Tag Archives: Security
My first-ever blog post from a plane!

Or maybe not.
There was no way I could pass up the opportunity. Not only am I making this post while in the air over…well, somewhere, (UPDATE: I’m not!) I’m going to use it to tell you a little about how exactly in-flight WiFi works, or doesn’t, what the complexities are, and where it’s expected to go in the future.
The service, or more accurately the idea, is nifty, but there are some major, and I do mean majorly major, caveats. Frankly, and I’ll say this again, it’s so slow I just couldn’t post this from the plane. Failed uploads, 404 errors, and dropped connections, and it didn’t get any better once I arrived at the hotel. Before I get to all of it, here are some screens showing the fun things you can do with in-flight wi-fi, and learn why you should always be careful on public networks.
Bad USB!

First off, my apologies for the late post. I spent all day recording the lecture for the week I’ll be gone, and it turned out to be much more involved than I had anticipated. I think it ultimately came out all right, but it took about six and a half hours.
So we’ll see how it goes, in the meantime here’s a late post.
There was, earlier this year, the revelation that every single one of the billions of USB devices out there has a fatal flaw in its firmware, in which a malicious user or hacker could reprogram it to fool the machine into which it is plugged that it is some other type of device. In other words, it may be a thumb drive, but its firmware could be reprogrammed to fool a PC into thinking it’s a keyboard, which would then allow it to send keypresses to the host machine and a malicious user to then get the host to carry out malicious tasks. The flaw is known as BadUSB.
New technology brings new, serious security concerns
Technology, and its advancement, is a great thing. With every passing moment, some new development is announced that will make our lives, and ourselves, better, or faster, or more efficient, or healthier, or more accessible, or a host of other things that make everything we do better.
The problem is, there are always people out there who want to exploit that technology for their own gain, their own end, or their own purpose. And now, although it’s been a concern for quite some time, it has now been predicted that the first ‘Online Murder’ will happen by the end of the year.
The FBI’s facial recognition system comes online
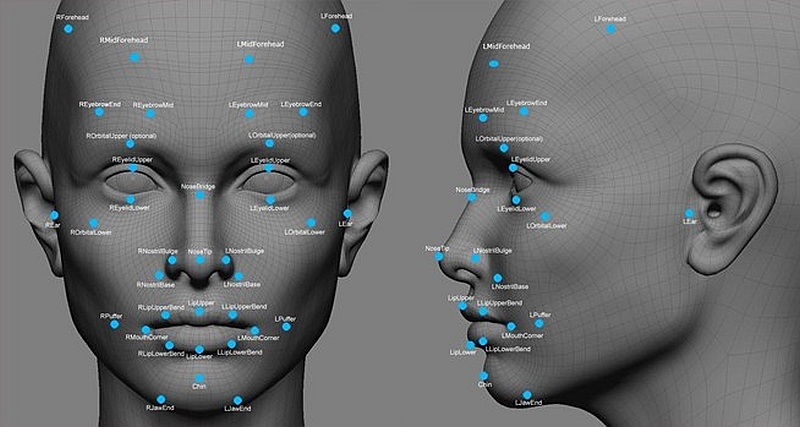
Privacy and security come up a lot with technology, and if you’re the suspicious type, something may seem awfully suspicious about this. The FBI has announced “Full Operational Capability” of it’s Next Generation Identification (NGI) system, which has been in development for three years and serves as an umbrella biometric identification system that will incorporate facial recognition and fingerprint identification capabilities along with things like voice prints sand other abilities.
For the fingerprint aspect of the system, NGI will be replacing the bureau’s current Integrated Automated Fingerprint identification System (IAFIS), which no one seems to mind. It’s the new facial recognition capabilities that have people riled up.
This new facial recognition component, the Interstate Photo System, is intended to treat faces like fingerprints; using automated software to scan photos of people and match the face in a photograph to a face already in the database. In other words, just like with fingerprints, if law enforcement has a photo of someone, they can compare it to the images in their database of faces, and the system will return 50 likely candidates. The database is expected to have over 50 million faces by next year.
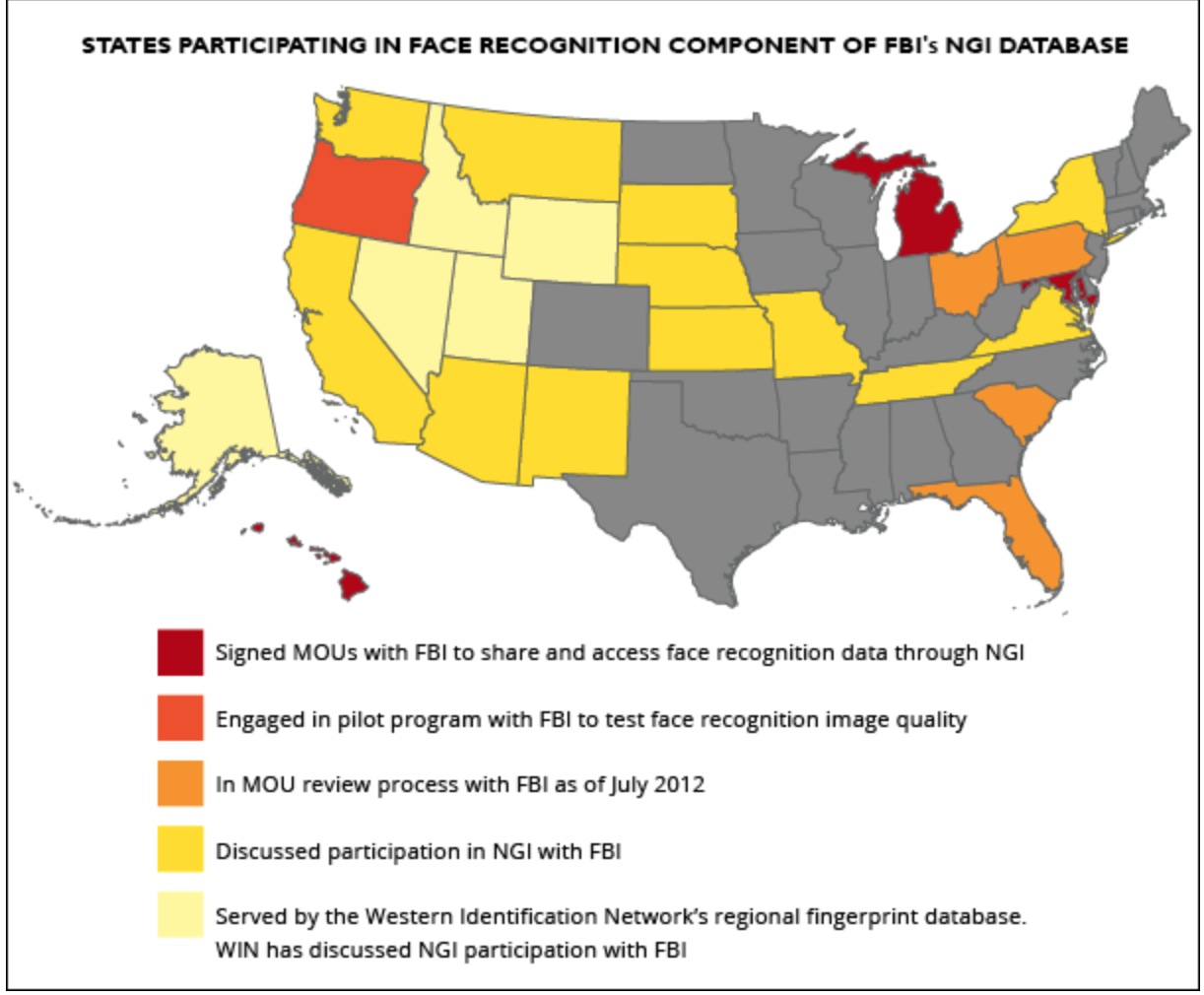
Many states are already participating in the program, as can be seen in the map below. MOU, in the legend, means ‘Memorandum of Understanding,’ which is simply an agreement on an ideal between two parties, it indicates they are on the same page about something.
It has been decried, of course, by many groups including the main anti-monitoring group the Electronic Frontier Foundation, which is often at odds with government at all levels for their surveillance and monitoring practices. The big issue is the possibility of false positives, or accuracy in general, which is the main issue the EFF takes. From reports, of the 50 faces returned, there is an 80 percent probability that the actual matching face will be returned in the results. However, the system has already had success and I suspect will continue to expand rapidly in practice.
This is a sensitive subject, so let me make a couple of comments: First, as we have already said on this site, privacy and security are mutually exclusive. If you want one, you give up some of the other. You can’t have complete privacy and complete security. In this day and age, with what is happening in the world, the balance of one versus the other is a seemingly impossible judgement.
Also, Facebook and Apple have been using facial recognition for years and no one seemed to mind. In fact, here in Las Vegas s have been using it for YEARS for essentially – but not quite – the same purpose the FBI now claims and we’ve been ok with it. Priorities, I suppose.
You can see an unclassified PowerPoint presentation about the system that has a few additional details at this link.
The Nevada DMV’s unusual password requirements

I occasionally share personal experiences on this site when I feel they are of relevance to the class and deal with material we have covered or will cover in the future, but it has to be something of significant consequence for me to break that fourth wall.
As an example, I have trouble with websites all the time. They don’t load, they give me 404/page not found errors, they don’t load properly, but that happens and I don’t chronicle every experience here on the class page. No, it has to be something exceptional if I’m going to tell everyone about it, and this time it’s the DMV that gets to be the target. I had one of the most curious experiences on their website recently, and I think it warrants a post.
I wanted to renew my license online, seeing as going to the DMV is one of the most despised experiences one can have. To be fair, the last time I went to the DMV to take care of a pretty serious issue (expired registration), it was smooth sailing – I was in and out, including getting the car smogged, having it inspected, and getting my new registration all within about two hours. Not too terrible.
Even so, I was interested in trying out their not-terribly-new online functionality, but it turns out while going to the actual, physical DMV might be getting better, going online to the DMV is getting worse, at least in this case.
Before I get into it all, I must say their website is far, FAR improved from what it used to be, which was a cluttered mess of links reminiscent of the early days of Yahoo. Yet when it came to renewing my license there were two serious problems: The draconian password requirements, and the fact that the system didn’t tell me what I actually needed to do.
First, the recent celebrity hacking scandal has everyone fired up about password strength, and I’ve even heard a couple of TV commentators saying it reinforces how important it is to have complex, difficult passwords. That’s true to a point, and we’ll talk about that later in the session, but it’s certainly better than an easy-to-crack password.
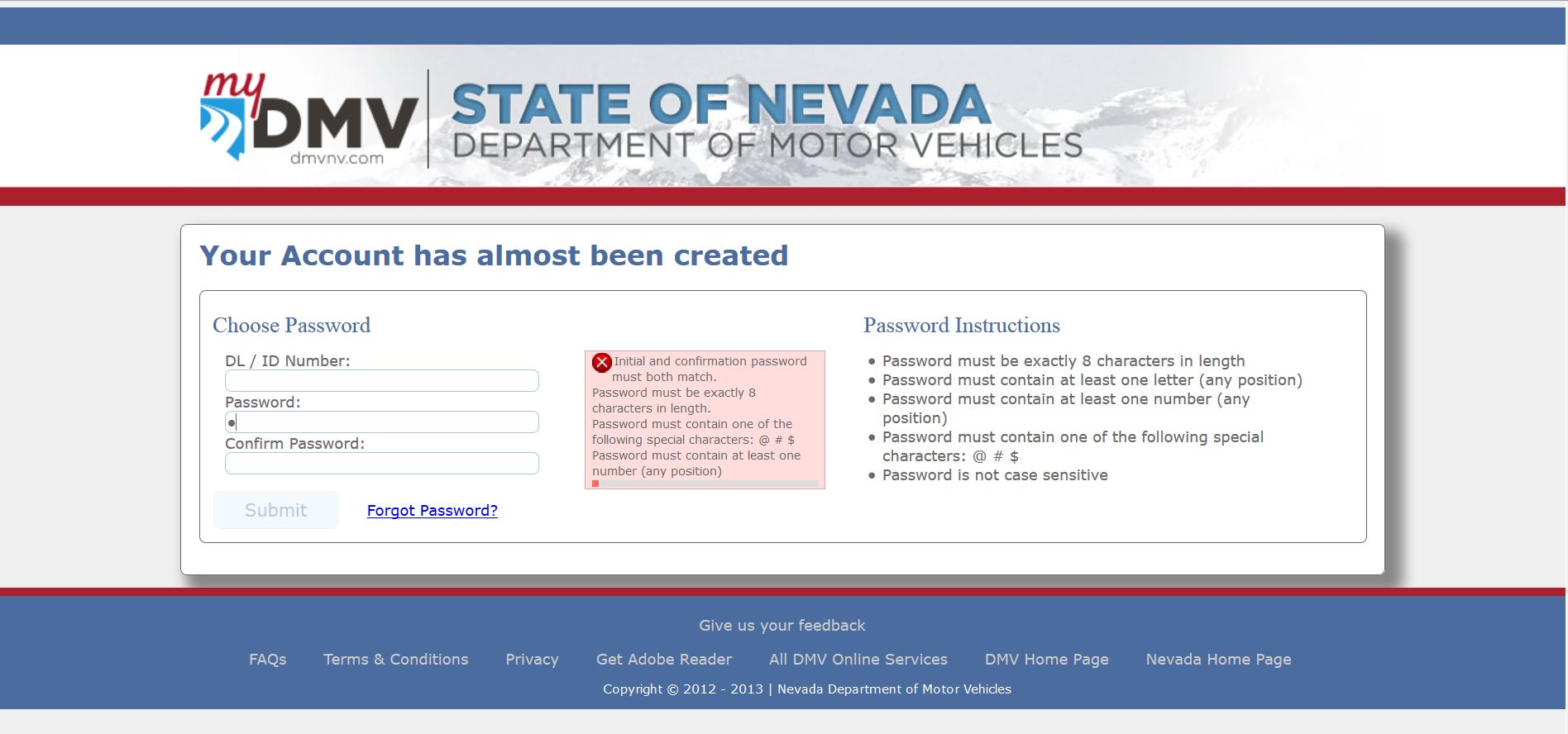
But in order to have that, you have to let people create them in the first place. The Nevada DMV does exactly the opposite. In what can only be described as an absolutely bizarre set of password requirements, it imposes restrictions that for the life of me I can’t begin to understand. In all my years of being involved in this industry, it is, without a doubt, the weirdest set of limitations I’ve ever seen. Here’s a shot of the webpage, and I’ll walk through it afterwards:
First, for what possible reason would you limit the length someone can make their password? The DMV isn’t big enough to argue it would be a storage or maintenance issue, and everyone knows that a longer password is more secure than a shorter one. This is no secret, it’s common knowledge. There are other issues of course, some of which we’ll talk about in this post and others we’ll talk about in class, but a basic rule is longer is better.
Next, they require at least one letter, but notice at the bottom it says “Password is not case sensitive.” What? Having case sensitive passwords (meaning the capitalization of letters in the password matters. For example, a lower-case ‘z’ could not be used in place of an upper-case ‘Z’) makes the passwords more unique, more complex, more difficult to crack, and like the length requirement above is very well known. Why they would limit the length and make them not case-sensitive is beyond me. You can read here about a bank that did the same thing and the response from the author and most commenters is of understandable incredulity.
They require a number, which is fine and a sensible requirement, but right after that they indicate you can only use one of three special characters: @, #, or $. No asterisk, no parens, no ampersand, just those three. As was the case with the previous restrictions I ask the same question again: Why? Why would you limit the types of special characters that can be used when just like before it is common knowledge that they contribute to the complexity of a password?
The whole experience was so strange, and frankly trying to create a password that met these requirements was very difficult, which of course means I’d have to write it down making the whole thing less secure. Unbelievable. Whoever decided on this needs to be strategically reassigned.
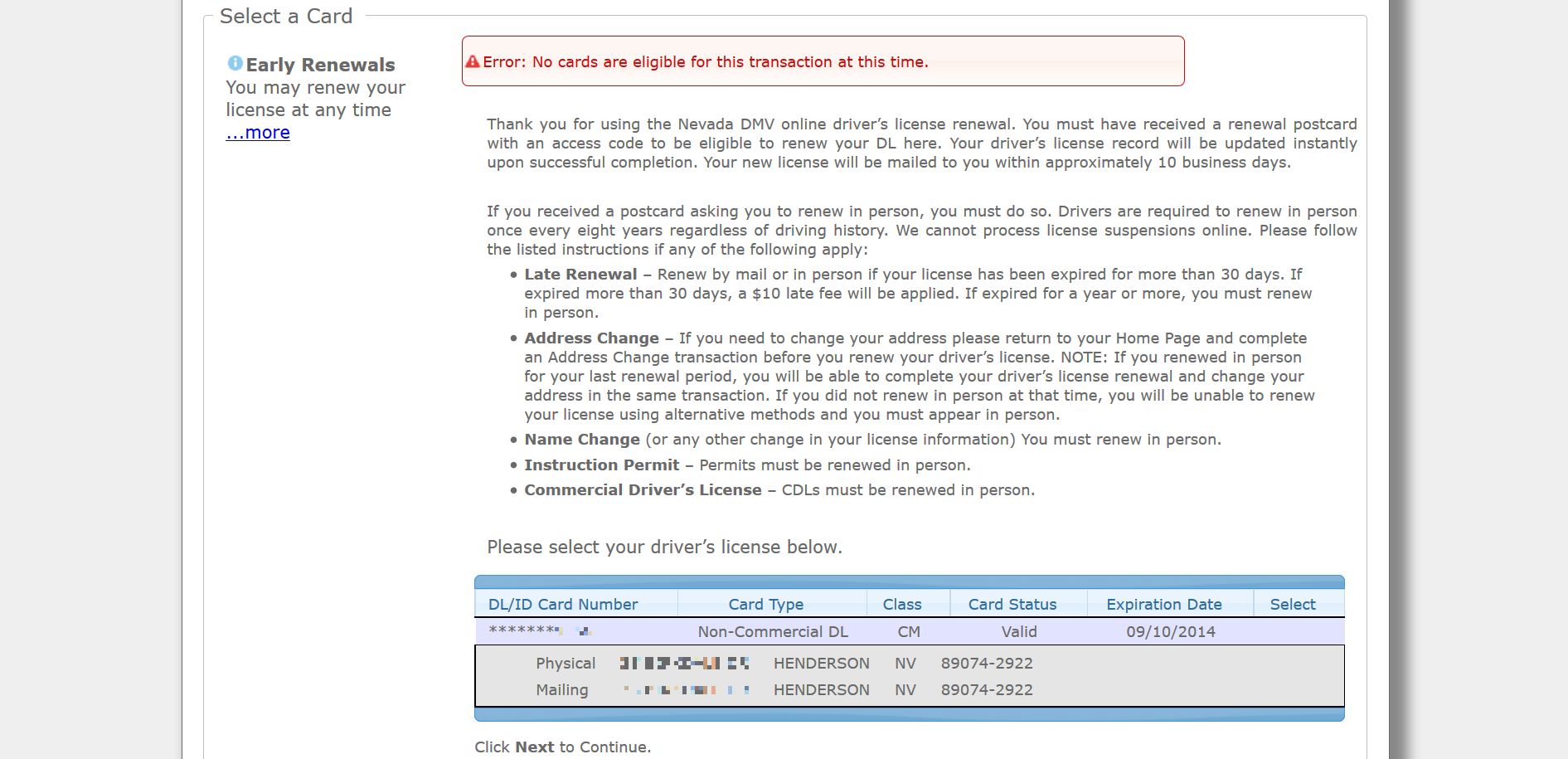
Of course, after finally getting through it all, I was presented with this screen:
Yes, even though I have had the card telling me my license will expire next week sitting on the table for a month, apparently the system that put me through the hell of its password requirements didn’t recognize I actually needed to renew my license in person. Instead, it simply said I had no cards that needed renewal. You can see it says “Click Next to Continue,” and although it’s cut off in the image there was no ‘Next’ to click, only a “Cancel” button. All that for…that. Apparently I have to go in because I need to have my picture taken, which based on my current picture is fine with me.
This was a password creation and system failure of epic proportions, and it shows me that something is seriously wrong over there. The system should not impose such limits on password requirements, and it should be aware I have to go in to renew my license because of the picture and tell me as much.
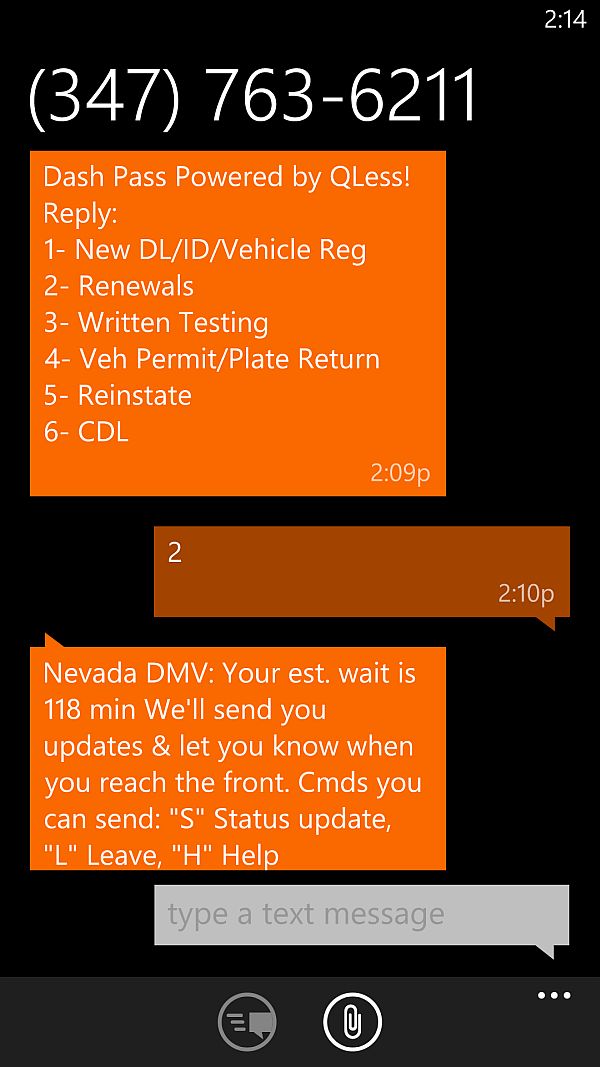
Having gone through all of this, however, there is something for which I must give them significant credit, that being the option they provide of simply texting ‘dmvhenderson’ (for the American Pacific location) to 347.763.6211, and they text you back a menu of options from which you can choose. You text them your choice, and they automatically place you in line for that function, providing you updates on your wait, your place in line, and how many people are ahead of you without you having to actually be there. They also provide the option for you to text them back for updates or to cancel, and you can even text them that you need more time. Very, very nifty. A screenshot of the texts that I received is below.
How to protect yourself from viruses

Well, not you, you know, but rather your digital devices. It came up in class and I was asked again by a few of you as to what programs are available to guard against malware that might infect your machine, so I thought would offer some suggestions.
First, I advise against paid services for your home machines, especially Norton/MacAfee/Symantec. There are many free alternatives that work very well, while those big ones and their ilk are dilettantes, wanting to protect your machine and monitor ports and watch incoming/outgoing traffic and monitor webapges and it ends up using a ton of computing resources and they’re difficult to uninstall, leaving traces of themselves all over your hard drive and registry. The free options have paid versions, but as an individual user you don’t need them, and their virus definitions, which allow them to recognize viruses, are updated just as often.
Also, please be aware that any digital device can be infected with malware, and for those who think Macs are immune I have some bad news for you as well.
Having gotten that out of the way, I have provided some alternatives below. Keep in mind that each of these offers strong virus protection, but their features beyond that are usually pretty comparable, such as HTTP scanning to protect you against visiting malicious webpages, and real-time system monitoring. You also want to be sure the virus definitions are always up-to-date, and in fact right after installation of any of these that’s the first thing that will happen, then set them to update automatically. Ultimately, the one that is best for you depends on what you need and what you want.
One final thing, absolutely do not run more than one simultaneously! Not only will it unnecessarily tax your system resources, they’ll try to scan each other interfering with their ability to perform their tasks and possibly providing false positives.
And now, your choices!
AVG has been around for a long time, and they recently updated their interface to bring it more in line with modern design trends. Their malware detection and removal is effective, it actively monitors your system and your browsing (it even claims to monitor your Facebook browsing), and it has been around for a long time. They have a free version for individual users which can be downloaded from the link provided above.
Bitdefender (PC)
Bitdefender is another stalwart product that has been around for quite some time and is quite popular as an antivirus tool as well. They have also expanded their capabilities, and according to their webpage they will even monitor for rootkits, which are subversive programs that let people access your machine, and it even claims it can determine unknown threats based on how regular programs are supposed to work. Either way, it has been long-trusted as an anti-virus program.
AVAST has been around, in one form or another, longer than all the others. While it’s antivirus capabilities are very strong, there are some opt-ins during installation you want to watch out for; it’s best to choose a custom installation and un-check anything you don’t want. Strictly speaking as an antivirus service, it works very well.
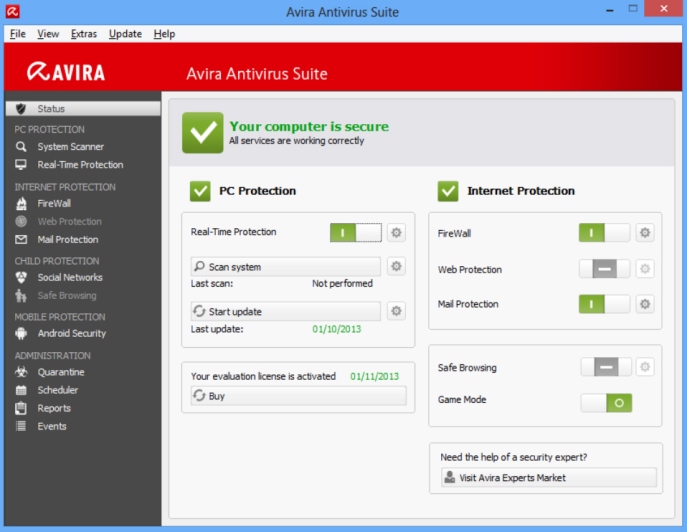
Avira (PC / Mac / Android / iOS)
Although you don’t hear the name Avira all that much, it has been around since the 80’s and is very highly regarded as an antivirus program. It has a small footprint, smaller than most of the others even, meaning it uses less resources (generally) than many of its competitors yet still offers a full suite of protection options. I personally don’t have as much experience with this one as much as the others, so if you’re the experimenting type you can let us know how it worked for you!
Windows Defender (PC, obviously)
Windows Defender is a new program in the grand scheme of things, only becoming available for the first time with Windows Vista, however if you have Windows it’s likely all you need. It can be activated/deactivated from the ‘Action Center’ under ‘System’ settings in the Windows Control Panel. Surprisingly enough, it works very well and is as effective as the other programs I’ve listed, but it doesn’t provide any feedback or too much interaction, while the other programs listed provide a lot of information, detail, and hands-on control.
Malwarebytes AntiMalware (PC)
Very well known, well respected, and well trusted, Malwarebytes Antimalware is an anti-malware program, however the free version needs to be run manually. In other words, while all the others offer real-time monitoring, this one doesn’t, you have to run a scan deliberately. However, it is so well regarded that many people do a once-a-week scan using Antimalware, in addition to their regular protection with one of the others.
That’s all I have for now. Although it’s just a list with some brief comparisons and explanations, hopefully it provides a starting point. Remember, whichever you use is really a personal choice; they’re all comparable and it depends on which one you feel the most comfortable with. Experiment (but don’t use two at once!) and see what you think. The more security becomes an issue, the more you will need this type of thing.
Be sure to do an initial deep scan once you’ve installed your choice!
Federal websites don’t screw around

This won’t be a very long post, I just wanted to show all of you that the federal government wants to be very clear in your expectations of privacy when using their websites. It also fits perfectly with the discussion of security and privacy we’ll be having tomorrow (or today, depending on when you see this). I was recently using the IRS.gov site when I was presented with this window:
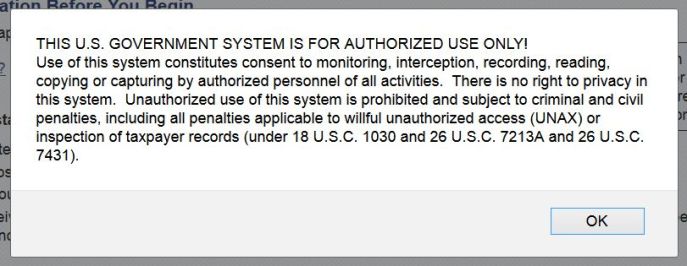 It almost sounds scary, but to be fair it’s no secret this happens. It happens on most websites, actually, government or not. Their wording sounds Orwellian and apocalyptic, but it’s par for the course when conducting business online. I actually don’t have a problem with it, you can’t have 100% privacy and also have 100% security, you have to make sacrifices in one to have any amount of the other. Even so, the wording is so forceful it gave me pause. Maybe I should have used my real name instead of the pseudonym “Gleeson McNasty.”
It almost sounds scary, but to be fair it’s no secret this happens. It happens on most websites, actually, government or not. Their wording sounds Orwellian and apocalyptic, but it’s par for the course when conducting business online. I actually don’t have a problem with it, you can’t have 100% privacy and also have 100% security, you have to make sacrifices in one to have any amount of the other. Even so, the wording is so forceful it gave me pause. Maybe I should have used my real name instead of the pseudonym “Gleeson McNasty.”
A very useful, and very unnerving, webpage
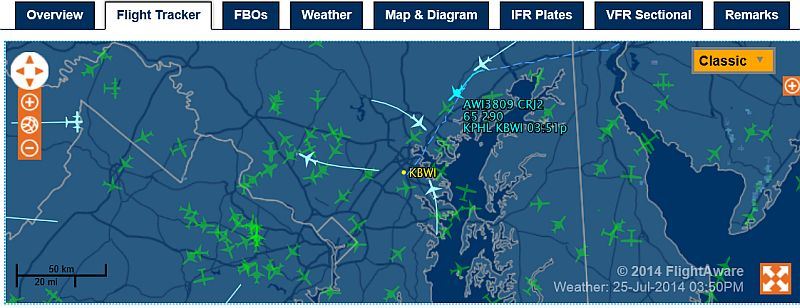
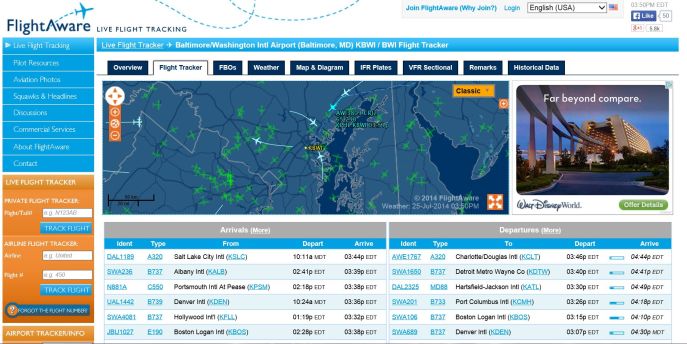
Last week, I was sent a link to a website that was at once fascinating and informative, and at the same time unnerving. Allwyn alerted me to flightaware.com, a website that allows you to track all planes in the air, their airports, their origins and destinations, and a multitude of other factors. As you can see form the homescreen below, there are a re a ton of things you can do, from tracking airlines, to checking airport status, to determining arrival, departure, and current locations of flight, to checking the weather, and a ton of others.
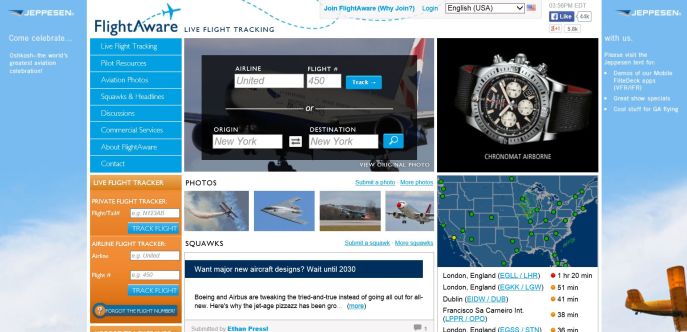 I thought I would give it a run with the airport of my adopted hometown, Baltimore-Washington International (BWI) in Baltimore, Maryland. Massive international hub that it is, it can’t be seen on the small national map on the right unless you zoom in, and I’m ok with that. That map also shows real-time storm tracking – very impressive.
I thought I would give it a run with the airport of my adopted hometown, Baltimore-Washington International (BWI) in Baltimore, Maryland. Massive international hub that it is, it can’t be seen on the small national map on the right unless you zoom in, and I’m ok with that. That map also shows real-time storm tracking – very impressive.
I clicked on ‘Live Flight Tracking,’ then ‘Browse by Airport’ (although you can also browse by flight, by aircraft type, and by operator among others), and entered ‘BWI’ into the search box. I was greeted with the following screen, that shows all flights currently inbound and outbound from the airport.
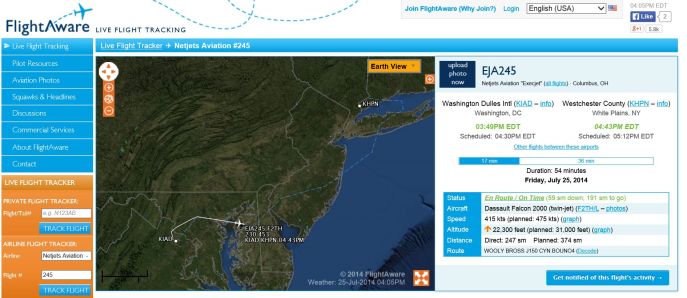
An earth-view that shows terrain is available, even infrared views! Hovering the mouse over an airplane icon shows information about that airline, and if you click on it you will be taken to a page that gives further information, including its starting point and departure time, the type of plane it is, its current and final altitude, as well as its destination and estimated arrival time (screen below). Not only that, the planes’ positions are updated in real time, so they are all slowly moving across the screen as you watch.
There is a lot you can do, and while this is easily one of the most amazingly useful and informative sites I’ve ever seen, it also fills me with unease. This year has been one of the most deadly in aviation history, and although the contributors to that have been overseas in hostile territories, and even considering air travel is still the safest means of travel by far, but if we can have mapping services that can tell someone how to drive directly to your house, perhaps this isn’t so bad after all, and nothing has happened as a direct result of it. To be fair, none of tit is classified information, you can get the same information by visiting an airport/airline website or calling their number. Which means I could see myself really using this site.
Who is on your wifi?
We talked extensively in class about networking, and only a little about WiFi specifically, however your WiFi setup leaves a lot of security holes, even if you have security in place (you did set a WEP, or even better a WPA or equivalent, right?).
There is a well-known activity known as wardriving, in which someone drives around a neighborhood or commercial district looking for a WiFi signal to leech off of. The problem is, if someone manages to attach to your network they have access to your whole system, even if they don’t exploit that.
If you’re interested in seeing all the devices attached to your wireless network at any given time, you’ll want to head over to whoisonmywifi.com and download their eponymous program. After set up, you will have to do a couple of network scans, after which it will show you what devices are connected to your network. If you know the device, you can set it to ‘known,’ otherwise you’ll have to do some investigation. A screenshot of my network is below:
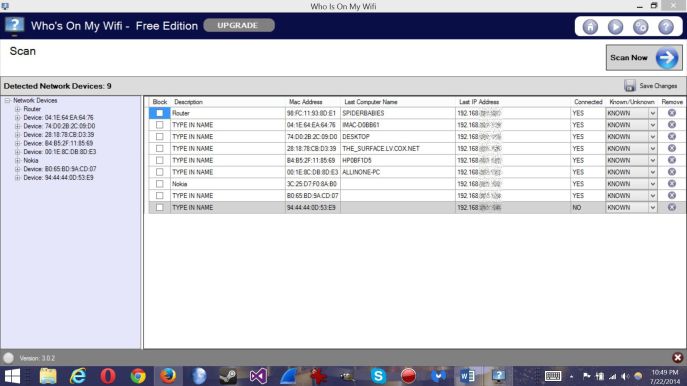 You can see from the scan that my router runs the network with the name of that network (SPIDERBABIES), along with its MAC address and associated IP. The MAC, or Media Access Control address is a unique address assigned to every piece of hardware for identification on a local network, and it’s one of the ways a device checks whether or not a packet is in the right place or not. You can also see it looks very similar to an IPv6 address as we talked about in class (please read the link, it thoroughly explains IPv6 and why we need it).
You can see from the scan that my router runs the network with the name of that network (SPIDERBABIES), along with its MAC address and associated IP. The MAC, or Media Access Control address is a unique address assigned to every piece of hardware for identification on a local network, and it’s one of the ways a device checks whether or not a packet is in the right place or not. You can also see it looks very similar to an IPv6 address as we talked about in class (please read the link, it thoroughly explains IPv6 and why we need it).
There is also an iMac, a Surface, a Nokia phone, a Dell desktop (ALLINONE-PC), my main media server (DESKTOP), and an HP printer. For things that aren’t named, it is very easy to determine what they are: If you copy and paste the MAC address, colons included, into a search engine it will tell you what manufacturer owns that code. It’s how I discovered the last entry is an LG smart TV I have upstairs.
But as I mentioned, if you can’t determine what a device is, you’ll need to find out. If you don’t recognize the device, or if the manufacturer isn’t one you own, you might want to consider blocking it, something you can also do from the results screen.
Below is a video that explains how it works and what it can do. Check your network!
Did Russian hackers almost bring down the nasdaq?

It has just been revealed that in 2010, Russian hackers, likely associated with the Russian government, and using using custom-designed malware to exploit zero-day vulnerabilities (something that should absolutely not be present in systems of this sort) were able to infiltrate the NASDAQs systems for the purposes of snooping around. However, it appears it also had the capabilities of delivering what is known as a ‘Logic Bomb;’ a destructive program that waits until a specific date occurs before it does its damage.
A destructive program destroying the internals of the NASDAQ’s servers would have wreaked havoc across the U.S. financial infrastructure, and the world’s as well. And it turns out that once the malware was discovered it appeared it could have wiped out the NASDAQ’s internals completely. So serious was it, that although no less than five separate federal security agencies had discovered the infiltration, they felt it had to be brought to the attention of the President.
 The investigation discovered that not only did these Russian hackers have access to the NASDAQ’s servers, but Chinese hackers did as well along with other unidentified intruders, and that the servers were very vulnerable to attack with one person referring to it as a swamp. Although the potential impacts were catastrophic, the NASDAQ never reported the attacks nor indicated their severity. Expanding on the investigation, it turns out most banks and large financial institutions were possessed of the same vulnerabilities.
The investigation discovered that not only did these Russian hackers have access to the NASDAQ’s servers, but Chinese hackers did as well along with other unidentified intruders, and that the servers were very vulnerable to attack with one person referring to it as a swamp. Although the potential impacts were catastrophic, the NASDAQ never reported the attacks nor indicated their severity. Expanding on the investigation, it turns out most banks and large financial institutions were possessed of the same vulnerabilities.
The scary part is that no conclusion was ever reached. Even the ultimate purpose of the intrusion is unclear; some say it was to do damage, some say it was just so the Russians could build an equivalent system. It also shows that we are not as far ahead as we often think in terms of security or technology; we still can’t definitively say it was actually the Russians. Great advances have been made since this event happened, but it’s a global race and it seems we’re still in no position to prevent it.