My first-ever blog post from a plane!

Or maybe not.
There was no way I could pass up the opportunity. Not only am I making this post while in the air over…well, somewhere, (UPDATE: I’m not!) I’m going to use it to tell you a little about how exactly in-flight WiFi works, or doesn’t, what the complexities are, and where it’s expected to go in the future.
The service, or more accurately the idea, is nifty, but there are some major, and I do mean majorly major, caveats. Frankly, and I’ll say this again, it’s so slow I just couldn’t post this from the plane. Failed uploads, 404 errors, and dropped connections, and it didn’t get any better once I arrived at the hotel. Before I get to all of it, here are some screens showing the fun things you can do with in-flight wi-fi, and learn why you should always be careful on public networks.
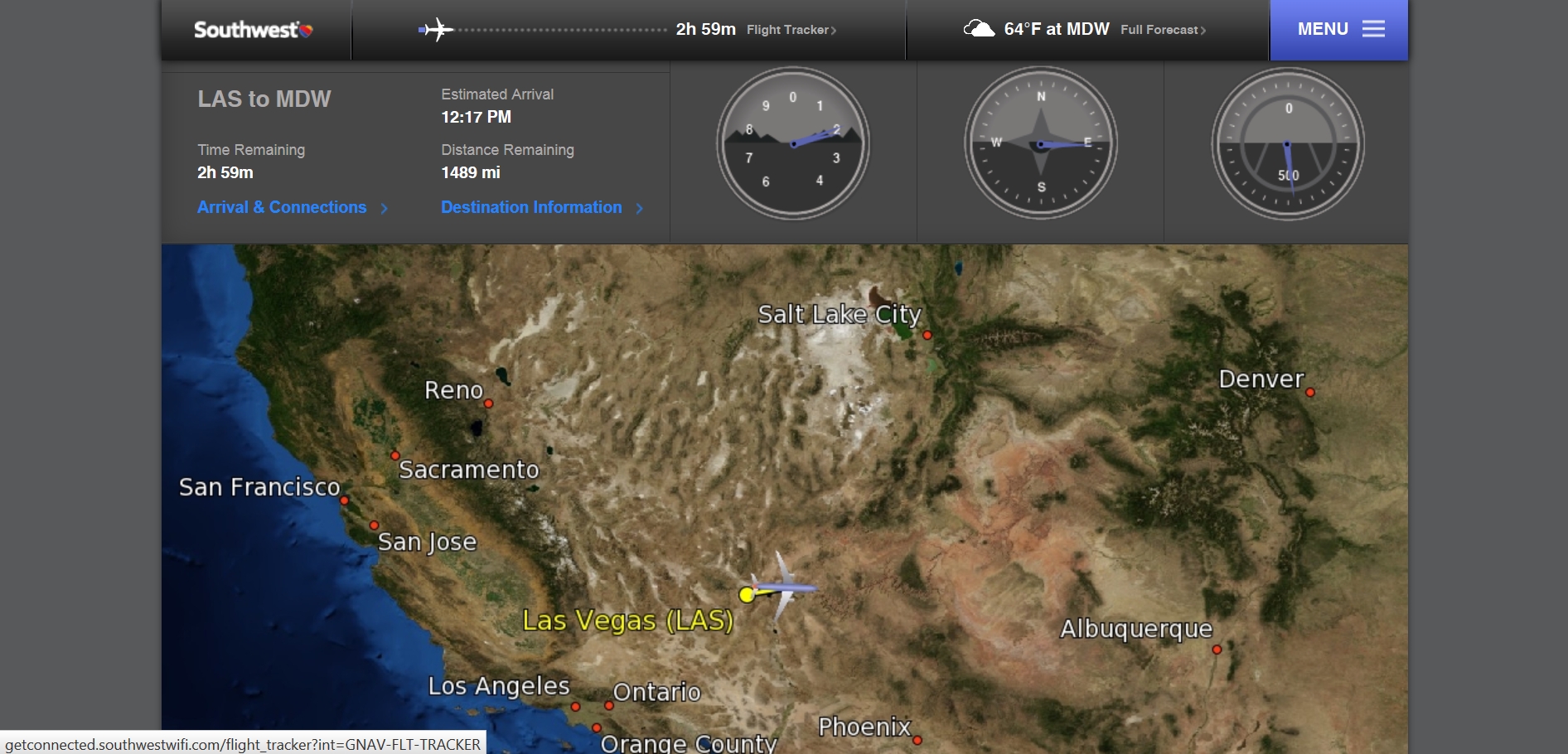
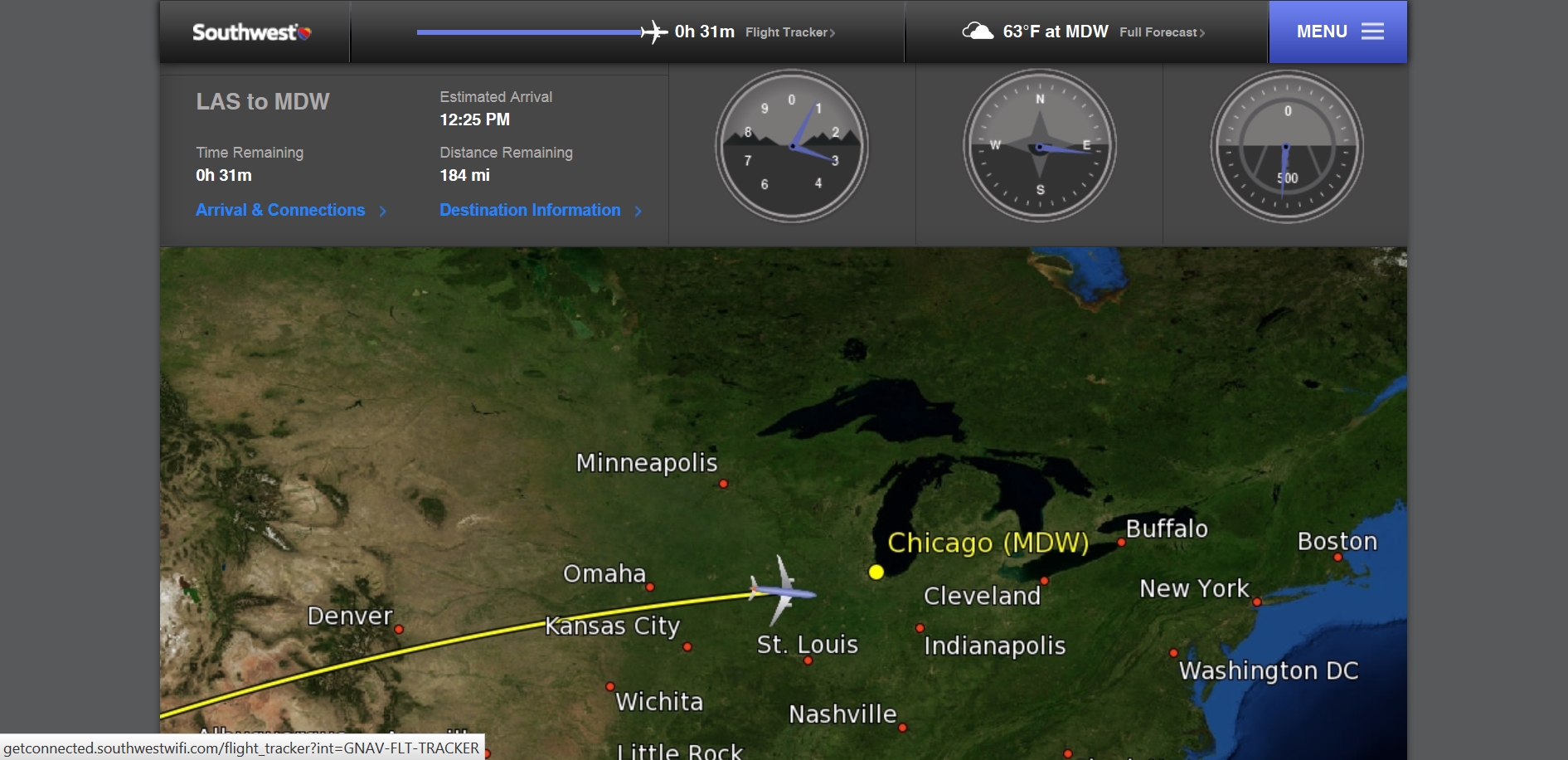
You can track where you are, along with some dials that are telling you…something:
Watch a gripping selection of live TV. To be fair, they had a moderately impressive lineup of channels, including things like Animal Planet, Cartoon Network, the Food channel, even the Golf Channel.
But I’d also like to use this as an opportunity to talk about privacy and security in a setting like this.
While it’s generally useless for any kind of involved on-line activity, within-the-plane browsing is another story, and I don’t necessarily mean that in a good way.
First, it’s slow. Grossly, disgustingly, putridly slow. Don’t believe it? I ran a speedtest on the network as we flew overhead, and measured what are easily the worst speeds in the history of anything ever. If you’ve actually watched paint dry, it was faster than this. This is what shared bandwidth looks like, people, and it renders anything you want to do online out of the question.
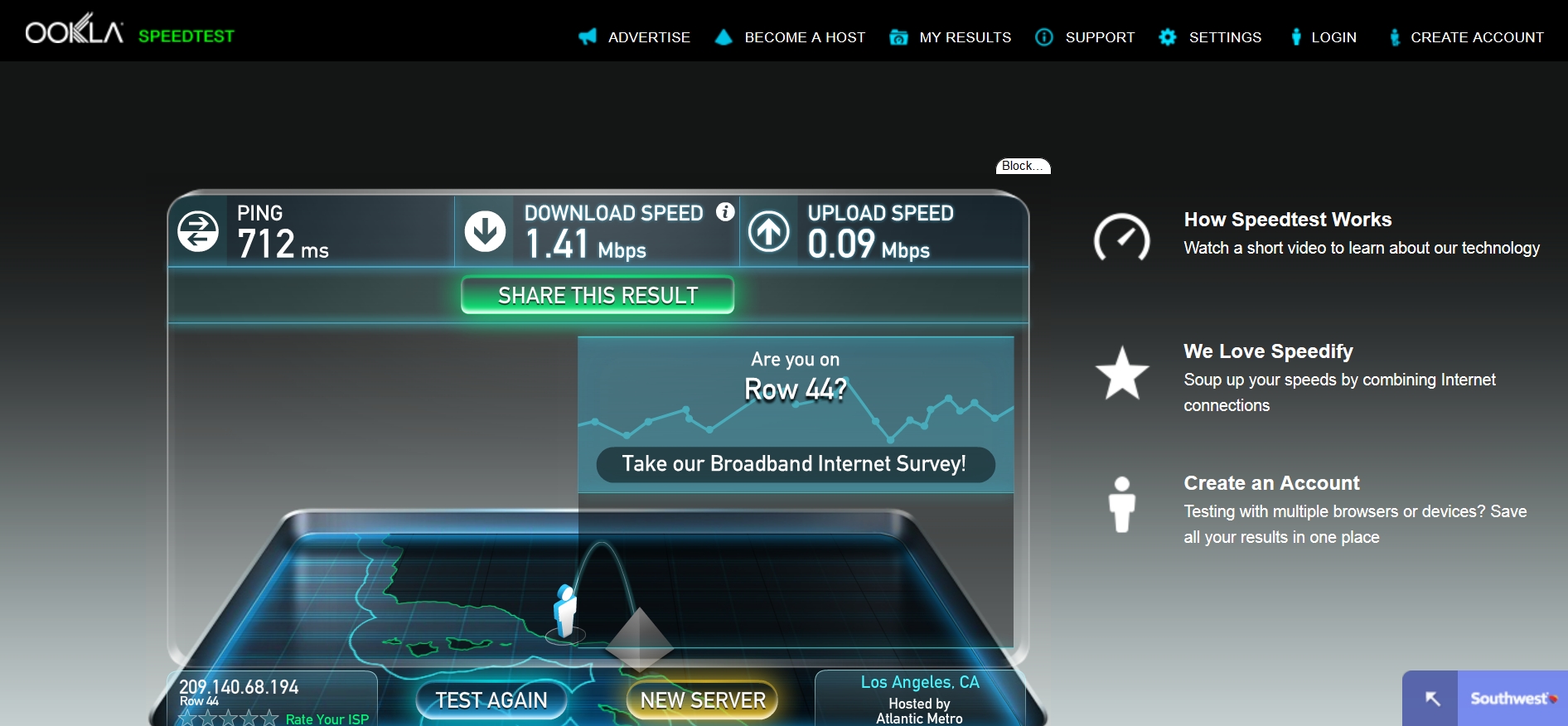 Absolutely atrocious. Note that is asks if I’m on “Row 44.” That will become important in a moment, and I should add that I even had this happen, which I have never seen before – this was a first.
Absolutely atrocious. Note that is asks if I’m on “Row 44.” That will become important in a moment, and I should add that I even had this happen, which I have never seen before – this was a first.
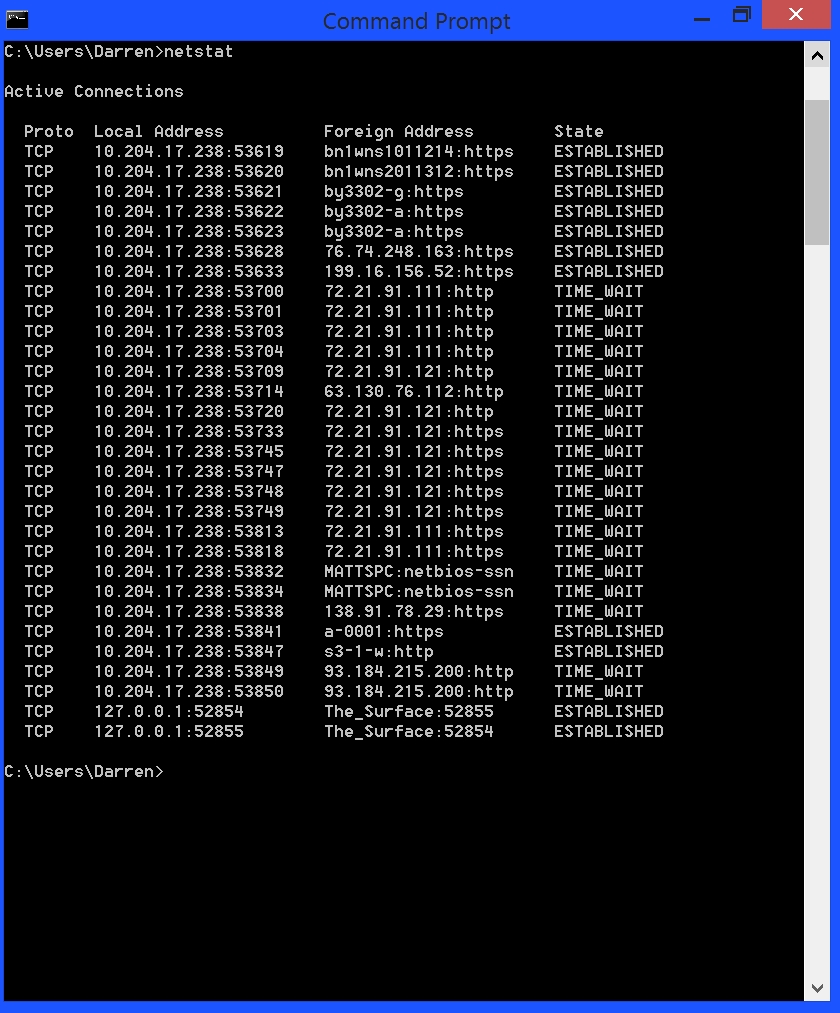
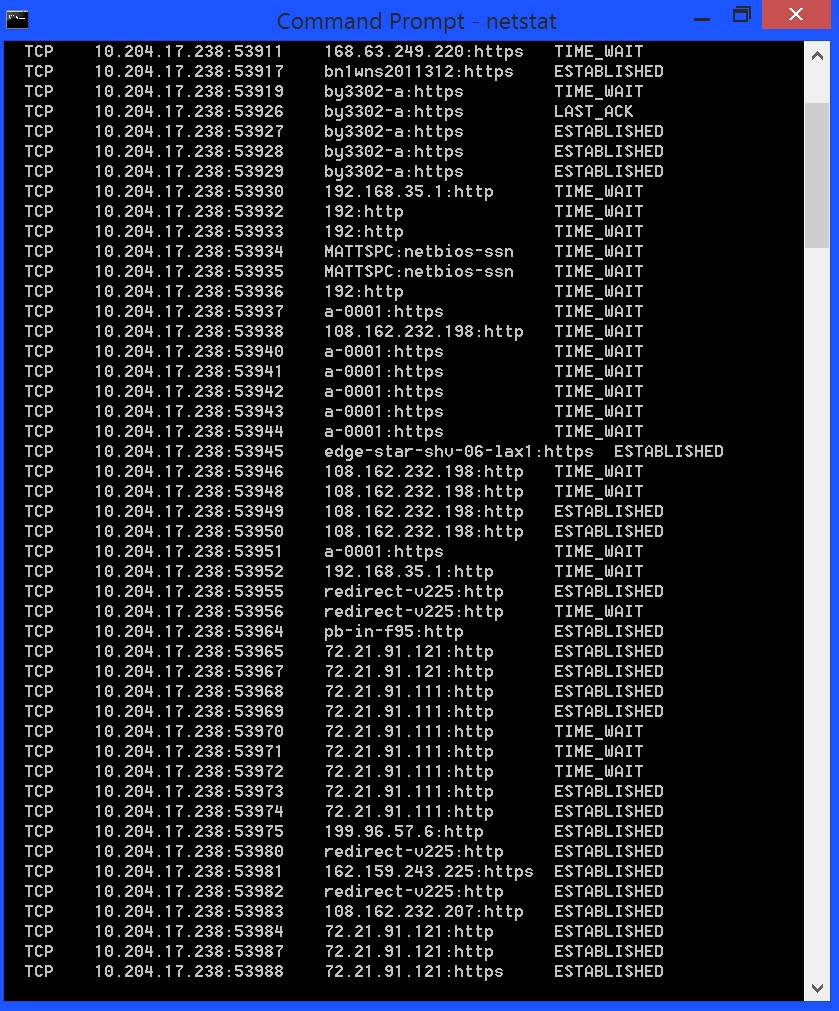
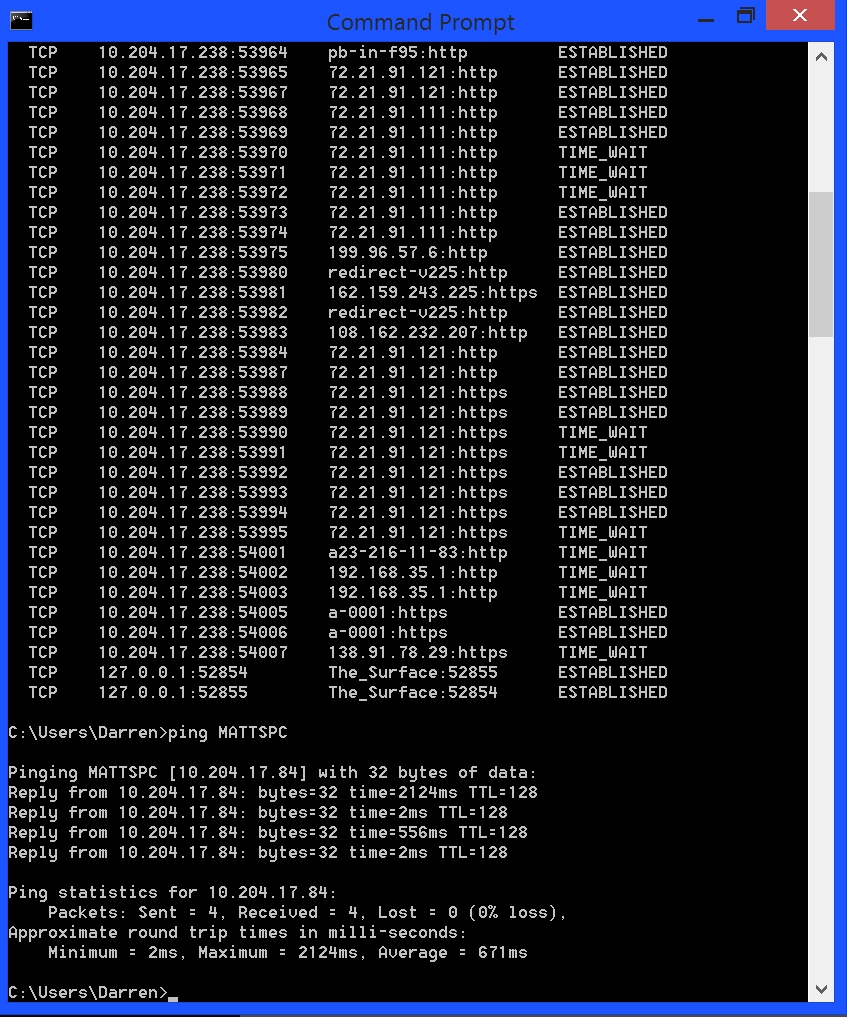
 I wanted to see what kind of security there was among the devices on the plane, so I used the “netstat” command at the command prompt to see the active connections to the network we were all using. As you can see in the first picture below there were a good number of them, but look how many more there were when I ran the command only a few minutes later, as shown in the second image below. The IP addresses in the second column are mainly the access point, with the specific port being used after the colon (for example, port 80 is the port used for HTTP. while 443 is the port used for HTTPS, so you can see some people were web browsing, others browsing secure sites. Both probably not such a good idea here). The destination address is in the third column.
I wanted to see what kind of security there was among the devices on the plane, so I used the “netstat” command at the command prompt to see the active connections to the network we were all using. As you can see in the first picture below there were a good number of them, but look how many more there were when I ran the command only a few minutes later, as shown in the second image below. The IP addresses in the second column are mainly the access point, with the specific port being used after the colon (for example, port 80 is the port used for HTTP. while 443 is the port used for HTTPS, so you can see some people were web browsing, others browsing secure sites. Both probably not such a good idea here). The destination address is in the third column.
If you notice about a third of the way down in those images there is a device with the name of MATTSPC. Very clever name, Matt. I chose it to be my test of what I could do on the network, if for no other reason than it screamed out to be used for that very purpose.
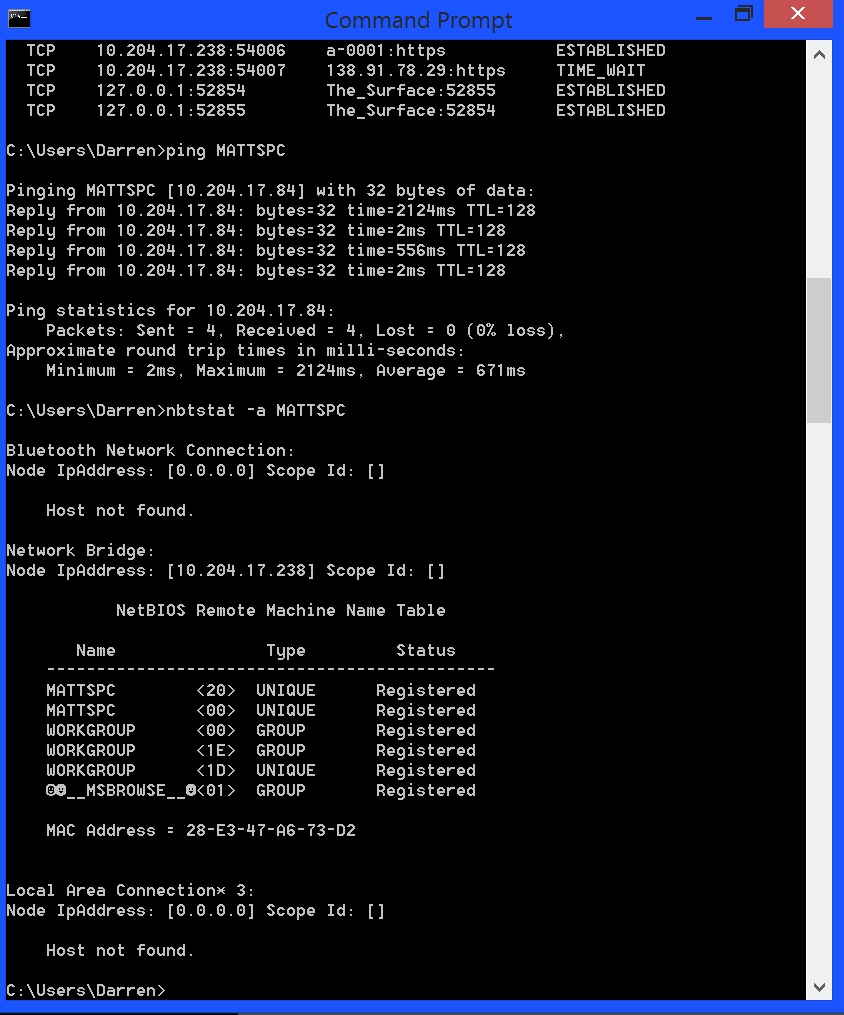
The very first thing I wanted to do was use the ‘ping’ command to see if I could communicate with MATTSPC. Pinging a device sends it a series of packets and returns some information about how long it took the packet to get there, and whether any were lost on the way. I ran the command as you can see in the next image, and what do you know, me and MATTSPC could communicate. That’s a grotesque average, and that maximum value is the highest I’ve ever recorded for a single ping.
Then, I wanted to see if he and I were considered to be on the same network since the netbios protocol was listed in his results from the netstat command. Lo and behold, we are all part of the same friendly workgroup. Good sign for me, not-so-good sign for him.
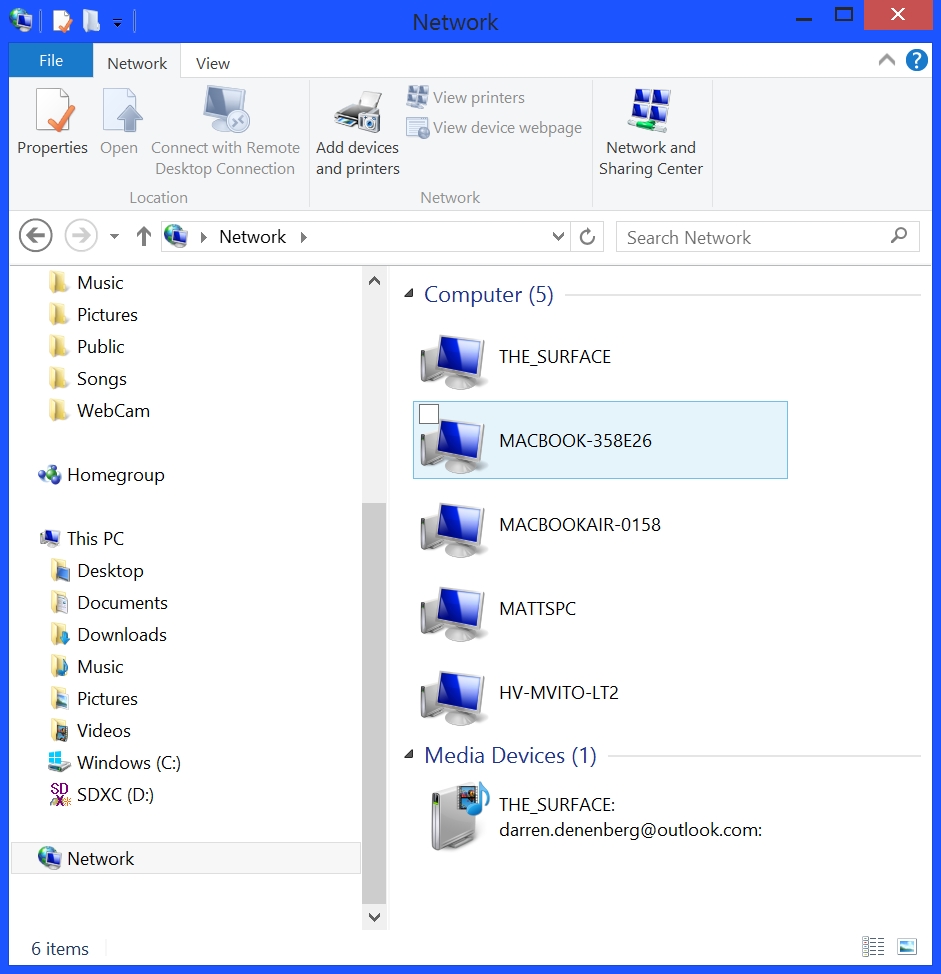
So now I had to do it. I had to see what other machines were on this group I was a part of. Connecting to this network joined us all together, so I went into Windows explorer, turned on device discovery, and LOOK WHAT I FOUND!
That’s right, all these devices (laptops, specifically) that other people were using must have had discovery turned on, because they all showed up right there in my own Windows explorer. It was time.
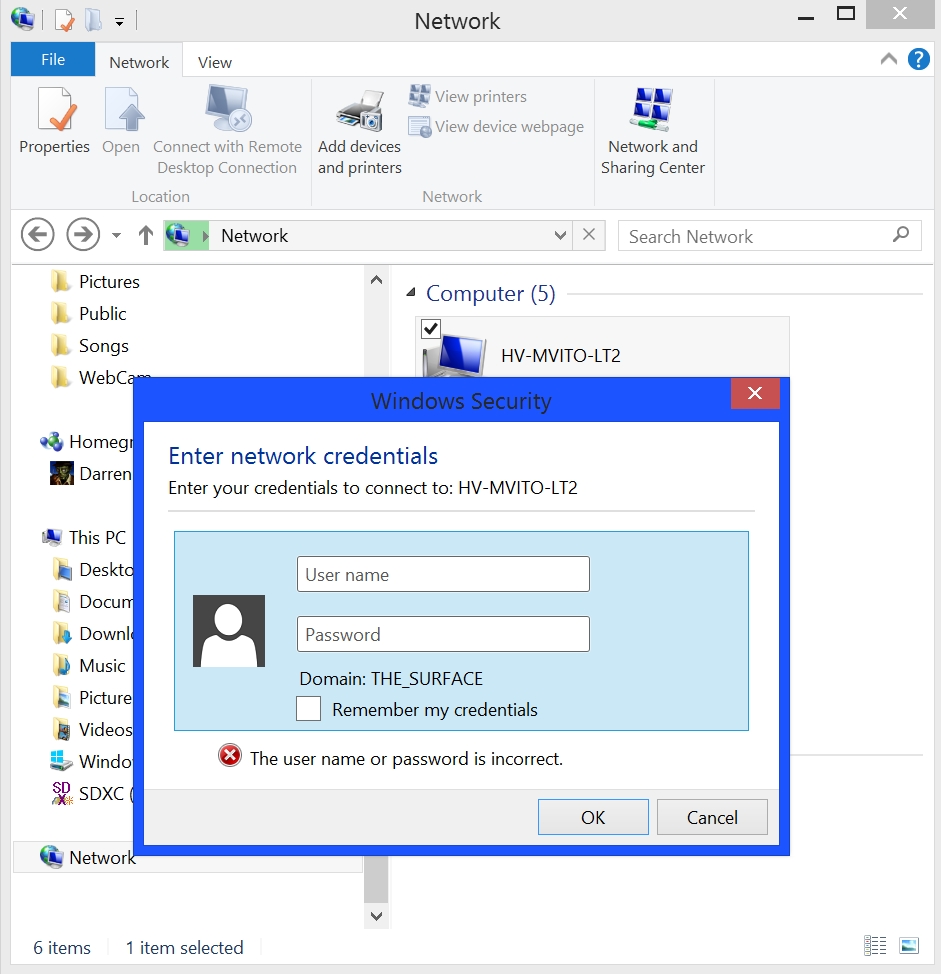
I double-clicked on MATTSPC, and sadly it gave me a login screen. Same for MVITO.
However, if I was the evil type and had a brute-force password cracker, I could very well have attempted an intrusion, and depending on the strength of his password had some success. I couldn’t access the two Macbooks, however further attempts at MVITO eventually gave me access to a network printer they use, specifically an HP OfficeJet J4500 – likely at their home or perhaps a small office. I had unfettered access to it, and could have flooded it with pictures of this guy.
This was really bad. Luckily for Matt and MVITO guy, they had password protected machines, but that won’t stop someone who’s determined as we’ll learn later in the semester. Even with that, I still had access to one of their printers at home, and that can be more of a security risk than you might think. It’s fun for me, but it won’t be fun for anyone if someone wants to really start mousing around in their network.
While I was snooping around in other people’s business, I thought I’d use the Wireshark packet analyzer to really get into the deep details of the traffic flying around the plane.
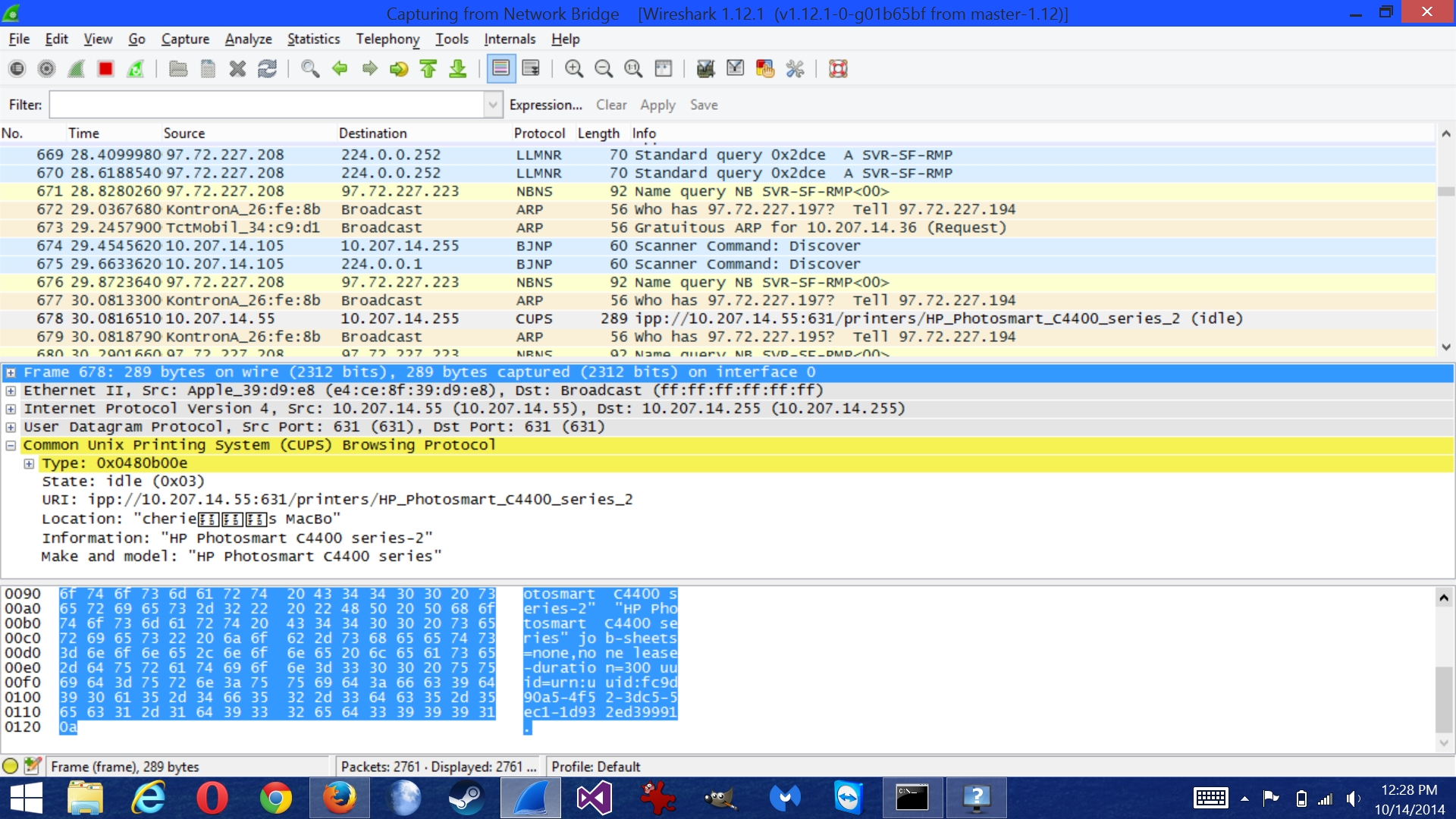
In the below image you can see I found the ipp (Internet Printing Protocol) address of an HP PhotoSmart C4400 Series 2 printer, indicated right above the blue highlighted line, attached to (what I assume is) a Macbook named “Cheries Macbook” as you can see just under the yellow highlighted lines. It even had the UUIDs (Universally Unique Identifier, big blue highlights at bottom of image) which allows for remote access to devices without a central controlling or organizing mechanism. Remember this guy? It’s endless printing time again!
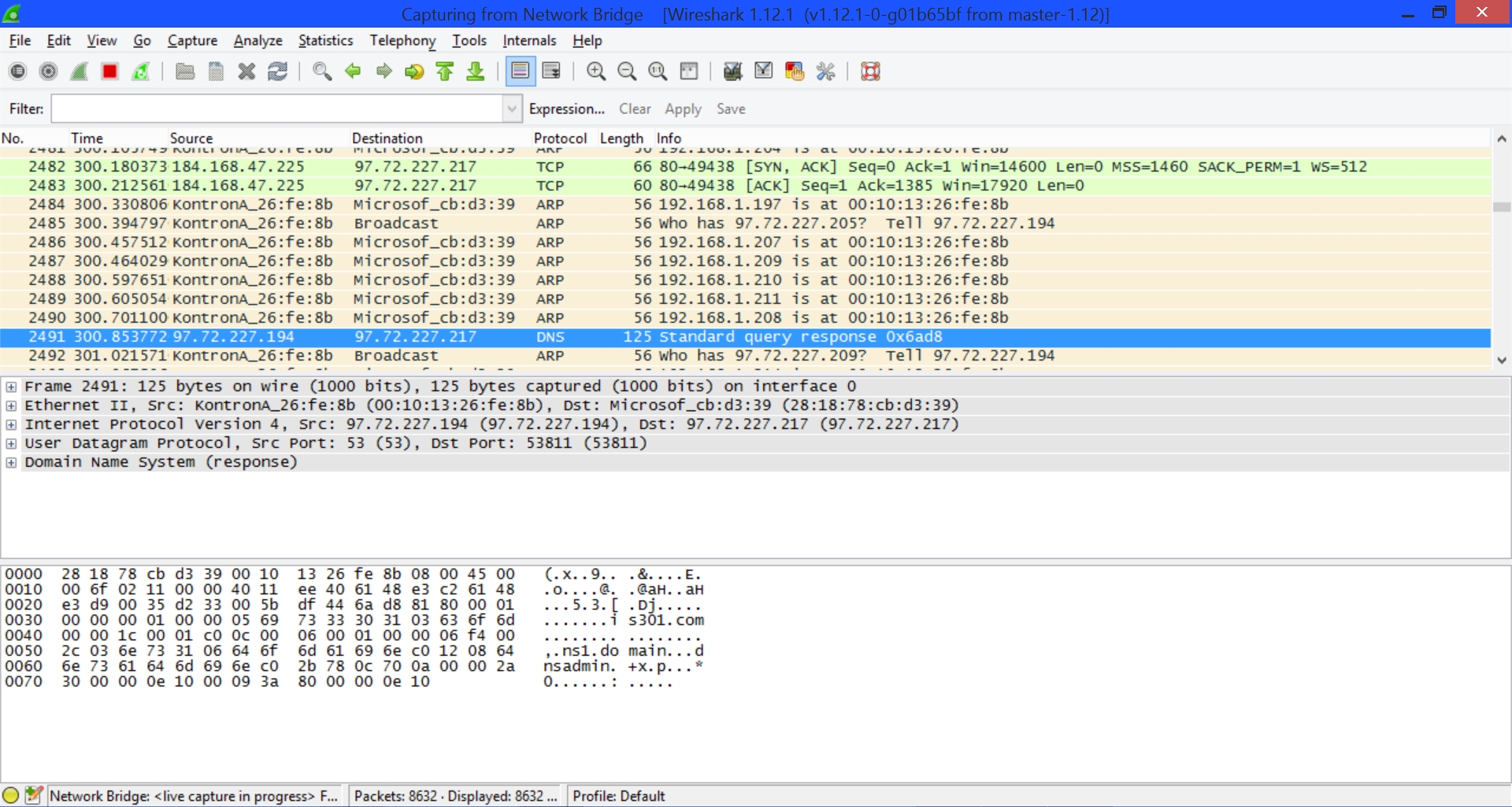
But there’s more. I also found a device named DannyJean, another named Brigittes iPad, and if you look closely among the dots representing the packet payload in the third panel of the image below, you’ll see someone trying to get to a destination that is familiar to you all.
With all that fun out of the way, a little about how it all works. It’s surprisingly simple. And slow.
Just like anywhere else, there is an access point on the plane, and the plane itself connects to a signal in one of two directions; either via ground towers below, or satellites far above. There are positives and negatives to both, and as we’ll see, this technology, like any other, goes through improvements and versions as the technology matures and the demand rises.
When a plane uses ground towers, the plane connects to a network of ground towers using a cellular connection, EVDO specifically, which has some advantages over pure WiFi, the main one being that it is always on even if away from the tower. The biggest provider of that service and the company who has set up the towers for airplanes to use is GoGo, who has a whole network of towers scattered across the country, and they use a technology dubbed ATG (Air-to-Ground). It’s slow however, only about 3 megabits per second divided up among everyone on the plane. But just as wireless technology has matured over time to provide faster speeds at better frequencies, known as 802.11 – the first version was 802.11a, then 802.11b, then 802.11g, then 802.11n – GoGo has now largely switched over to its new technology, ATG-4. This is simply a service improvement and provides about 10Mbps over cellular to the plane, which is still not great because everyone’s using that same bandwidth, but it’s better than what came before.
If the plane is connecting to a satellite for its signal, the big company providing that technology is Row 44, and they place an antenna on the plane just like your car might have that little stubby antenna on the roof to get satellite radio signals. The antenna connects to the satellite, which send the signal down to a dish, and off to the Internet. The most amazing thing about it all? Both these alternatives actually use a modem connected to an access point, just like a router and modem you might have at home.
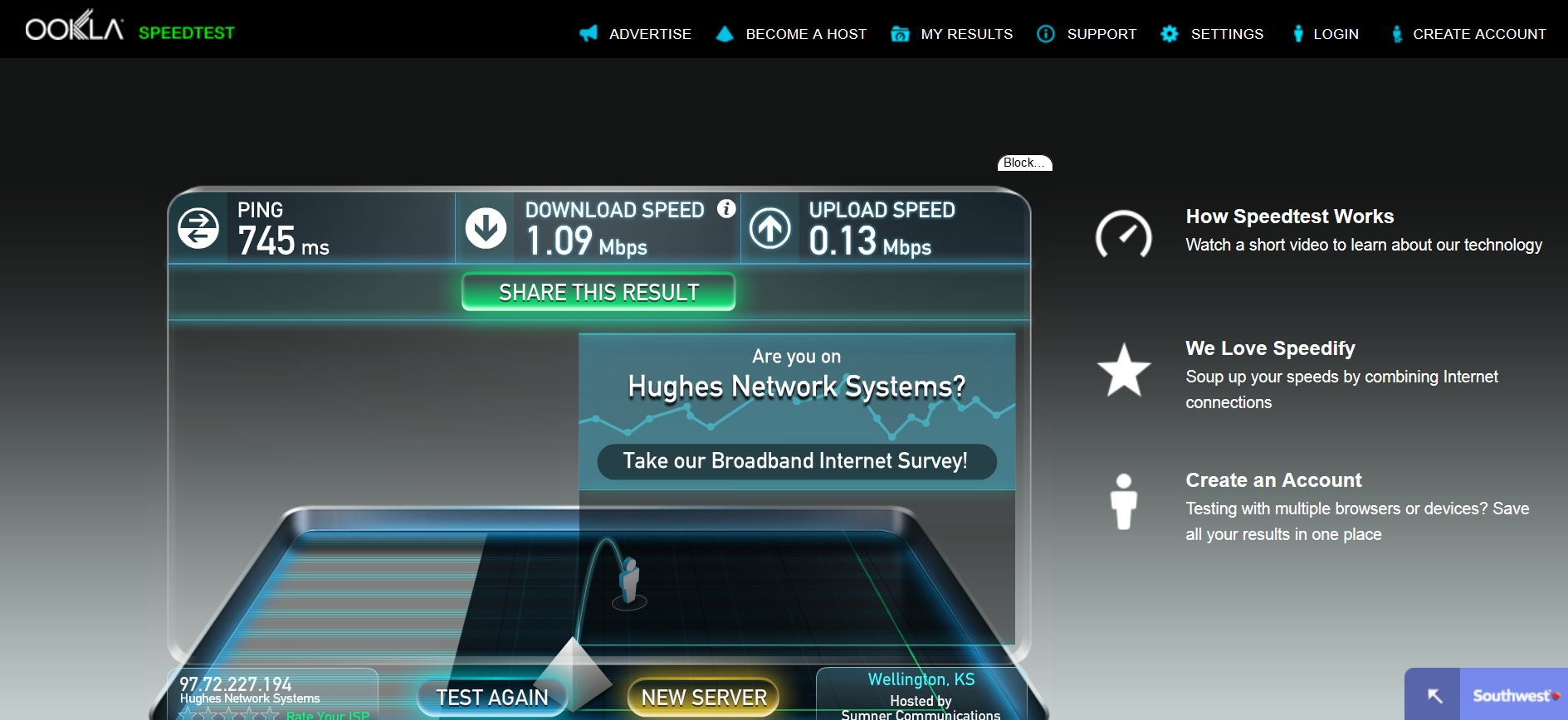
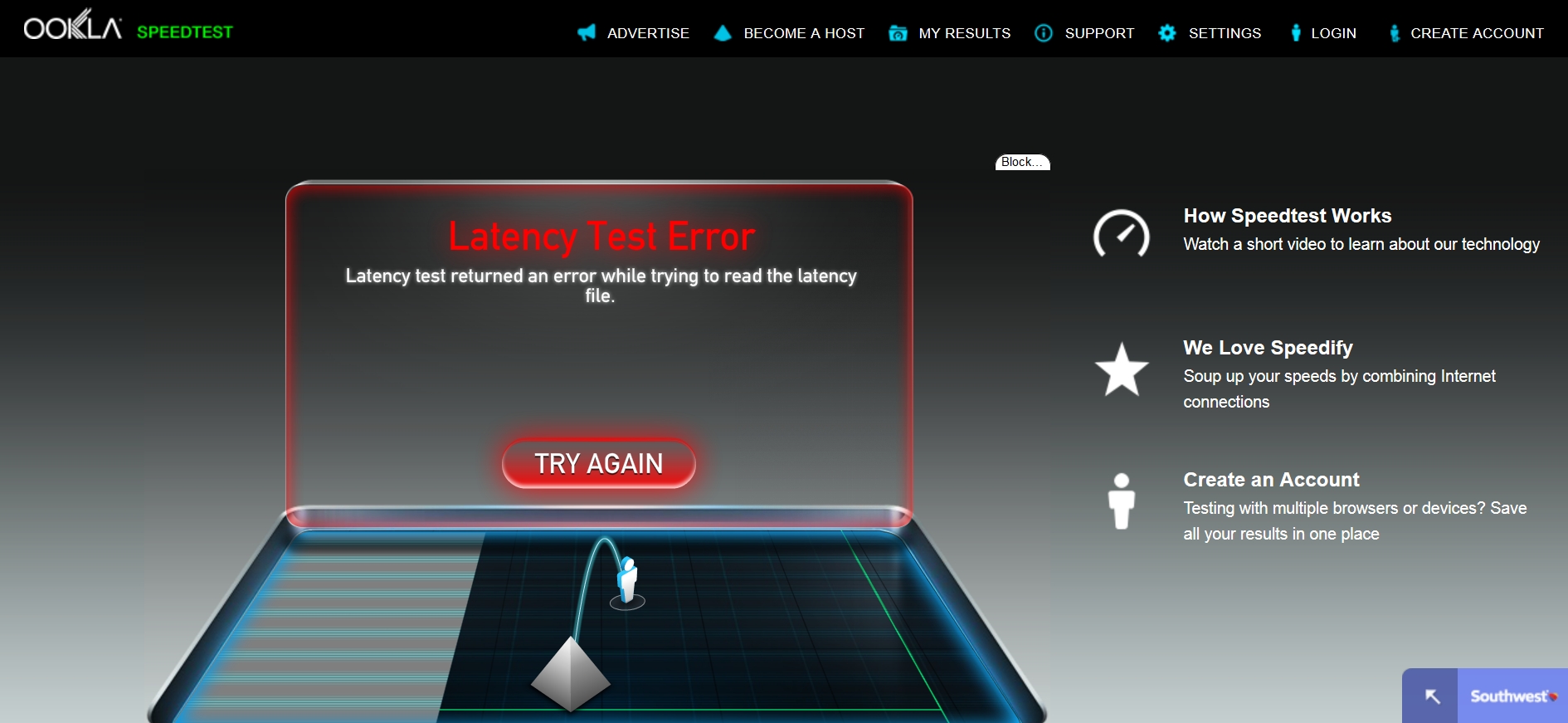
Again, the speeds are on the low end of terrible, and the reliability, well, not so reliable, but it’s better than no connectivity during those times that it’s useable which is never. I ran another speed-test on the network on the second leg of my journey in a much more modern plane, and got what this time really are easily the most deplorable, disgraceful results I have ever seen for anything. Look at the ping, upload speed, and download speed I received:
My hotel isn’t doing much better, I had to write this up out in the lobby just to catch a signal to avoid seeing this (note the tabs. At least twitter came up):
And all this is bad, because everyone knows we have to be connected at all times, or else this happens: