Tag Archives: Intel
A new exploit for Intel processors?
Whether or not this turns out to be a big deal is yet to be seen, but research from collaborators at UC Riverside, Binghampton University, Carnegie-Mellon Qatar, and the College of William and Mary, have discovered a new possible exploit in certain Intel processors that they have dubbed BranchScope – that link will take you straight to the research paper itself. The research is published in the Proceedings of the Twenty-Third International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS).
This is a new form of predictive execution exploit, in which the CPU attempts to predict what will happen as the result of a particular instruction, then branch based off of that guess, then guess what will happen as a result of that particular instruction, and so on. It’s the same kind of manner in which a computerized chess game plays chess: Every time you make a move, the game will play out thousands of games as a result of that, trying to guess the moves you will make and the moves it can make in response, and decide on an appropriate next move as a result. It doesn’t make this guess blind, either: In the processor is a component of the Branch Prediction Unit, or BPU, known as a Pattern History Table (PHT) that stores the results of previous operations, and each time a particular branch is taken, the ‘value,’ for lack of a better term, of that branch is increased or decreased. That allows the BPU to be more accurate in its future predictions (Spectre attacked the other part of the BPU, the Branch Target Buffer, which focuses on the result of a branch as opposed to the choice it made).
The exploit, therefore, is to set up selected branches that will modify the PHT and run them so that the PHT will always select one branch over another in a given situation, as well as monitor that the changes to the PHT have actually taken place. These attacks can be used to ensure a particular path is taken when predictive execution happens, and that can be used to divulge information that is otherwise unaccessible, even to the OS, such as key segments, or even provide access to the Software Guard Extensions (SGX), an Intel feature that allows deft software developers to place sensitive or critical data off in protected areas of the CPU cache that should, ideally, be available to none besides the program itself. The whole purpose of the SGX is to prevent bad actors from accessing the data.
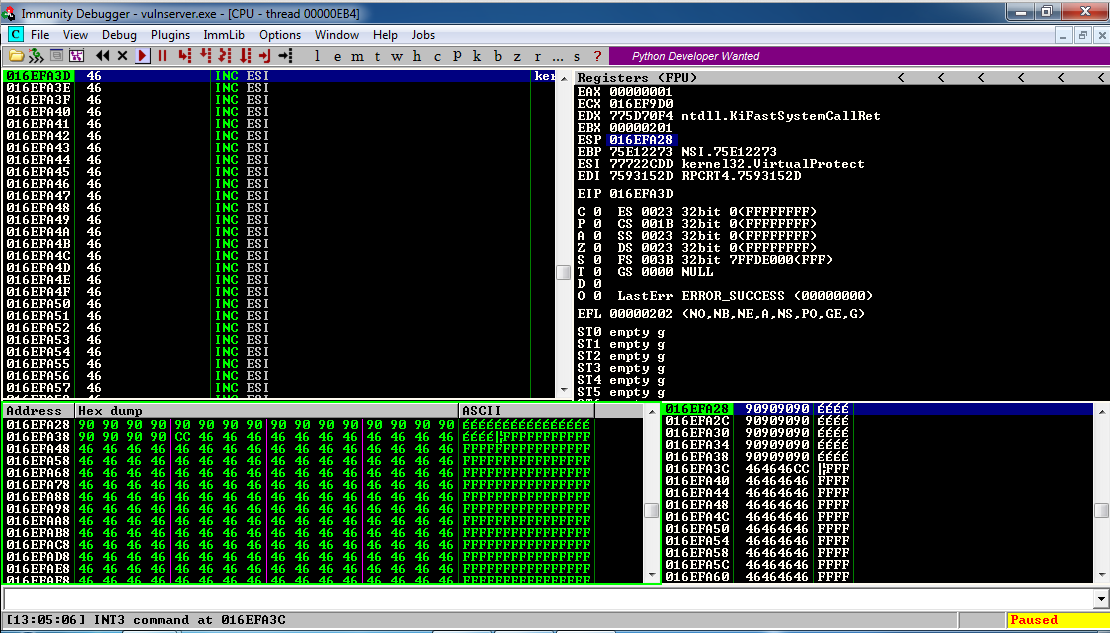
Both the Specter vulnerability and BranchScope as well remind me of the more widely-known and difficult to pull off NOP, or No-Operation, Slide (sometimes Sled or Ramp) type of attack, in which an attacker attempts to bypass a series of CPU instructions such that when an operation does happen, it ends up in a specific portion of memory where malicious code has already been installed and will then be run. These often fail, by the way, and in fact the section of memory that holds the malware will often be padded in front and behind so that the target memory location is bigger and the slide hits by luck; it’s a big shot in the dark. The hex value of the NOP is x90, and if you look at the image below which is tracing CPU instruction executions, you can actually see the slide happening as the series of ’90s’ at the top of the lower left and lower right window (source: samsclass).
This is called a side-channel attack because something is running that shouldn’t be, similar to how loading non-approved, outdated, or unkown-source OSs or apps on a smart phone is considered side-loading.
Predictive execution is complex, the exploits are complex, and as stated earlier, whether or not we see them in the wild is a completely separate issue; the payoff would really have to be worth the effort and I don’t see that being the case unless the exploit was adapted to pair with, say, a trojan horse-style attack, but even then the nature of the returned data would be useless without significant analysis. Knock on wood, but I don’t see this as a common attack vector in the near future.
Intel processors revealed to have major flaw, only addressable by OS updates

UPDATE: I’ve been trying to find out more, but Intel is now claiming it has a fix for the vulnerabilities affecting its chips that it will be rolling out by the end of next week. Details are slim, and I will hold off final judgment of course, but I’ll be surprised if it’s completely effective; these microcode patches can be tricky – it’s not a straight firmware update as it impacts the fundamental operation of the CPU. Additionally, it appears the fixes only address the last five year’s worth of processors. Better than nothing if it works.
Original post follows:
This is bad. It has been announced that Intel processors going back approximately ten years have a major flaw in how they separate the system and software. The details have not been released, but the general idea of the problem is already understood for the most part. To give a very high-level overview of what is going on and the impact of how it needs to be addressed, there is a component of every operating system known as a kernel, that separates the hardware from the software. When a program needs to open a port or save a file to disk or access a printer, or utilize hardware in any other way, it hands off that request to the kernel using what’s known as a system call, and the kernel completes the request (user mode to system mode). The catch is, the kernel is hidden from the program, even distributed in various memory locations to further hide it so that it can’t be exploited by malicious actors; it has to be loaded at system boot, however, in order for programs to use it.
Intel processors, though, use a kind of predictive processing, similar to client side prediction in games, in which a guess is made as to what will most likely happen next. In the case of Intel processors, they try to guess what code will be run next and load it up in the queue, however they apparently do this without any security procedures. The kernel is kept separate because it can contain confidential information such as passwords (which is why you can’t even get your own passwords back and there is no way to recover them if lost), however if the CPU provides no security check when loading up predictive code, it could, theoretically, run code that would ordinarily be blocked, which could then give savvy attackers access to low-level system processes and data.
But wait, there’s more bad news! Because this can’t be fixed with a firmware update or anything similar, OSs have to be written to address the problem. Linux, Windows, and OSX will all require updates that relocate the kernel in memory. Normally, it’s available to each program in their own process, but that will no longer be the case, and having to go back and forth between user mode and system mode in this manner will incur a possibly-significant performance hit on a PC after these updates, estimated by some to be as high as 30 percent.
Again, the details aren’t yet fully known, and the impact isn’t either, but if proven true it could be the worst design flaw I have ever seen. I’ll update when more is known.
Intel recalls all Basis smartwatches due to burn risk

I like to think I’m pretty up on the tech scene, but the first I’d heard of Intel’s Basis watch (Intel bought Basis for $400 million so they could enter the smartwatch market and diversify from their core chip business) was a slew of articles claiming they are now all being recalled because they can burn you. And not just burn you, burn you to the point of blistering your skin. Lots of technology gets hot, heat is a byproduct of chip architecture, but a watch that gets so hot it will burn your skin? Come on, Intel, of all companies.
In their defense, they say it’s only been an issue with .02% of all watches, and they first issued a warning back in June, but it looks like it’s starting to become more of a problem than they anticipated. So if you have a Basis watch, you can return it and any accessories you might have picked up to go with it to the retailer and get a full refund.
Oh, one other thing, from what I understand they were pretty good watches.
Stephen Hawking’s speech system gets an upgrade, comes with dire warning
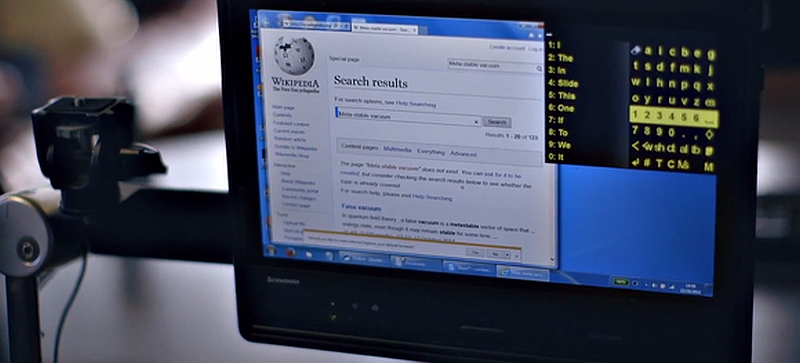
This week there are two important stories, both relating to Stephen Hawking and to topics we have discussed previously in class. The first involves an upgrade to the system he uses to communicate, and the second is a dire warning from the man himself.
First, regarding the system he uses to communicate. For the first time in twenty years, it has received a major overhaul in how it operates. The story was all over the place, however none of the articles about it did a very good job in discussing how it actually works. Instead, they all mentioned a cheek-operated switch attaches to an infrared sensor on his glasses that lets him use the system. That’s a non-explanation, and even the person involved directly with the process did a terrible job of explaining it as you can see in the video on this USA Today page, so hopefully I can add some additional detail that will help explain how it operates.
It’s true that because of his affliction he only has relative control over the muscles in his cheek, and that is how he interacts with his PC. Via an infrared switch on his cheek, which communicates with an infrared receiver on his glasses that then sends a signal to a USB key on the bottom of his wheelchair that then communicates the choice to the PC, he can make selections on a screen. You can see the sensor in his picture below, and it works like this:
Google raises Turing Award prize to $1 million

So much comes together with this announcement. The Turing Award, created by the Association for Computing Machinery (of which I’m a member, full disclosure) is the equivalent of the Nobel Prize for computer science. Founded in 1966 and valued at $250,000, it has been awarded for advancements and developments in all areas of computer science, from programming achievements to hardware to OS design and development, although it tends to skew towards methodologies and programming, which is understandable; it is a computer science award after all.
Previously jointly-funded by Intel and Google at a value of $250,000, Google has taken over the award funding after Intel ceased involvement and raised the value to $1 million. Considering the impact technology and computer science have in our lives (and the Alan Turing-based Google Doodle they created for his 100th birthday; do those numbers look familiar?), I think it’s about time, and it puts the Turing Award in league with the Nobel Prize, although the financial award for that fluctuates.
Look inside your CPU
(Important note: The program referenced in this post only works in Windows. I have searched for a MAC equivalent, however the only one there is hasn’t been updated in years and I don’t hold it in high regard).
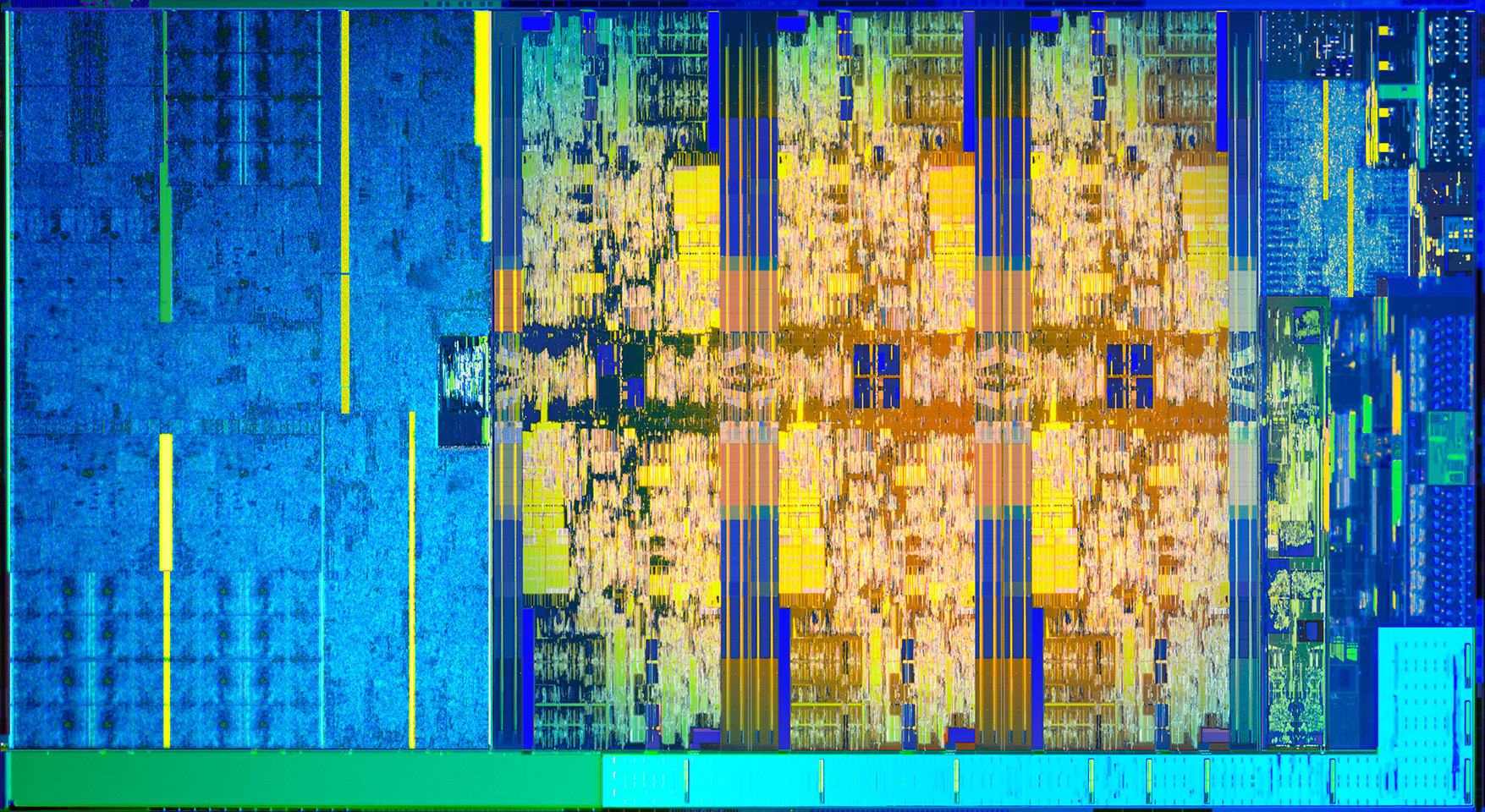
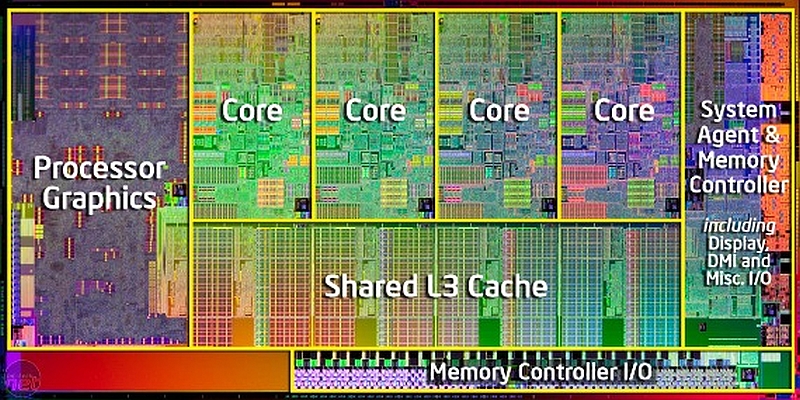
As we get into our discussions of hardware, we learn that there is a lot that goes on inside our machines that we aren’t normally aware of. We saw in class on Friday the picture of the inside of an Intel Core-i7 processor, saw the different cores, cache memory and registers that were inside the CPU itself, and started to learn about memory including RAM and ROM.
If you would like to see some details about what is actually going on inside your machine as it pertains to all we’ve discussed so far, you can download a very useful tool known as CPU-Z.
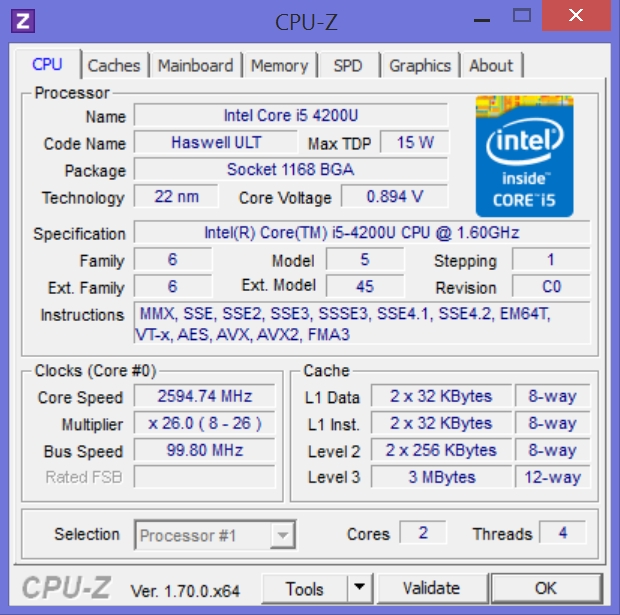
CPU-Z can be downloaded free of charge from the previous link, and it provides a ton of information about your processor and memory and gives a good example of what we’ve been talking about in class. To illustrate some of it, we’ll begin with the screenshot below:
You can see it starts off by indicating the model of processor I’m using, in this case the Intel Core-i5. You’ll recall we very briefly mentioned the Thermal Design Power, or TDP, which is (among other things) the amount of thermal energy a cooling system needs to dissipate, and in the image above you can see it is 15 watts, which isn’t bad for a mobile processor. Some high-power devices can have a TDP of over 200 watts.
It even shows that it is using the 22 nanometer architecture and that it uses something known as a BGA, or Ball Grid Array, in which the CPU is attached directly to the motherboard as opposed to using a socket like we saw in class. Socketed CPUs are either the older PGA, or Pin Grid Array, in which the CPU has pins that are plugged into holes in the socket, or the more modern and common LGA, or Land Grid Array, in which the CPU has metal contacts, or Lands, and they attach to tiny pins on the motherboard socket.
You’ll notice towards the bottom it has a header that says ‘Clocks,’ and you’ll remember our discussion of clock ticks and clock speed where we discussed the electronic pulses the system clock emits. In the window above, it shows that the clock speed of this system is 2595 Megahertz (Mhz), which translates to 2.6 Gigahertz (Ghz). So this is a 2.6Ghz system.
You can also see it shows the amount of level 1 (fastest), level 2 (next fastest), and level 3 (slowest and shared among all cores) cache memory, the memory we talked about that is built right into the CPU. It even divides up the level 1 cache into the sections used for program data and for instructions it is interpreting.
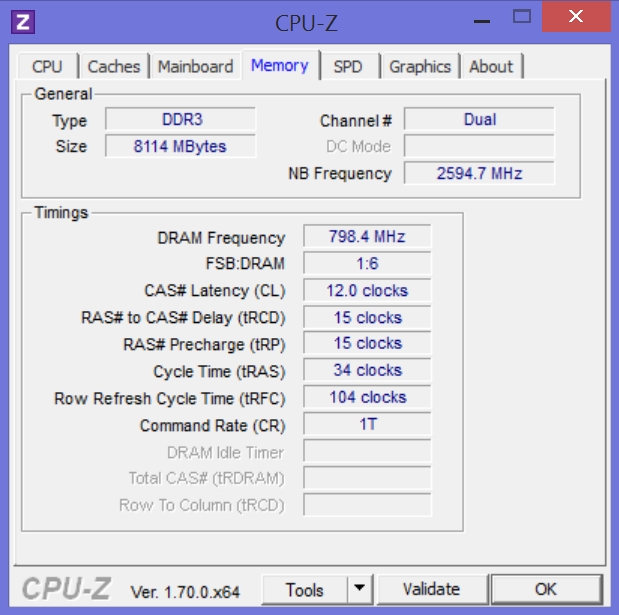
Let’s look at another screen:
In the image above, we see that this machine has DDR (Double Data Rate) RAM, and the ‘3’ is simply the improvement over DDR2, with 3 being faster and using less power. And yes, there is DDR4 memory as well. Back to the screenshot, you can see there is 8000 Megabytes of that DDR3 RAM, which translates to 8 Gigabytes, and relating back to our discussion of clock ticks and clock speed, you’ll notice it indicates something known as “CAS Latency.” CAS stands for Column Address Strobe, and it is the number of clock ticks between when a request of data is made of memory by the CPU, and when the data is actually delivered. So in this case 12 clock ticks will happen before the data can travel from memory to the CPU to be used.
One additional point while I’m at it: When we think of RAM, we’re thinking of what’s more technically known as DRAM, or Dynamic Random Access Memory. Dynamic means it occasionally needs to be refreshed in order to maintain the data that it’s holding. SRAM, or Static Random Access Memory does not need to be refreshed, and that is the type of memory used for the cache and registers inside the CPU itself. Since DRAM needs to be refreshed, you can see in the window above it tells us how often that refresh happens, in this case almost 800Mhz.
This is all on a mobile device, almost a tablet. Try running it on your own PC, whether desktop or laptop, and see what you can learn about the internals of your CPU and memory.