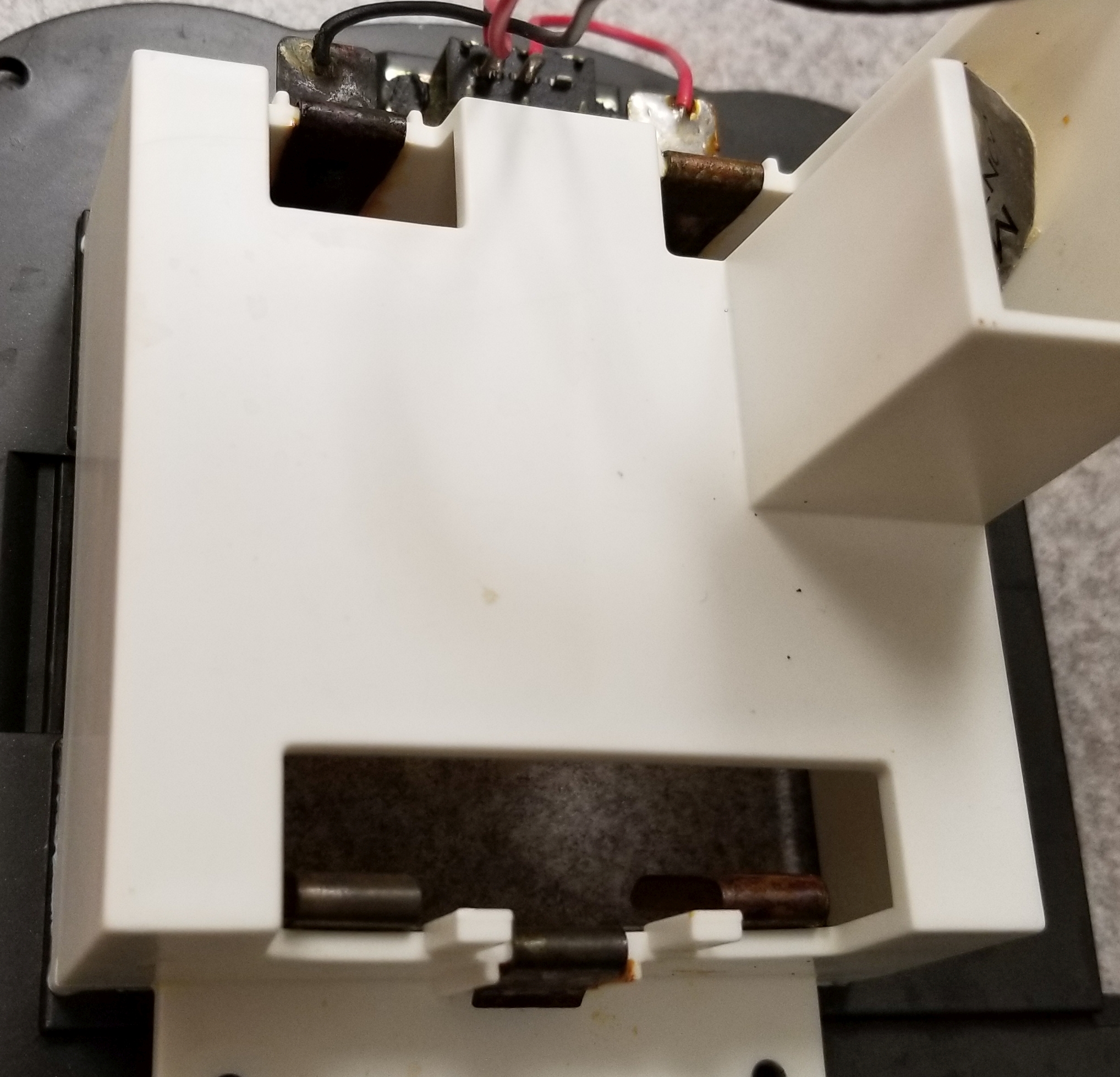
Recently, I acquired an LCD billiards game, which can be seen in the above image, that had aggressive corrosion not only on the terminals but on a solder joint and the plastic casing that sat above them as well. I knew they would have to be cleaned, and it reminded me that in the game collection I donated last year, there was horrendous corrosion on the terminals of the electronic castle from a Dark Tower board game and the handheld electronic component from a Lost Treasure board game. I am not proud of the fact that I left batteries in both those devices. Not only do I know that dead batteries will leak sooner or later, I also know it will happen much faster if left in a battery compartment where they are connected and continuously discharge, which is known known as a parasitic or vampire leak. That builds up hydrogen gas that will, thanks to the pressure, eventually cause a leak. I also know it will happen *much* faster when exposed to high heat. And these sat in a Las Vegas garage for ten years.
So for practical as well as penance reasons, I decided to tackle the corrosion problem and make a post about it to spread the word. It’s not hard to clean, frankly, although whether the device works afterwards is another step. But we’ll get to that – let’s talk about cleaning corrosion.
First was the small LCD billiards game. Upon checking the batteries, the corrosion was obvious, and when I opened it up it was even more than I had anticipated.
You can see the terminal itself is corroded, which is expected, however the corrosion has also clung to the spot where the battery lead is soldered to the main board, and even stuck to the casing above; in fact, it’s worse there! As mentioned, however, it is easy to clean, using only distilled white vinegar which neutralizes the acid into nothing, and the vinegar doesn’t have to be terribly strong – I use a generic brand that’s only 98 cents and is diluted to 4% acidity (acidity will be listed on the label). This is also an opportune time to mention that this only works with alkaline batteries; car batteries are something entirely different and require the using of baking soda and water. You can also use vinegar to clean the batteries themselves but I most certainly do not recommend this; once the leak has started the batteries are of little use anyway. Recycle them and use fresh batteries in their place. No matter what you do, wear gloves and eye protection – this is battery acid we’re talking about here.
I submerged the corner of the device in a small bowl of vinegar, and after a few minutes of aggressive fizzing and hissing, it was all clean. It’s wonderful how well vinegar works for this. You don’t have to do anything; no scrubbing, no washing, no cursing, the vinegar does all of the work, although it will stink afterwards. I recommend the previously corroded components get a rinse with water afterwards but that is not always possible, a gentle scrub with an old toothbrush to remove the odd bits if necessary (although it usually isn’t), let the components dry, and you’re good. The results of the cleaning are below, and the thing now works perfectly.
When I say the vinegar does all the work, I am not kidding.
Next up was Dark Tower, and this one was more difficult and less successful, although the problem isn’t the batteries. As you can see in the following images, the corrosion was extensive. The Electronic Component is a large plastic tower with a rotating segment that lights up, and getting to the corroded battery compartment meant disassembling the tower. Once done, the extend of the corrosion became evident.
Again with the vinegar! I submerged the whole thing in a bowl filled with vinegar, and after about ten minutes came back to find it all clean.
As you can see, there is still oxidation on them, and that will require a stronger approach with a bottle brush and hydrogen peroxide. In fact, the central unit still doesn’t work, and I can’t be sure if it’s because of the remaining cleaning that needs to be done or because of what appears to be a burn on the main board, which may also simply need a cleaning; there’s no component at the location to blow out. I will clean it all up and update with the results. It’s an impressive piece, and a magnificent, non-replaceable game, so I am intent on getting it up and running again.
Lastly was the corrosion in the electronic component of the Lost Treasure board game. This one was more difficult because it was a 9-volt battery terminal that had corroded, and a previous attempt to remove the battery had detached the terminal from the battery itself, which can be dangerous. I cut the connector and soaked the thing in vinegar, however while it was sparkling clean after that, it also left the positive terminal from the battery stuck in the adapter and no amount of finagling with an eyeglass screwdriver and needle-nose pliers was getting it out. Eventually the adapter gave way, detached, and that was that. Fortunately, those are easy to replace and I’ll wire one up when the ones I ordered come in.
I can’t fault the person who tried to remove the battery as I don’t recommend dipping the battery in vinegar to clean it, but it was cemented in place by the corrosion. Pulling out the connecting wire like that isn’t a very desirable result, but in this case I can understand why it happened. Incidentally, you know what 9-volt batteries have inside them? Little batteries!
So vinegar. Never mind about it’s uses for cleaning or washing hair or killing bugs or neutralizing pet stains or clearing your skin or…just look here. When it comes to neutralizing battery acid it’s a miracle worker. Rinsing with water afterwards and allowing to fully dry is important, as are gloves and eye protection, but if you have corrosion, you’ll find that the vinegar soak is usually enough to get any device working again.
The new Samsung Galaxy S8+
I’ve been using my new Samsung Galaxy 8+ for a few weeks now, and must say I like it. It has a slew of new features such as the occasionally functional face-recognition method of login, which according to Samsung I should not use if I have a twin, and I end up using the login PIN about half the time anyway, since wearing sunglasses, being in bright/low light, having your head at a different angle than what the phone expects, or wearing a Freddy Kreuger mask all seem to interfere with its accuracy. It also eschews the previous models’ physical home button for an on-screen equivalent, which can sometimes get lost in app overlays, and the back button rotates with the orientation of the phone which means it sometimes points up, not back. Plus it no longer comes in glorious gold, but I did get a neat metallic grey-blue.
The metallic blue branding on the box let me know I was in for something special. I wasn’t such a big fan of the quick start card telling me to follow the instructions on the phone, which in turn told me to follow the instructions on the card. I was almost stuck in an infinite loop.
Even with those caveats, it’s a great phone. It comes standard with 64GB of internal storage, however I popped in a 256GB MicroSD and have enough storage for everything. While other Galaxy’s supported this, my previous S5 did not and I ran out of space almost immediately, which caused repeated battles with those pesky storage demons for months on end. On the front, the S8+ is adorned with a magnificent 6.2 inch AMOLED screen that wraps around the edges, an ‘Infinity Screen’ as Samsung brands it, and you can slide in panels from the edge that house frequently-used apps. I never do that, but you can.
In the US, the phone runs on an 8-core Qualcomm Snapdragon at 2.35 GHz, which is powerful but on-par with competitors. International markets get Samsung’s own 8-core, ARM-based Exynos processor running at the same speed. Both are plenty fast and more than capable for most mobile applications, especially with 4GB of RAM packed in alongside. I was hoping to use Qualcomm’s own Vellamo benchmarking suite to put it through its paces, however it was nowhere to be found, so I fell back on the stalwart and well-established GeekBench 4, which provided a comparatively average single-score of 1830, but a scorching, second-place multi-core score of 6032, placing it only behind Huawei Honor V9. I should also mention that the scores earned by the phone are much higher than what they are reporting for the S8+ on their site.
(It needs to be mentioned as a warning that I also intended to use the well-known and oft-utilized AnTuTu mobile benchmark, however on boot it insisted I download an additional ‘phone verification app’ and even loaded the Play store to do so. I don’t know why it would require that, I’ve never heard of such a thing, it sounded very fishy, and the reviews of it were foreboding. Therefore, although I like AnTuTu generally, I must recommend that you not use it for mobile bench marking purposes.)
I was also quite pleased at the 3500 milliamp battery life: Using Google Maps for navigation, after an hour of use my battery power was still in the high 80 percentile, whereas the Galaxy S5 would have been long dead by then. Speaking of which, it also supports Qi wireless charging, however be aware that is a misnomer: While you can rest the phone in a dock and have it charge thanks to two coils in the back, the dock itself still has to be plugged in. It doesn’t just magically charge from the air, although I am still waiting for that feature. The 12-megapixel rear camera takes stunning photos, and you can even elect to have them stored in RAW format. May as well, you’ll have the room. I don’t use the front camera except for the once-in-a-blue-moon mobile Skype call, so I can’t comment in any meaningful way on its quality, however it’s an 8 megapixel component.
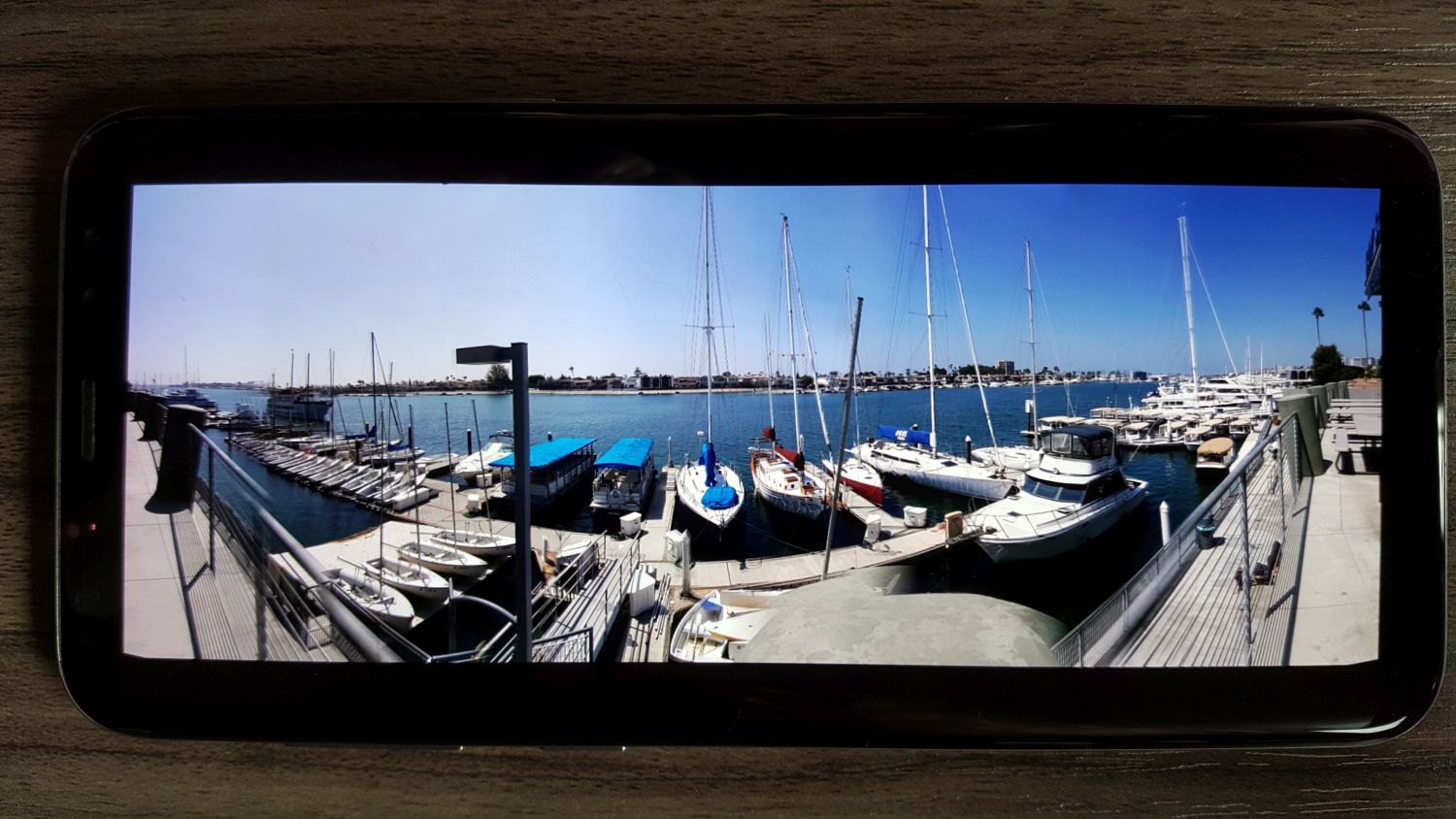
In the first image below, taken at a mid-level setting and moving at ~70 miles an hour, the wind farm comes out quite clear with separation among colors from the rich blue at the top to the white of the mills in the center (even considering the haze that muddies the contrast along the horizontal center) and the darker colors of the earth and road at the bottom. Minimal blur with good color even at speed. Below that, a few pictures from my trip to Monsterpalooza in Anaheim, and even in low light conditions there is still sharp contrast and detail, except when an area of the image was in competition from multiple light sources as can be seen in the sign to the right of Frankenstein.
- Horror Heads
- Frankenstein (note competing lights on sign)
- Captain Quint
- Nosferatu
Another aspect of the phone I really appreciate this time around is when a known or suspected scam call comes in, the phone displays the contact name either as ‘Potential Fraud’ or ‘Potential Spam.’ I don’t know what the difference is, and like to think I could guess it anyway, but there have been no false positives or missed calls because of it so far. Also note the beautiful 1080P screenshots the phone takes.
I’ve been very happy with it so far. I haven’t had the chance to run it though its paces save for some movie streaming from my Plex server, which worked flawlessly, and with everything else it hasn’t hiccuped, stuttered, or frozen up yet. It doesn’t even get as hot. I’m still not thrilled about the lack of a physical home button, and once I transfer over all 13,672 files in my music library and see how it handles that in terms of performance and usability I’ll have a better idea of its overall capabilities. They’re also sending a complementary GearVR version 3, but every two weeks they inform me it will take six to eight weeks so I don’t know when it will get here, but with the S8’s USB type C connector, it won’t work with my old version 1, but I’ll update as soon as I can put it through it’s VR paces too.
IoT skills, deployment lagging behind expectations
Because I am teaching a project class in ubiquitous computing this quarter, I was struck by a post on the BPI (Business Performance Innovation) network discussing the results of a survey they conducted along with Nerdery and the Internet of Things Institute that states while industry does genuinely wish to adopt IoT strategies and deployments, they’re not happening as quickly as their enthusiasm might make it seem.
I can’t say I’m surprised by this. The most striking statistic as one reads through the report is that “…just 1.5 percent of executives at large companies say they have a clear vision with implementation well underway, while another 57 percent are either beginning implementation, have pilots underway or are committed and in the planning stages.” It’s the ‘clear vision’ aspect of this that is truly telling, especially when paired with the rest of the sentence. Immediately the question that presents itself is ‘If only 1.5 percent of executives have a clear IoT vision, how is it that 57 percent can be at various stages of design and/or implementation if they don’t?’
One clarification: In my class, and for the purposes of simplicity, we use Ubiquitous Computing and Internet of Things (IoT) interchangeably, however they’re not quite the same and I do let my students know that. The IoT is a subset of the concept of Ubiquitous Computing, the platform on which it’s enabled, similar to how the Internet is the technical foundation on which the Web operates. With that out of the way, the one issue I run into more than any other in this course is the belief of a small contingent of students that it should be a programming course, that they should be learning how to program sensors and the IoT protocols and whatnot. What I explain to them is that anyone can buy a book on how to program for the IoT; what they can’t buy is a book on how to think about the IoT. Like all technologies, IoT technologies can’t, as I tell them ad nauseum, be developed in a metaphorical vacuum. The technical issues of networking, the pragmatic issues of security and privacy, the enterprise issues of data collection and management, as well as many others, all must be considered as well when developing and deploying IoT strategies. After all, they’re not called strategies for nothing.
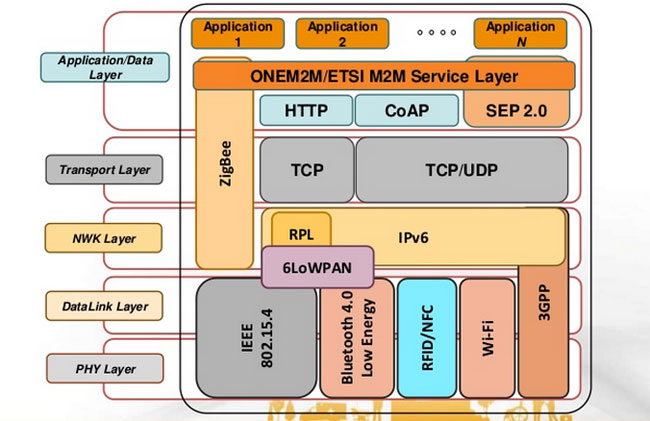
The second most common issue that comes up in this course is the question of what exactly the Internet of Things is. What defines it? What separates it from the regular Internet? Is that not an Internet of Things as well? How are they delineated? And where does ‘The Cloud’ fit in to all of this, if at all? Is that part of it? As is the case with all definitions, it can often depend on who you talk to. generally, in my class we define it terms of its low-power devices (sensors being the big ones) and lightweight protocols. However even in that case there can be disagreement and confusion. Do we need to make those delineations? The Internet is the Internet, yes? Do we need to divide it into TWO Internets, one for regular electronic devices and one for low-power sensors? What about our phones? Our TVs? They may be using Bluetooth but they certainly are not low-power, lightweight devices. And while this post isn’t meant to be about the technology per se, there are no fewer than twenty different protocols that can call themselves IoT protocols which has almost immediately led to standards overload. The image below gives and idea of this, although it contains both lightweight IoT as well as heavyweight regular networking protocols and where they fall in the TCP/IP stack.
And here’s this, for good measure, since we’re long past this moment in terms of the IoT. I rail against this all the time, but it never ceases to happen (and you should all read XKCD anyway):
True to this idea, The Technology Partnership in the UK states it should be called the Internet of Sensors, not the Internet of Things, since the Internet has always been an Internet of Things. A valid point, in my opinion, but then there’s also this. Let’s make up our minds, people!
And that brings me back to my introductory statistic. The linked article above has the following quote: “In my view, far too much attention is focused on getting the ‘Things” connected and not enough time is spent understanding the data insights that will actually drive the business forward.” That’s exactly right. Everyone is trying to figure out how they’ll get ‘things’ connected and get sensors out there and have an IoT strategy, but to what end? They’re so busy thinking about doing it that that they’re not thinking about why they’re doing it, what it all means, or if they need it, or how it will impact their business, or how it might impact their customers not just in terms of, say, improved customer service but also in terms of privacy and data collection and retention / distribution.
It’s important to take a step back and consider the gestalt of the IoT, and all the concerns and considerations that go along with it. It’s not a programming exercise; that’s just one low-hanging leaf on a vast tree of issues. I would hope that some people would be willing to take a step back for a moment, away from the headlong rush to have an ill-defined IoT strategy or deployment, and simply consider what it all means. We can all rush forward after that.
I guess no one tested this
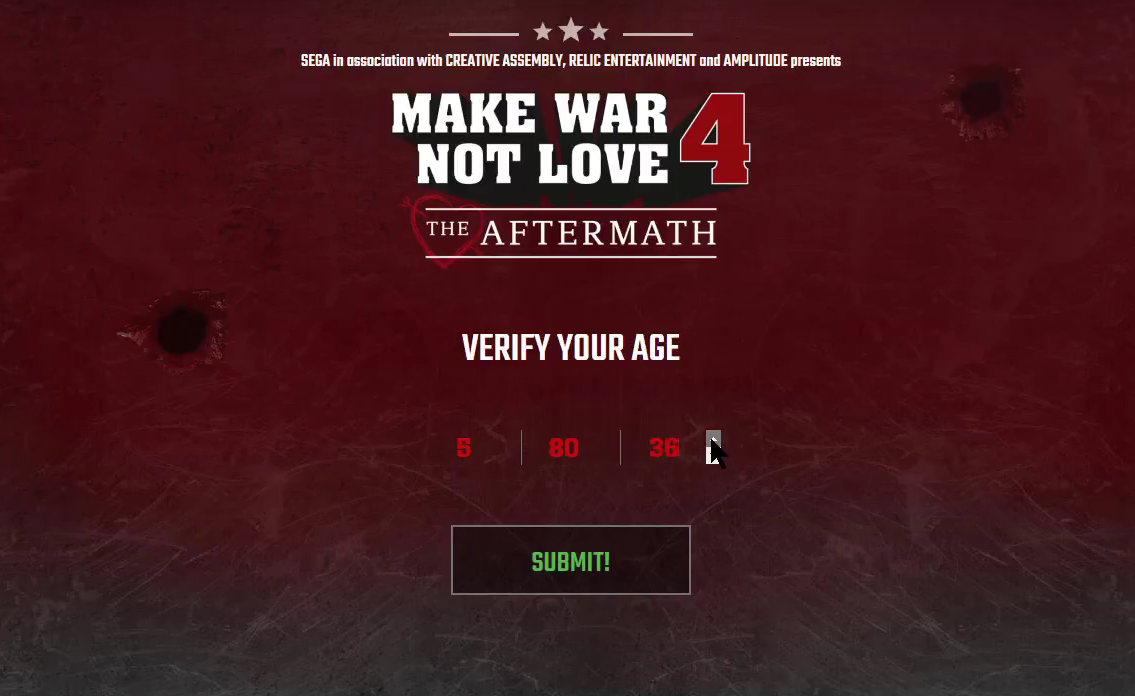
Some rules for interface design: Don’t allow users to make obvious errors, don’t provide them the means to make errors, limit their choices to only the ones that are relevant (or even correct), provide them flexibility within the confines of their task or goal, don’t introduce unnecessary complexity or redundancy (in terms of information or elements – the arrows I’m using in the video have no reason to exist), adhere to accepted conventions, and that’s just to name a few. How, then, did this travesty of a birthdate entry form come into existence? Who bothered to spawn it, and why? How bad could it possibly be? See for yourself, and marvel at what it provides.
Fixed! Or maybe not.
UPDATE: The error returned, so I restored a backup and recreated this post and the previous post. As sheer luck would have it, I had this site opened in another browser pre-backup, so I just copied the posts over from there. I’m not sure what is causing it although I am certain it has something to do with image caching. I will continue to investigate.
ORIGINAL POST:
One of the longstanding issues I’ve had with this site is that it is slow to respond and slow to load. Sometimes it’s very slow. My host, GoDaddy, is a great host and always very responsive, and even convinced me to upgrade my service but it never helped.
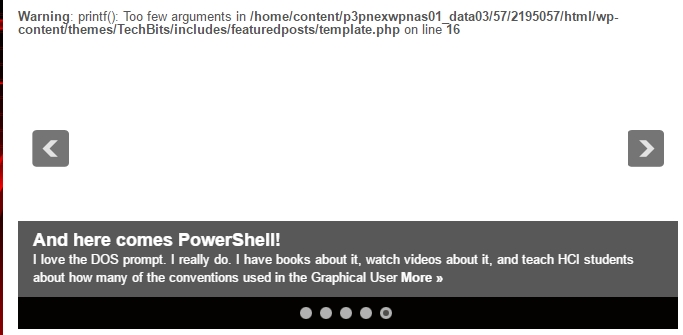
Recently, we determined it was a problem with image caching, and they suggested I do some back-end general caching to speed things up; it’s the first bit of bad advice they’ve given. I installed a plug-in that claimed it would do that, and the reviews were good, and it had 50,000 installs, so I thought ‘this seems ok.’
It didn’t improve performance, but at least it borked my featured post slideshow up there at the top as you can see in the header image. What was especially strange is that I couldn’t access that file mentioned in the error through the WP CMS editor; I would have had to download it via ftp, then edit and reupload it the same way. Luckily, rather than go in and edit the source, which can lead to further, much more significant problems, GoDaddy was able to restore a recent backup. Not only that, since I already had my most recent post – which was lost in the backup – open in another browser, I just copied it over and here we are! It’s still slow to load, but faster than it was, so we’re moving in the right direction.
Apparently I can do the backups myself if I wish (edit: I just did!), so next time there’s and error I’ll likely do that, although it will take some learning since I have to do it through my account page with my hosting provider. Anyway, crisis (not quite) averted, everything is working again.
Why Not?

I know people are mocking this, but my opinion is “who am I to judge?” If anything, I’m surprised it has taken so long.
The idea of virtual or holographic companions has been the stuff of science fiction for some time now. Cortana from Halo is one of the most well known, and now one of the most well-realized in her (its?) implementations within the Windows ecosystem, and the movie Her expanded on this very idea in a very moving and relatable way, presenting it as an evolution of society and technology that are merging closer and closer together. Of course, we can’t forget about Siri who, in fairness, was doing it to us first. And they’re hardly the only ones.
So now, a company called Gatebox has developed a sort-of holographic companion (it uses rear projection, a common technique for pseudo-holograms) that can act as a regular virtual assistant, however this one can be more…personal and adds a visual component that we haven’t seen before. It sounds unnerving at first. Taking on the appearance of an anime-inspired girl named Azuma Hikari, and living in a tank on your desk, she can provide not just assistantship, but companionship as well.
That’s right, for around $2,700 she will remind you of important events and dates and appointments, but she has been imbued with her own dreams and desires, hopes and wishes, just like a person. She’ll send you text messages, ask how your day was, tell you about herself and her thoughts. She can turn on lights and appliances, and connect to the Internet and talk about the weather or events or sports, or whatever else you’d like.
Most, but not all, articles talking about it have mocked it and its development, but I just can’t criticize it. it’s for release in Japan with no North American or European release in sight, and in my opinion that speaks to the Japanese culture, one of which I am very fond, but they dedicate themselves so much to work and school that there is little time for investment into personal relationships. This was designed and developed in part as a response to that, to give (generally) men who would otherwise be wanting for companionship a way to have someone with whom they can interact. People have pets for that very reason, so if someone doesn’t mind a holographic anime girl, then why not?
Perhaps there will even be additional characters. Maybe a snarky robot, or imp, or angry Australian guy, or a long-haired heavy-metal fan who converses in the same vernacular as I, or a sentient toaster; the possibilities are endless. For many of us, something like this would be a pure novelty, but if someone is genuinely lonely, or perhaps has an aversion to crowds or social spaces, or simply doesn’t have the time currently to invest in relationships, then I can’t find fault. If there is a demand for this type of technology, then as I said before, why not? Who am I to judge?
I genuinely encourage you to visit their website, it’s actually well-designed and gives you an almost first-person view of the device. I’m strangely interested in where this technology goes, and what its development says about us as people and a society.
Here’s the promo video. Make your own judgement.
Thank you Outlook Calendar!

Since Thanksgiving is only two days away, I would normally be writing some interesting and tech-oriented post about some turkey-themed technology or technology we’re thankful for (or not). However this year I thought I would instead briefly mention a curious notation on my Outlook Calendar. It’s not a huge thing, or a bad thing, just…curious.
It properly labels November 24th as Thanksgiving Day. However it labels November 25th as the Day After Thanksgiving Day. How strange. Do we not know that? It doesn’t label the 26th as the Day after Christmas Day, or July 5th as the Day After the Fourth. The strangest thing of all is that November 25th does actually have a colloquial name associated with it: Black Friday. The ‘Day After Thanksgiving Day’ just seems so matter-of-fact and odd to me, I’m having trouble processing its purpose!
Maybe I’m just reading too much into it. Or maybe Microsoft is playing the best prank ever. I don’t know. Where’s my turkey?
And here comes PowerShell!
I love the DOS prompt. I really do. I have books about it, watch videos about it, and teach HCI students about how many of the conventions used in the Graphical User Interface (e.g. cut/copy/paste) are taken from the command line, which were themselves taken from manual conventions used with typewriters (when typists made an error, they would often type the intended word on a separate paper, cut it out with an X-acto knife, and paste it over the mistyped word on the original document).
Although I frequently criticize techy types for being unnecessarily proud of their cult-like, obtuse, user-unfriendly platforms that require deep-dive understandings of underlying technology to get them anywhere close to working (I’m looking at you, FreeNAS and DD-WRT), I have to give the command line credit as it was all we had back then, we didn’t use it for bragging rights, and it worked well enough at the time while requiring some understanding of the underlying machine and software architecture.
However, it appears that the command line is being pushed to the back row. You’ll notice in the image below, which is of my very own Windows 10 Start context menu which appears when right-clicking on the start menu, there is the option for command prompt and command prompt admin.
In the following image, though, taken from a PCWorld post about the most recent Windows 10 Insider Build, Build 14971, you can see that the entries for command prompt are no more, and instead have been replaced with PowerShell.
What is PowerShell you might ask? If you were to just look at it, it might not look all that different from a standard command line. In fact, it IS a command line. However, rather than carrying out one command at a time as is typical with traditional command lines, hence their name, PowerShell allows for a host of capabilities that would be very difficult – although not impossible – via traditional command line commands. It allows for system and network/remote management, as well as scripting functionality supported by the .NET platform. It has many functions, which is also why the name PowerShell is both accurate and misleading.
You see, a shell is a command line. We’ve been using shells forever now, they even have allowed for the authoring of some basic scripts called batches in which a bunch of commands run all at once, but they were also very limited in the universe of the GUI. When a criminal attempts to put malicious code into or onto a system in the hopes it will run, that is often known as shellcode because it provides command-line access to the compromised system (if you’re interested, this is most commonly done through buffer/stack overflow attacks, of which there are many different kinds). Even PowerShell itself has been around for a long time. These types of interfaces have been a staple of computing since the birth of the PC and before.
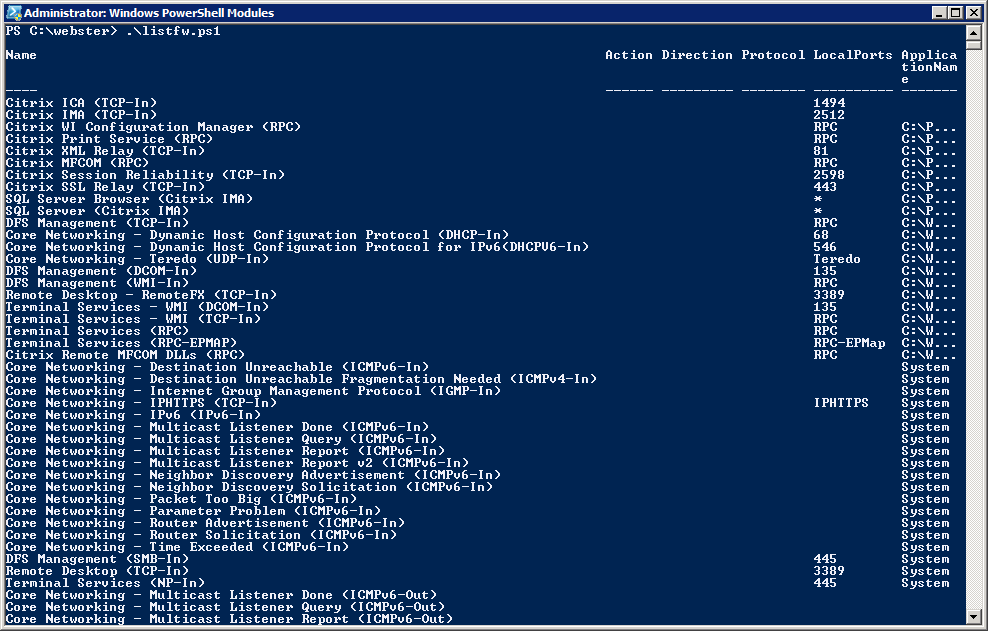
PowerShell is powerful, and has extensive capabilities that make it as useful as a GUI if you know how it works. Why not just use the GUI? Because a command line interface doesn’t use nearly the resources of a GUI, can run on a low-power system, gives much finer and more focused control than a GUI, and a command line interface won’t crash. You can see that I appreciate the power of the command line, and while I have nothing against PowerShell specifically, I also see it as the end of an era. The DOS prompt was so insanely unintuitive, yet comparatively simple as well; a true paradox. In PowerShell’s defense, here is a screenshot from the carlwebster.com blog showing it running a script that displays firewall rules. And that is just one example of the infinite amount of ways in which it can be used.
Apparently ‘Command Prompt’ can be brought back to the context menu through taskbar personalization settings so I may do that when the update finally rolls out, but I also want to give powerShell a chance – I haven’t used it that much but use the command prompt extensively, so who knows, maybe it will all be for the best. I’m approaching it with an open mind, and I’ll post my thoughts here when I’ve had the chance to work with it for a bit.
Destroy your stuff with just a USB stick

Hey, now this sounds fun! Want a simple, effective, and inexpensive way to destroy your expensive stuff and all the data on it? Well do I have good news for you! Now, with just a simple USB stick you can blow up damn near any digital device with a front-facing USB port (meaning publicly accessible, it doesn’t actually matter which direction the thing is actually facing. An important distinction).
The USB Kill will charge itself from the USB’s power supply, then discharge itself back into the port, over and over again until the host device is broken. Of course they say don’t use it for malicious purposes, but come on…why else would we want one of these things? Oh right – ‘testing’ purposes.
To be fair, everyone knows USB ports are a haven for malicious attacks, they’re the mosquito-breeding stagnant pond of digital devices, a very easy way to infiltrate a system or exfiltrate (steal or lose) its data.
It’s a pretty nifty device, in and of itself, and another interesting point they make is that only Apple devices are protected against this type of attack out of the box. Everyone else, well, look out (also, it might not destroy the data, and if it doesn’t, then NSA-approved bulk erasers are for you!).