Tag Archives: Passwords
Better change your passwords
Seriously. I’m not just telling you this because it’s World Password Day (it is, though, and I don’t know what Betty White has to do with anything). I’m saying it because it has come out that a security pro at Hold Security discovered an absolutely massive theft of usernames and passwords from Russia’s largest email provider, mail.ru, about 275 million stolen records. Not only that, there was a significant amount of credentials stolen from Gmail, Hotmail, and Yahoo account holders as well. Incidentally, many reports are saying ‘Microsoft’ instead of ‘Hotmail,’ which is a Microsoft property, but they also have Outlook which hasn’t, as far as I can figure out, been hit.
Most surprising of all, even more than the fact this is one of the largest theft of electronic records in history, is that the teenage hacker who acquired them was willing to sell the whole multi-hundreds-of-millions record lot for the grand sum of $1. But wait, there’s more! The hacker was discovered via his bragging of the theft in an online hacking forum, and when the Hold Security employee who engaged offered to leave positive feedback for the hacker, the price was dropped to free. That’s right, free for the mere quid pro quo of a positive review.
Off topic, but that touches on the concept of what is known as the reputation economy, in which someone’s actual worth depends on what others say about them in public and think about them in private. You can read more about it here.
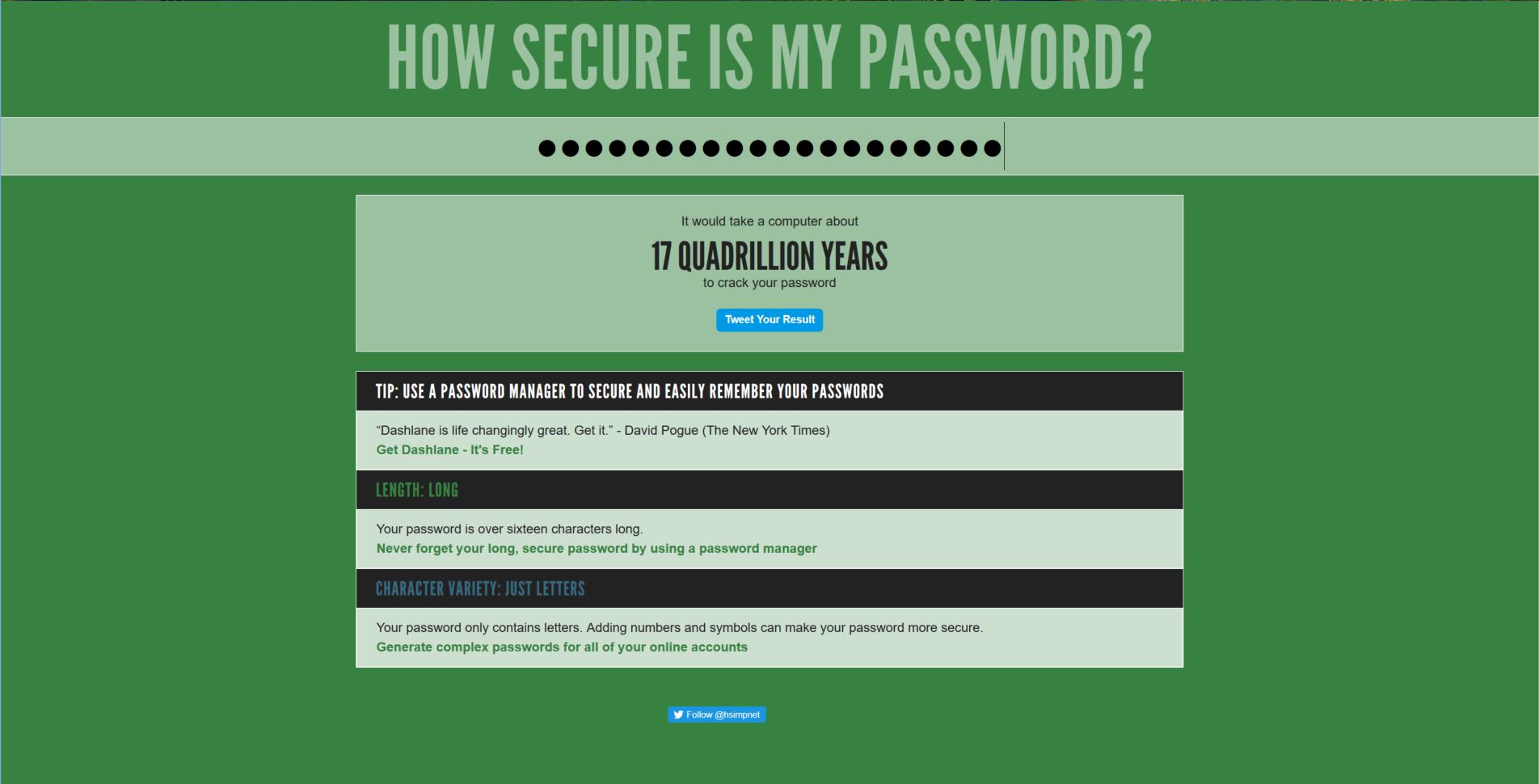
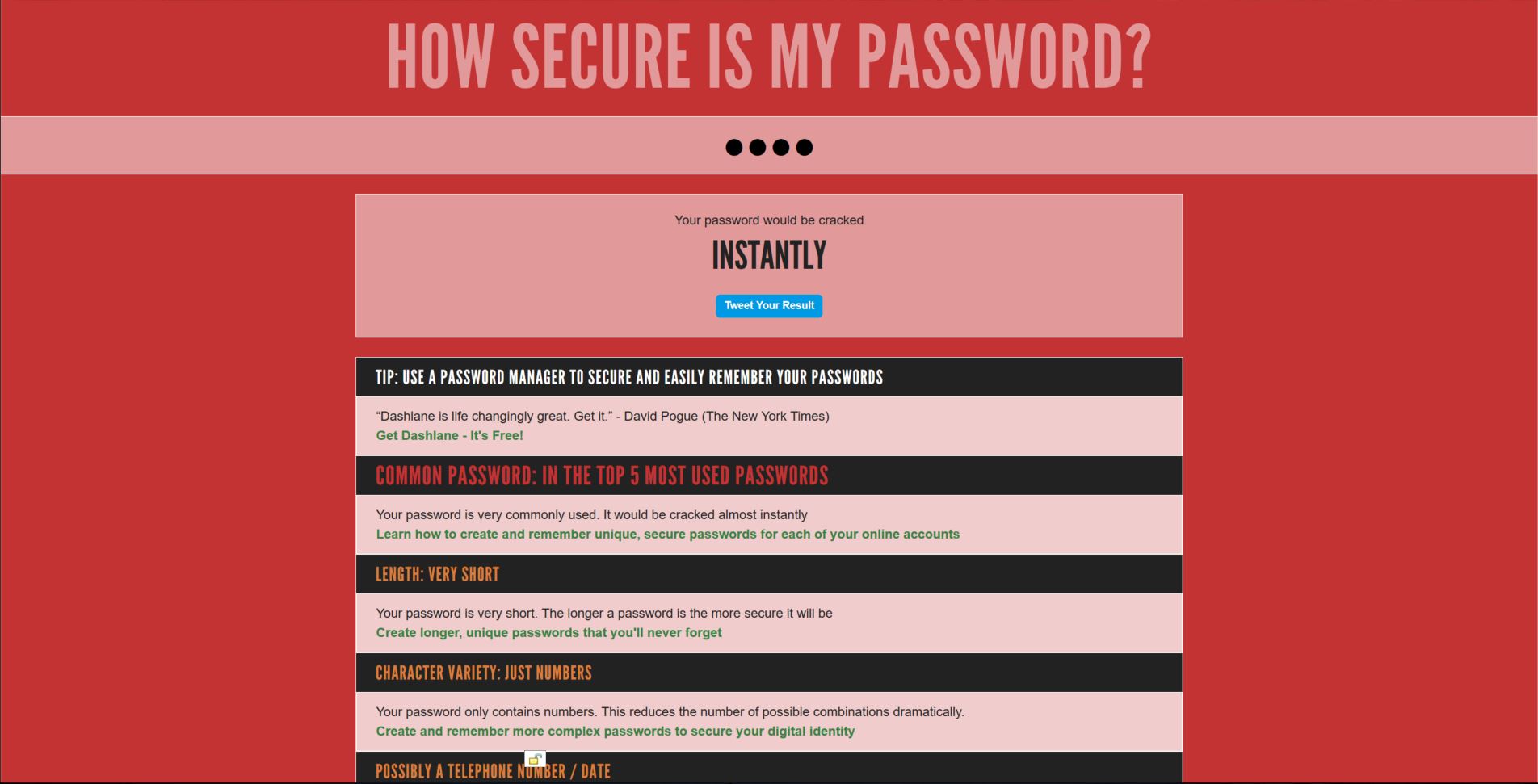
It’s no secret people use bad passwords all the time, and reuse them over and over for multiple functions and sites. Don’t do that! Use a passphrase – in class just today, my students suggested ‘sheturnedmeintoanewt,’ a line from Monty Python and the Holy Grail, which turns out to be a perfect passphrase. It’s long, complex, yet easy to remember. Plus, it would take 16 BILLION years to crack! How do I know? Because we plugged it into howsecureismypassword.net, and that was its estimate. Even if it’s off by a billion years or so, that’s still pretty good. If we capitalize just one letter, the ‘n’ in newt, it jumps up to 17 quadrillion years. This isn’t the be-all end-all for accurately determining password strength, but it’s a good estimator.
If you’d like to use a different password for each site or service, but are worried about keeping track of them all, you can use a password manager like KeyPass to manage them all. Some password managers even enter the passwords for you. I don’t know how I feel about that personally, but it is easier. Beware, password managers often have a master password and if you lose or forget that, you are screwed – you’ll be resetting passwords forever.
Everyone knows I hate passwords and especially the policies that go along with them, and I hope the scourge of passwords is one we can raze from this earth in the very near future, replaced with something more robust – but not 100% foolproof – like biometrics (fingerprint scanners, for example). Until then, just remember: It’s only a flesh wound.
I don’t know why I bother
SplashData has, as they are wont to annually do, released their list of the worst passwords of 2015. Definitely look at the link, there’s lot of additional information there regarding how dumb we are when it comes to this. Want to take a guess which terrible password takes the top spot? That’s right, 123456. Anyone suprised? Anyone? No? Frankly, if that’s your password, you deserve whatever happens. Not to be all alone, other number-based passwords made the list as well, including 12345678 and 123456789. Other idiotic passwords include qwertyuiop, login, and passw0rd. That last one is especially offensive, as though the person thinks they are pulling a fast one by having a zero instead of an o. They’re in for an unpleasant surprise.
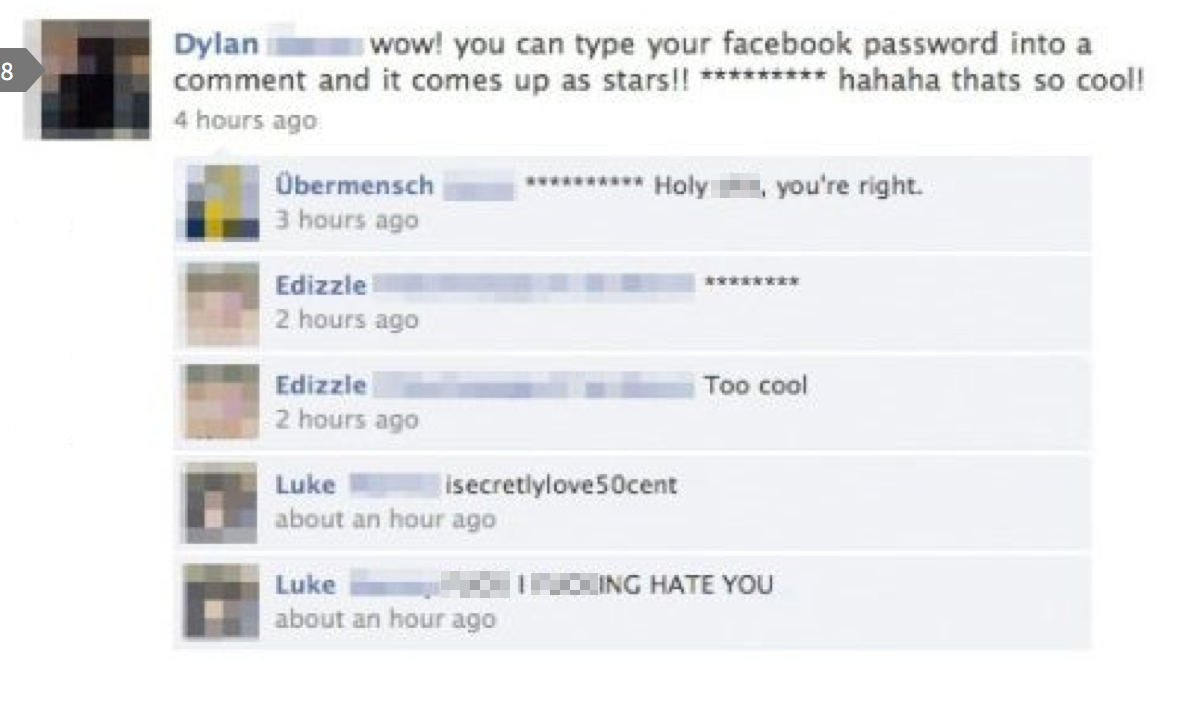
I used a different header image than I originally had intended, one that showed the bad passwords from 2014. They’re generally the same as last year, but I ended up not going with it because it was redundant considering the list below, but the original version of this post still referenced it. So I made a fun edit, and instead I found the Facebook post used in the header which – although I sincerely hope it’s fake – really very much hope that it is fake – shows how gullible people can be. If it’s real, I wouldn’t at all be surprised. Now hold on while I allow a Nigerian prince access to my bank account.
There are some passwords on the list that are less offensive, as though the person tried, including dragon and starwars, but geez oh man, at least throw a capital letter or exclamation point or something in there, even the passw0rd people up above did that. If you really need to make a strong password, remember a sequence of at least four random words is the best alternative, and hopefully one day passwords will go the way of the dinosaurs and disco (although I do love disco), and we can switch to things like biometrics full time. Here’s the full list, pasted from Cnet:
1 – 123456 (unchanged from 2014)
2 – password (unchanged)
3 – 12345678 (up 1)
4 – qwerty (up 1)
5 – 12345 (down 2)
6 – 123456789 (unchanged)
7 – football (up 3)
8 – 1234 (down 1)
9 – 1234567 (up 2)
10 – baseball (down 2)
11 – welcome (new)
12 – 1234567890 (new)
13 – abc123 (up 1)
14 – 111111 (up 1)
15 – 1qaz2wsx (new)
16 – dragon (down 7)
17 – master (up 2)
18 – monkey (down 6)
19 – letmein (down 6)
20 – login (new)
21 – princess (new)
22 – qwertyuiop (new)
23 – solo (new)
24 – passw0rd (new)
25 – starwars (new)
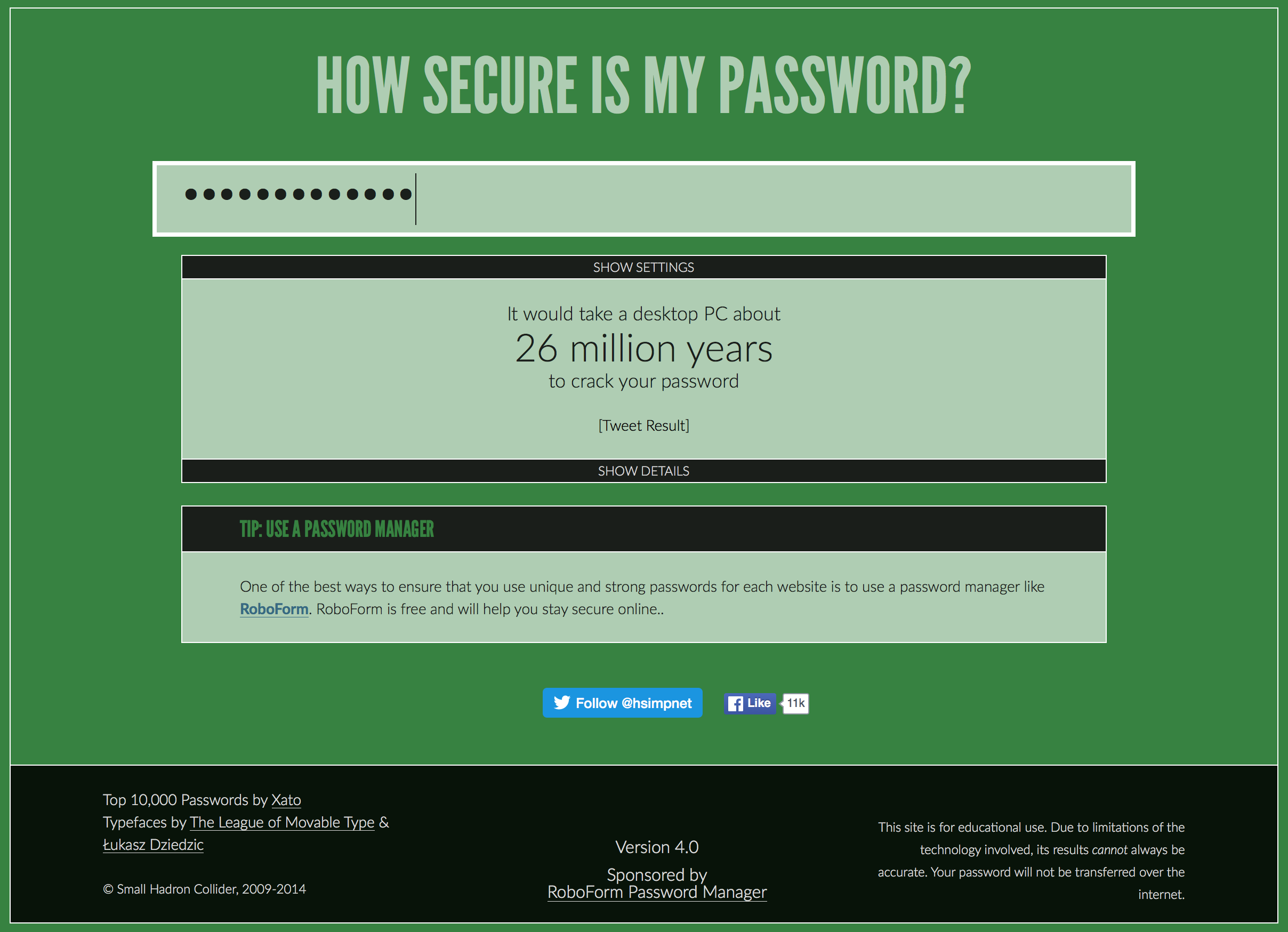
Incidentally, if you think you have a pretty robust password, and want to test if you really have the goods, you can go to howsecureismypassword.net and see. The site is legitimate, I promise, it’s not stealing your credentials or anything like that, and it will show you how strong your password really is. Here’s mine – I’ve got the process down.
The end of passwords? Hopefully.
Finally. Finally, formal standards have been published from the FIDO Alliance, whose aim is to do away with passwords through the use of techniques such as two-factor authentication and USB devices, and whose members list reads like a who’s who of big names: Google, Microsoft, Bank of America, Alibaba, ARM, Qualcomm, PayPal and Samsung, among many others.
I have been tired of passwords from quite some time, as you will or already have learned. Not only are you expected to have different passwords for everything, you are expected – in what I feel is the most repellant, counterproductive IT policy of all time – to change them every 90 days or so. Not only that, you can’t change them to something similar to the past five password you have used, and they have structural requirements involving length requirement, letters, numbers, it goes on and on and on. The result is that we end up re-using passwords that are easy to remember. Don’t believe it? Here you go:
The Nevada DMV’s unusual password requirements

I occasionally share personal experiences on this site when I feel they are of relevance to the class and deal with material we have covered or will cover in the future, but it has to be something of significant consequence for me to break that fourth wall.
As an example, I have trouble with websites all the time. They don’t load, they give me 404/page not found errors, they don’t load properly, but that happens and I don’t chronicle every experience here on the class page. No, it has to be something exceptional if I’m going to tell everyone about it, and this time it’s the DMV that gets to be the target. I had one of the most curious experiences on their website recently, and I think it warrants a post.
I wanted to renew my license online, seeing as going to the DMV is one of the most despised experiences one can have. To be fair, the last time I went to the DMV to take care of a pretty serious issue (expired registration), it was smooth sailing – I was in and out, including getting the car smogged, having it inspected, and getting my new registration all within about two hours. Not too terrible.
Even so, I was interested in trying out their not-terribly-new online functionality, but it turns out while going to the actual, physical DMV might be getting better, going online to the DMV is getting worse, at least in this case.
Before I get into it all, I must say their website is far, FAR improved from what it used to be, which was a cluttered mess of links reminiscent of the early days of Yahoo. Yet when it came to renewing my license there were two serious problems: The draconian password requirements, and the fact that the system didn’t tell me what I actually needed to do.
First, the recent celebrity hacking scandal has everyone fired up about password strength, and I’ve even heard a couple of TV commentators saying it reinforces how important it is to have complex, difficult passwords. That’s true to a point, and we’ll talk about that later in the session, but it’s certainly better than an easy-to-crack password.
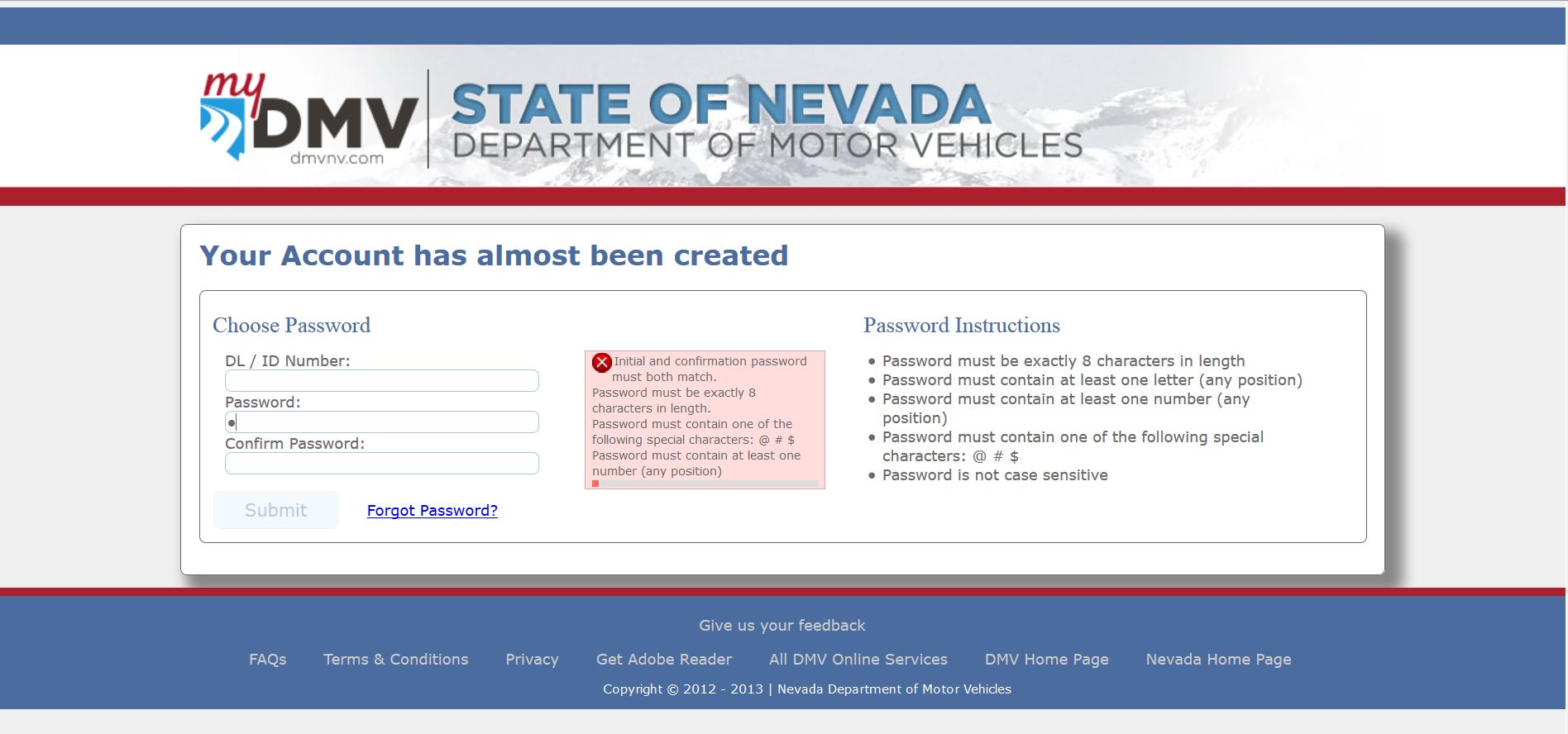
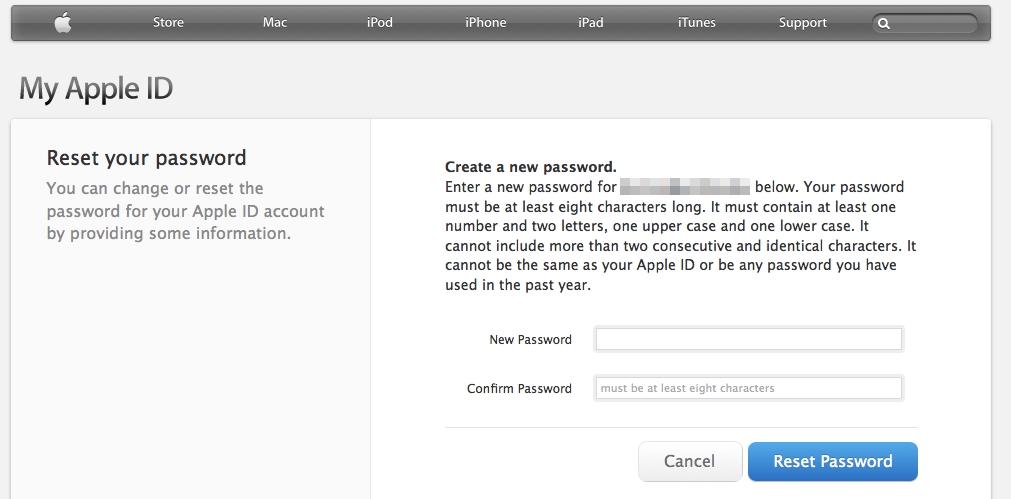
But in order to have that, you have to let people create them in the first place. The Nevada DMV does exactly the opposite. In what can only be described as an absolutely bizarre set of password requirements, it imposes restrictions that for the life of me I can’t begin to understand. In all my years of being involved in this industry, it is, without a doubt, the weirdest set of limitations I’ve ever seen. Here’s a shot of the webpage, and I’ll walk through it afterwards:
First, for what possible reason would you limit the length someone can make their password? The DMV isn’t big enough to argue it would be a storage or maintenance issue, and everyone knows that a longer password is more secure than a shorter one. This is no secret, it’s common knowledge. There are other issues of course, some of which we’ll talk about in this post and others we’ll talk about in class, but a basic rule is longer is better.
Next, they require at least one letter, but notice at the bottom it says “Password is not case sensitive.” What? Having case sensitive passwords (meaning the capitalization of letters in the password matters. For example, a lower-case ‘z’ could not be used in place of an upper-case ‘Z’) makes the passwords more unique, more complex, more difficult to crack, and like the length requirement above is very well known. Why they would limit the length and make them not case-sensitive is beyond me. You can read here about a bank that did the same thing and the response from the author and most commenters is of understandable incredulity.
They require a number, which is fine and a sensible requirement, but right after that they indicate you can only use one of three special characters: @, #, or $. No asterisk, no parens, no ampersand, just those three. As was the case with the previous restrictions I ask the same question again: Why? Why would you limit the types of special characters that can be used when just like before it is common knowledge that they contribute to the complexity of a password?
The whole experience was so strange, and frankly trying to create a password that met these requirements was very difficult, which of course means I’d have to write it down making the whole thing less secure. Unbelievable. Whoever decided on this needs to be strategically reassigned.
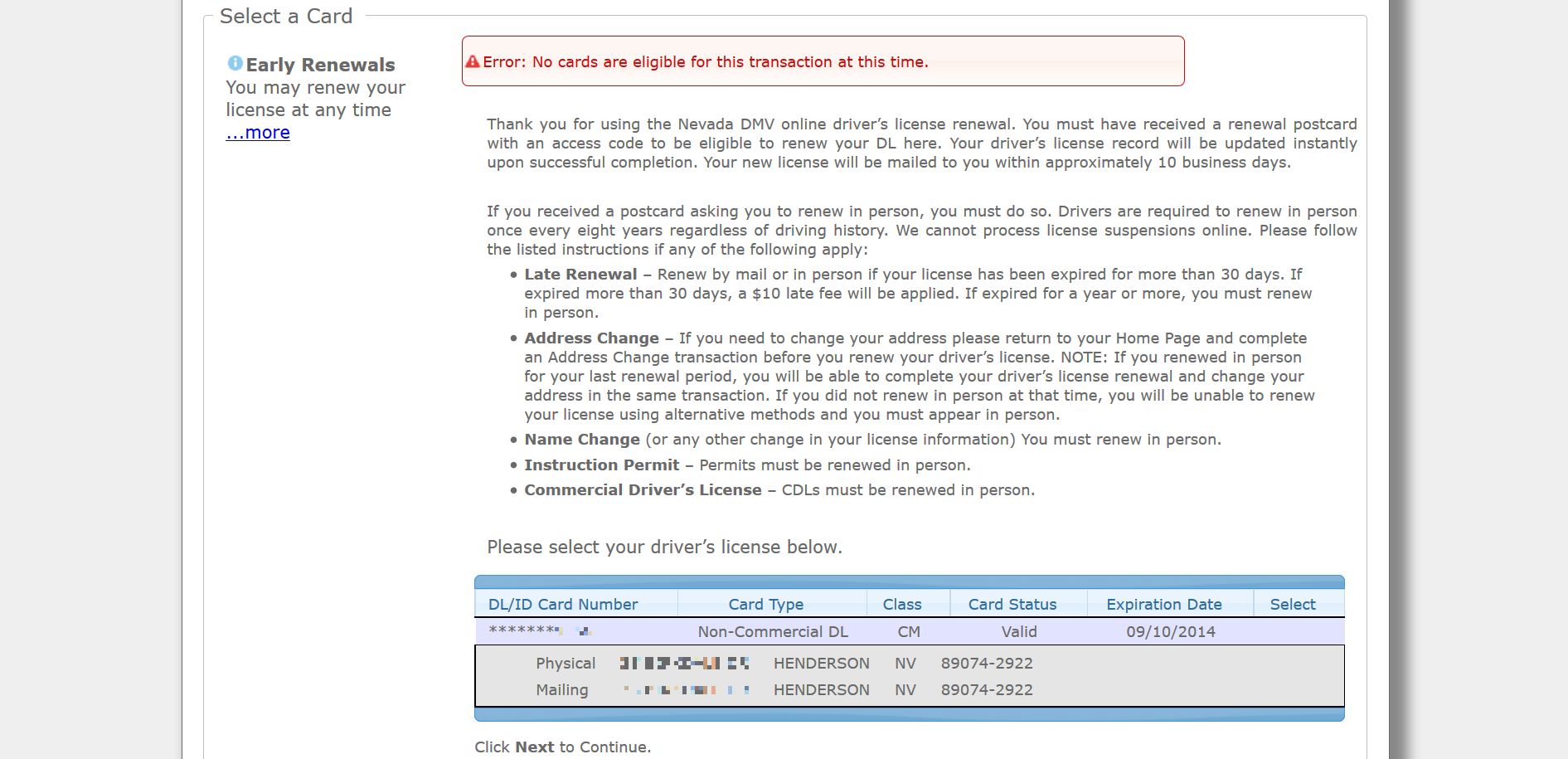
Of course, after finally getting through it all, I was presented with this screen:
Yes, even though I have had the card telling me my license will expire next week sitting on the table for a month, apparently the system that put me through the hell of its password requirements didn’t recognize I actually needed to renew my license in person. Instead, it simply said I had no cards that needed renewal. You can see it says “Click Next to Continue,” and although it’s cut off in the image there was no ‘Next’ to click, only a “Cancel” button. All that for…that. Apparently I have to go in because I need to have my picture taken, which based on my current picture is fine with me.
This was a password creation and system failure of epic proportions, and it shows me that something is seriously wrong over there. The system should not impose such limits on password requirements, and it should be aware I have to go in to renew my license because of the picture and tell me as much.
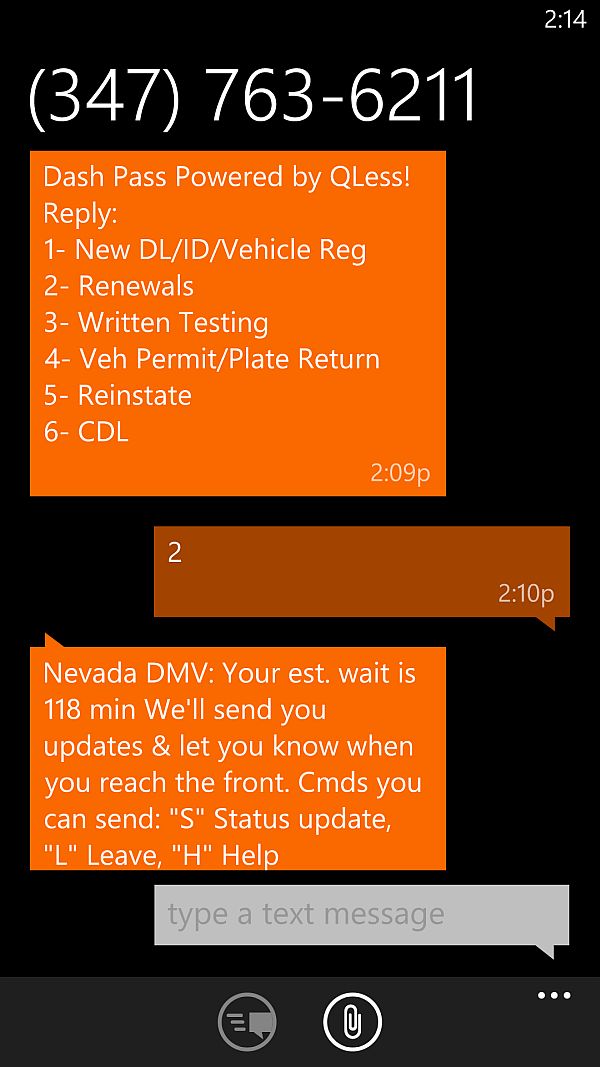
Having gone through all of this, however, there is something for which I must give them significant credit, that being the option they provide of simply texting ‘dmvhenderson’ (for the American Pacific location) to 347.763.6211, and they text you back a menu of options from which you can choose. You text them your choice, and they automatically place you in line for that function, providing you updates on your wait, your place in line, and how many people are ahead of you without you having to actually be there. They also provide the option for you to text them back for updates or to cancel, and you can even text them that you need more time. Very, very nifty. A screenshot of the texts that I received is below.