Tag Archives: Security
Massive information theft unveiled
Over on Tom’s Guide is a post revealing that a massive, and I do mean massive theft of information has been taking place for many years and by the same attack.
The attack, dubbed NightHunter by the security firm that discovered it, has been using an unusual form of hostile software to carry out the theft. Using keyloggers (which record keypresses and relay them to a third party, something we’ll talk about in class) embedded in phishing emails (fraudulent emails asking for account information, something we’ll also talk about in class), they were able to steal information – including login information – from sites like Skype, Facebook, Twitter, Amazon, LinkedIn, Google, and bank sites to name only a few.
As far as I can tell this is a new revelation, and the attempt to figure out who is behind it is still going on. In the meantime, be careful. Keyloggers are the most difficult type of malware to identify if your machine has been infected.
LED lights are a surprising security risk
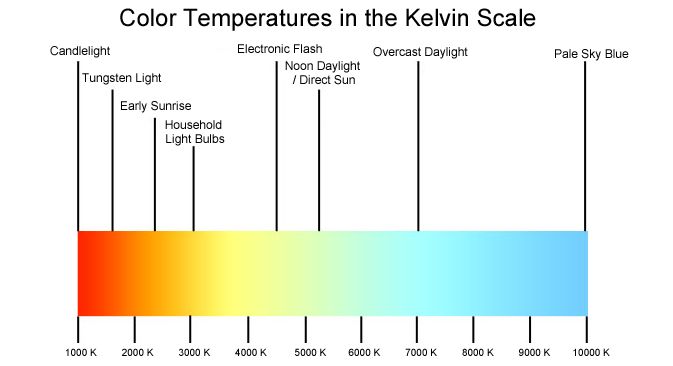
We’re all familiar with LED (Light Emitting Diode) lights, they’ve been used as decorative and accent lights for years. We are only recently beginning to see suitable LED replacements for the warm light of incandescent bulbs – bulbs that use filament in a gas-filled globe – in standard household fixtures, and with the manufacture of regular incandescent bulbs now banned by federal mandate and major efficiency standards put in place, the switch to LED takes on more importance.
LED bulbs are a marked improvement over incandescents in many areas; They use substantially less power, about 95 percent less than an incandescent (The seven gigantic pine trees in my backyard are wrapped with LEDs, and if I were to leave them on all year long, the total cost would be about $6), they last for decades, they emit almost no heat and what heat they do emit is re-absorbed by a tiny heatsink.
They have had some major limitations, however, but with the cost rapidly dropping the two most glaring become their design and the quality of light they give off. Many LED bulbs have an unsightly plastic base, and until only recently they tended to give off a ‘cool blue’ light that looked very artificial. That’s in contrast to the warm, yellowish light of an incandescent.
Now, however, LED lightbulbs have finally improved their design and are being made with a wide range of color temperatures that should suit any home. Not only that, we now have color changing LED bulbs whose color choice and cycling can be controlled from a smartphone! Pretty neat stuff.
But therein lies the huge, hidden problem.
We are seeing a major push for the creation of the Internet of Things, in which all electronic devices are connected to the Internet. This would allow for additional functionality, such as a refrigerator being able to monitor what is left inside of it and order more food, or a door lock that be remotely locked or unlocked, or a thermostat that can be remotely set and monitored. Incidentally, that Honeyell Lyric from the last link is actually the first in what is expected to be a whole host of connected devices, all under the Lyric brand.
In order for connected ‘things’ to work however, you have to have credentials, such as a username and password, that allow you to access them. And it is because of that, and with little surprise, that LED smartbulbs have been hacked to provide a third party with the username and password used to connect them. Specifically, it was the Kickstarter-backed LIFX bulbs that were hacked, however any bulb that becomes part of a network of connected bulbs within a location would be susceptible. If you’re wondering why all the bulbs in your house need to be connected together in a network, it’s so they all act accordingly, and you don’t have to, say, dim all of them in a room one by one; just tell them to dim and they all do it at once. The LIFX bulbs are, to be fair, pretty remarkable. I’ve considered adding a few for when I listen to disco.
The vulnerability has been fixed, but it shows the danger of having things that are always connected. If they are always connected, you are always connected. Even your lightbulbs aren’t safe.
Unbelievable real-time map of global hack attacks
Norse Technologies, one of the leading network-security and monitoring companies, has released an absolutely mesmerizing global map that shows, in real time, global hack attempts, including the type of hack, the origin of the hack, and the intended target. That’s a picture of it in the header, and while writing this post I also was fortunate enough to witness a massive, coordinated attack that you can see in the image below. Fun!
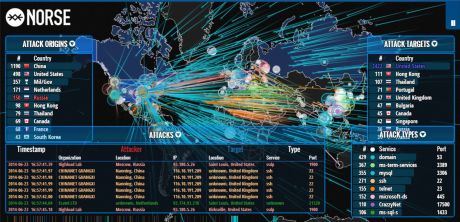 You can hover over any on-screen element top get more information about that particular attempt. Norse achieves all this by using its own honeypot infrastructure. A honeypot is a type of server that sits between the Internet and a company network, and is intended to look like a regular server on said network. However, it is actually specifically designed to attract hack attempts and fool the attacker into thinking they have successfully gained access to a system or network, all the while while monitoring the attempt and gathering as much information as it can in order to learn about network vulnerabilities or to gather information for a potential prosecution. Honeypot servers can be deployed in several ways, however it is not uncommon for them to have a small amount of actual corporate data on them to maintain the ruse for as long as is required.
You can hover over any on-screen element top get more information about that particular attempt. Norse achieves all this by using its own honeypot infrastructure. A honeypot is a type of server that sits between the Internet and a company network, and is intended to look like a regular server on said network. However, it is actually specifically designed to attract hack attempts and fool the attacker into thinking they have successfully gained access to a system or network, all the while while monitoring the attempt and gathering as much information as it can in order to learn about network vulnerabilities or to gather information for a potential prosecution. Honeypot servers can be deployed in several ways, however it is not uncommon for them to have a small amount of actual corporate data on them to maintain the ruse for as long as is required.
They also mention they are following darknet attacks, but I don’t know why that would be necessary. Darknets are networks that run underneath the Internet, using virtual private networks and tunneling protocols and things of that nature to avoid detection and access (Silk Road, in the news a lot recently, was a darknet used to traffic weapons, drugs, in some cases even people), but there are enough regular attacks that darknet monitoring wouldn’t be necessary. I suspect their use of the term is representative of their own network of honeypot servers.
NOTE: I could only get the site to run smoothly in the Chrome browser, and it’s worth downloading just for this. It worked in Internet Explorer and Firefox after a refresh, but very slowly, so be aware.