Tag Archives: Security
Important: Flash zero-day exploit uncovered

Although I usually try to avoid strong, one-sided opinions on these posts, I’m just going to come out and say it: I hate Flash. Hate it. It is now, and has always been, far more trouble than it’s worth, with it’s supposed benefits never coming close to outweighing the risks. If you’re not familiar with Flash, it’s what allows things like small browser games, some videos, but most of all banner advertisements, to run in webpages. They even try to get you to install another bad product, MacAfee AntiVirus, when you install Flash. Unbelievable. There are other technologies, such as Java, that do the same thing as Flash, but Flash is very lightweight. I won’t use the hyperbole that was used at the Register, but I completely agree with their take on it.
You know why it’s always showing you this dialog? Because there’s a recurring problem.
Sony begins to settle

Remember that Sony hack that happened? And that other Sony hack? And that other one? Each time Sony gets hacked, it’s always one of the biggest hacks in history. It’s bad when it happens to Target or Home Depot, but with Sony being a technology company, it’s more of a problem for them not just in terms of actual damage done, but also in reputation.
I just received an email today that a settlement has been reached regarding the 2011 Sony hack, the first one linked at the beginning of this post, and I may be part of it. In fact, if anyone had an account with Sony or any number of its subsidiaries or services, you may be entitled to one, or perhaps more, possible compensations.
Rather than dissect the email, I’ll just paste it below and you can determine for yourself if you’re part of it. Although if you are, you should have received the same email already. This also illustrates that this kind of data breach can impact a company for years afterwards. Just like an oil spill, a data spill is very hard to clean up, and very hard to remove from the minds of the public.
Here’s the message:
If You Had a PlayStation Network, Qriocity, or Sony Online Entertainment Account Before May 15, 2011, You Could Get Benefits from a Class Action Settlement.
A settlement has been reached with the Sony Entities about the illegal and unauthorized attacks (the “Intrusions”) in April 2011, on the computer network systems used to provide PlayStation Network (“PSN”), Qriocity, and Sony Online Entertainment (“SOE”) services. The Sony Entities deny any claims of wrongdoing in this case, and the settlement does not mean that the Sony Entities violated any laws or did anything wrong. Who is included? The Class includes everyone in the US (including its territories) who had a PSN account, a Qriocity account, or an SOE account at any time before May 15, 2011. What does the settlement provide? There are various benefits, depending in part on what type of account(s) you had. Benefits you could get (if you qualify) include:
• Payment equal to paid wallet balances (if $2 or more) in PSN or SOE accounts that have been inactive since the Intrusions,
• One or more of the following: a free PS3 or PSP game, 3 free PS3 themes, or a free 3-month subscription to PlayStation Plus (once valid claims exceed $10 million, class members will still be eligible for one free month of PlayStation Plus),
• A free month of Music Unlimited for Qriocity accountholders who did not have a PSN account,
• $4.50 in SOE Station Cash (amounts will be reduced proportionally if valid claims exceed $4 million). Identity Theft Reimbursement: If you had out-of-pocket charges due to actual identity theft, and have documentation proving that the theft was caused by the Intrusion(s), you can submit a claim for reimbursement up to $2,500. Reimbursements will be reduced proportionally if the total amount payable on all valid claims would exceed $1 million. How can I get benefits? To get benefits, you must file a claim form. Claim forms are available at WWW.PSNSOESETTLEMENT.COM. You can also request claim forms from the Claims Administrator by writing to PSN-SOE Settlement, PO Box 1947, Faribault, MN 55021 or by calling 1-877-552-1284. The earliest deadline to file a claim is August 31, 2015, or 60 days after the settlement becomes final and effective. Visit the website for more details on submitting a claim online or by mail. Your other options. Even if you do nothing, you will be bound by the Court’s decisions. If you want to keep your right to sue the Sony Entities yourself, you must exclude yourself from the Settlement Class by April 10, 2015. If you stay in the Settlement Class, you may object to the settlement by April 10, 2015. For instructions on how to exclude yourself from the Class or object to the settlement, please see WWW.PSNSOESETTLEMENT.COM. The Court will hold a hearing in this case on May 1, 2015, to consider whether to approve the settlement, and a request by Class Counsel for fees, costs, and expenses up to $2,750,000. You or your own lawyer may appear and speak at the hearing at your own expense. For more information or Claim Forms: WWW.PSNSOESETTLEMENT.COM or 1-877-552-1284 PARA UNA NOTIFICACIÓN EN ESPAÑOL, VISITE NUESTRO SITIO DE INTERNET.
Watch an interview with a well-known hacker

The most well-known hacking group is Anonymous, known for their Guy Fawkes masks and high-profile attacks against targets such as Sony, the Church of Scientology, Westboro Baptist Church (a hack that was, impressively, carried out during a live interview), an ironic very high-profile attack against security firm HBGary, even Gene Simmons’ website, and there are many others. I was impressed, in a way, when a member of Anonymous was arrested at UNLV, and turned out to be a journalism student.
However there was another group, an offshoot and sometimes-rival, known as LulzSec that carried out some hacks of its own, apparently just for the, well, the lulz. Their targets included PBS, Fox, Arizona State Police, the U.S. Senate, and, of course, everyone’s favorite target, Sony. There were many other targets.
LulzSec disbanded, however, after many of them were arrested after their leader, ‘Sabu,’ real name Hector Xavier Monsegur, turned government informant, and he has helped them in other endeavors as well. This was part of a plea deal that he said he agreed to due to his kids.
Now, he has been interviewed on CBS This Morning, and I have embedded a clip below. I couldn’t find the full interview, but if I do I’ll update this post. Even with the four minute clip, it’s still very interesting and gives some insight into the hacker mentality and law enforcement’s attempts to thwart them.
Secure, and I mean *really* secure, your email. Just not right now.

Worried about becoming the next Sony? Afraid all those terrible things you said about your friends, family, coworkers and teachers will be released for the whole world to read? Then perhaps you need to think about taking the next step and taking complete control over your email, even if you have a web-based service like Gmail or Yahoo Mail or whatever.
I very recently was made aware of an email client called MailPile, which gives the appearance of a web-based email client, it even runs in a web browser, but it’s actually housed on your own machine. It’s even designed to run from a USB drive if need be.
You can connect the client to any web-based or client-based (Outlook) email service, and it will download all the mail to your local device, and it encrypts them so even if someone gets your PC or USB key they won’t be able to read them. On top of that, you have to have the password for the account itself, as well as a passphrase (if you remember our class discussion) for the MailPile program as well.
New, dangerous ransomware appears in the wild

In class we talked briefly about ‘Ransomware,’ software that compresses / encrypts / locks up your files, then demands payment for the password or key or whatever to get your files back. We also discussed that the amounts of money demanded are never too much to prevent someone from actually paying – if they asked for a million dollars no one would pay it, and the encryption was normally breakable if you knew what you were doing.
Now, in an event that involves many of the topics we discussed in our last class, a scary new ransomware attack is changing all that. Known as OphionLocker (this article shows it may not be as sophisticated as everyone is saying, possibly breakable through a C++ IDE ), it uses what is known as elliptic curve cryptography, a practically unbreakable form of encoding, to hold files hostage, and it is delivered through malicious ads displayed on web pages.
This WordPress site is clean

And we don’t have analog TVs anymore, so that’s a plus considering we don’t want a visit from the ‘TV People‘ (If you’re not a fan of the scary, I’d be careful with that link).
Anyway, I noticed through the Ars Technica feed there on the right hand side of the page that researchers in Finland had discovered a bug in WordPress 3’s comment system that could allow someone to include malicious JavaScript code in a comment, providing the attacker with all kinds of fun things to do. As the article states, by using this code, someone could create a new administrator account with a new password, change the old password locking the old administrator out, and have complete control of the site to do anything they want, including attack visitors and commenters.
It’s exceptionally similar to the way an SQL Injection attack works (remember SQL?), which we’ll talk about in class, except instead of trying to get a database to fess up its contents it attempts to wrest administrator control from the actual site administrator. We need JavaScript, though – how can we get ants to chase our cursor without it?
Luckily for us, this site runs on WordPress version 4.0.1, so we’re not at risk of this vulnerability. I just wanted to make this short post in case anyone saw that and had concerns, which I suspect was exactly zero of you. Continue on, people!
Targeted Hacking Attempts Against High-Profile Hotel Guests

Over on Wired is a post about high-profile hotel guests, mainly but not always in Asia, being the targets of what are known as spear-phishing attacks. As opposed to regular phishing attacks which target as many people as possible, and which we’ll learn about later, spear-phishing attacks target a particular individual and attempt to steal data. The specific malware used for these attacks, and the group using it, is known appropriately as DarkHotel.
To summarize the article, the attackers would upload malicious software to the hotel server, then when the target logged on to the hotel WiFi they would be prompted to download an update to some Adobe software (the article didn’t state which, however never, ever download updates over public or even semi-private networks), but what they actually got was an infection.
More Facebook, but actually Internet privacy
Boy, this week is all Facebook all the time. Weird, considering I don’t use it.
So a couple of days ago I made a post about why I’m not on Facebook, at least at this particular time in my life, but I know many others are and that’s ok. For those of you who are, have you ever worried that someone might be spying on you while you connect? It seems like a strange thing to wonder about considering the whole purpose is to be visible, but in other parts of the world, sharing photos or other information on sites like that can result in serious consequences.
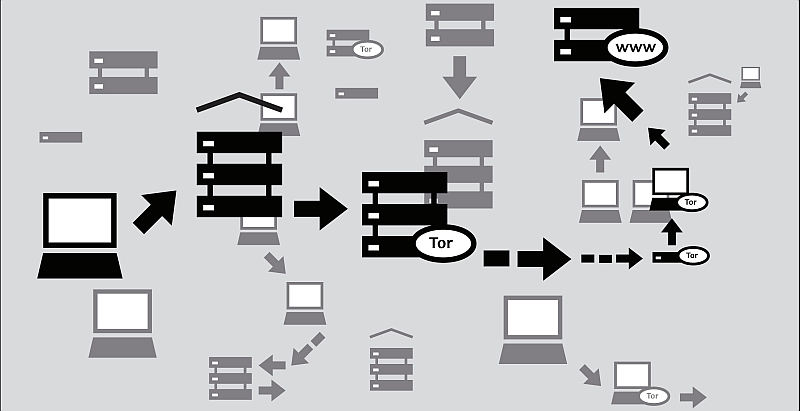
So in a somewhat surprising move, Facebook has created a version of their site that can only be accessed using TOR software. Let me give you some background:
TOR is (was) an acronym for “The Onion Router” (which is why the technically correct way of writing it is TOR, not Tor, although Tor is now the catchall term for it). What it does is bounce your connection to a site through a trusted series of secure points before you head out on to the Internet proper through an exit node, where you exit form the Tor network tot he Internet itself, all of which makes it very difficult to trace your origins or determine the true destination of what you’re doing on line. So if someone wants to monitor your network connections to try and determine where you’re going or what the origin of a particular transmission is, TOR would make that very difficult.
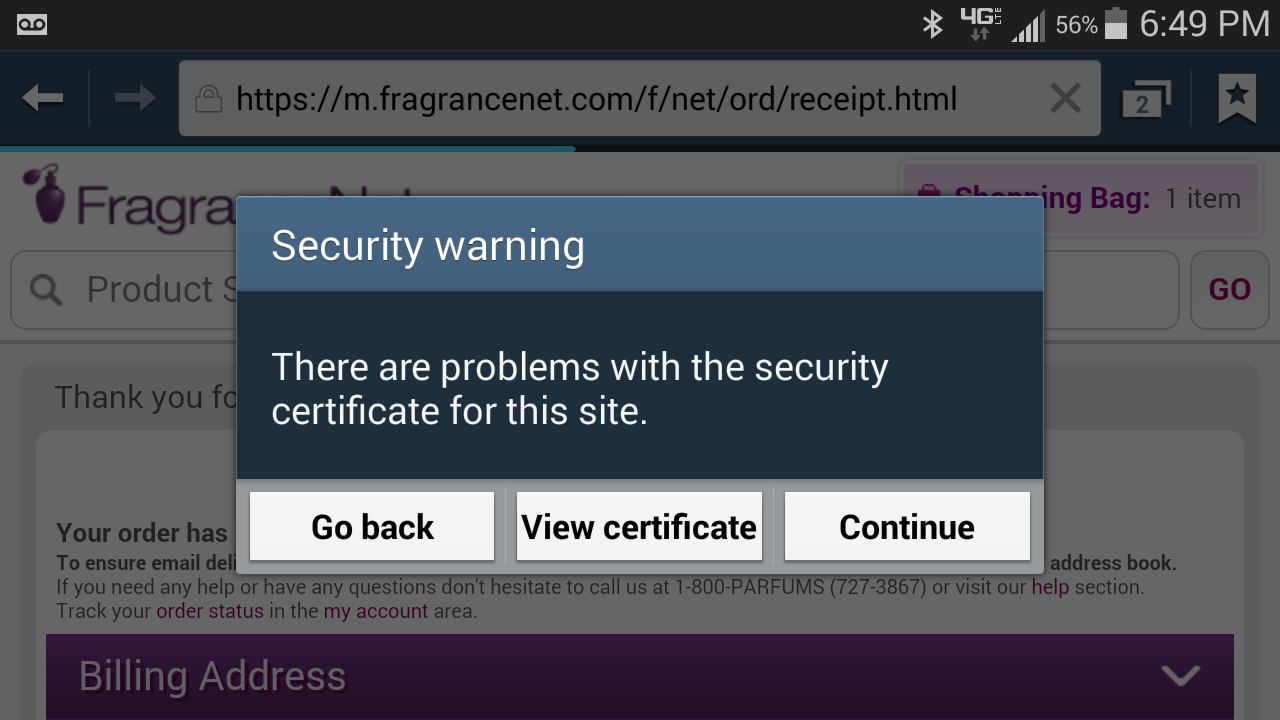
Security certificates and what they mean

Yesterday I received an email from a student who was in this class last semester, and they had a question regarding a security-certificate warning that popped up as they carried out a mobile retail transaction on their cel-phone. The screenshot of it is below, and they were understandably concerned:
Very Important: Major PowerPoint Vulnerability
I wanted to let everyone know that Microsoft announced about a week ago that there is major security issue with PowerPoint, in which a bug in how Object Linking and Embedding (OLE) works could give malicious attackers full access to your machine.
OLE is the means by which you are able to insert data from one type of program into another program, for example embedding a spreadsheet into a PowerPoint presentation. But there are a couple of things to keep in mind regarding this flaw:
First, there is a fix, even an automated one. You can find out all about it on this page at the Microsoft support site.
Second, the attacks using this vulnerability have been very limited, no widespread havoc just yet.
Third, if you were attacked, the attacker would only get the level of control you had. So if you were a regular user, those are all the rights they would have. If you were an administrator, on the other hand, which many home PC users are, things could be different. Administrators have the ability to do things other users don’t, like install programs, make system changes, etc.
Fourth, *you* have to let it happen by opening the PowerPoint file in the first place. Here’s a bit of advice that I hope we all already know: DON’T OPEN EMAIL ATTACHMENTS FROM PEOPLE YOU DON’T KNOW! It’s very, very easy to avoid this issue altogether, and why the attacks have been limited. It requires you to open the mysterious presentation from the person you’ve never heard of. Don’t do that, and you’ll be fine.
Header image credit: techaeris.com