Why your screen just went black and white: Windows 10 color settings and color-blindness

UPDATE: I’m leaving the original post up, however the latest Windows update changes some of this around. The ‘Windows key-ctrl-c’ shortcut for setting filters is no longer enabled by default, and while you can still use the ‘right-click on desktop and select Personalize’ technique, in settings you now have to choose ‘Ease of Access’ to access these settings, which does make more sense. Additionally, high-contrast settings are where they’ve always been, but black and white / color-blind settings are now under the ‘Color filters’ option.
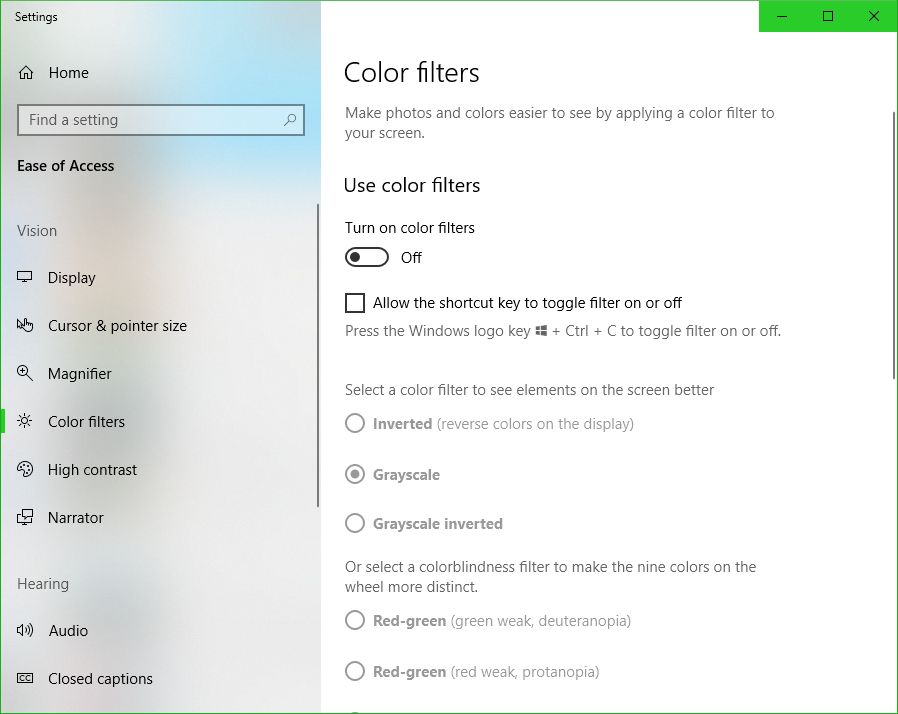
Here’s the new screen in settings, and the original post follows:
If you’re using Windows 10 and looking for a fix as to why your screen has suddenly gone black and white, or if it hasn’t and you’re looking simply to learn something new and interesting and fun (and what can be used as a cruel trick on your friends / acquaintances / enemies, but please don’t do that), try the following: Hold down the Windows key, then Control, then C. If your screen was black and white, problem solved! If it wasn’t, well, now it is. Do the combo again and you’ll be good as new. Spoiler: You can choose other visual settings for that shortcut; black and white is simply the default. More on that in a moment, and here’s the companion video I recorded for this post.
I’d also like to briefly talk about the importance of color. It is a vital tool in communicating information, although it should never be used as the sole communicator: if someone can’t distinguish red, a red sign will serve no purpose if there isn’t text that also communicates what’s up. But there is no such thing as a green stop sign or a red ‘everything’s ok’ light, and there is a reason for that. For you programmers, you know that you tweak the colors of your IDE to enhance readability and comfort. Never underestimate the purpose of color in design. Also, my Ph.D. was in this very subject so I’m especially passionate about it, as you can tell.
But black and white? You may be wondering why something like this is even a feature. The reason is readability and accessibility, a primary focus of HCI, interaction design, and the larger field of human factors, and remember it’s not the only setting – it’s just the default. The point is to make the screen easier to see for those with visual impairments, particularly color blindness, but these adjustments can also be used by those who simply find stock Windows color settings to be too much. And let’s face it – sometimes they can really be too much.
It reminds me of the old Atari 2600 and it’s B*W / Color switch, which is as far as I can tell the first time a dedicated option was provided to select between one or the other. This wasn’t an accessibility issue, however, it was used because in 1977 black and white TVs were still quite prevalent, and using the black and white setting would adjust the contrast by switching the palettes used, thus making the game easier to see. Without that, in other words if it just switched to a standard black and white with no consideration given to their original colors, on-screen objects that were easily distinguishable in color might be very difficult to distinguish with just shades of gray. So the idea was the same, but the reason was quite different.
The image below shows the B*W / Color switch taken from one of our 2600 consoles in the gameroom here at UCI, while the other two screens show Slot Machine for the 2600, running in the Stella emulator, and how it displays in color and in switched black and white.
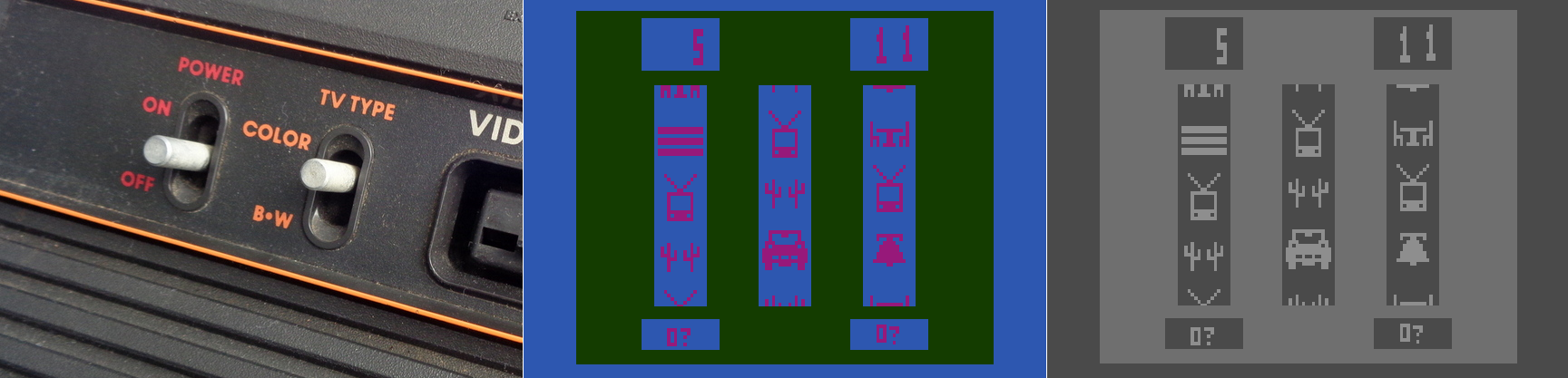
Atari 2600 Slot Machine in color and black and white
Yet that was back in 1977. With todays monitors having HD and 4K capabilities, why on earth would we need a black and white setting? There are several reasons, the most obvious being that black and white photography, which adds an ethereal, ageless quality to a photo, and in my opinion often requires the viewer to focus more on the content and composition of the image, is still very common today. However you can’t simply switch from color to black and white for the same reasons we had a switch on the old Atari; what works well and is easily distinguishable in color may blend into a single shade in black and white. No, unless you are shooting in black and white natively, and if you are you should use the RAW setting to get as much contrast and separation as possible, you have to convert an image from color to black and white, manually adjusting for all those settings that would have been done automatically otherwise. That’s one use for the setting in Windows. Of course, it’s possible that a user might have complete color-blindness, and even though that is extremely rare, it does happen: estimates are, for men, between 1:30,000 and 1:100,000 depending on type.
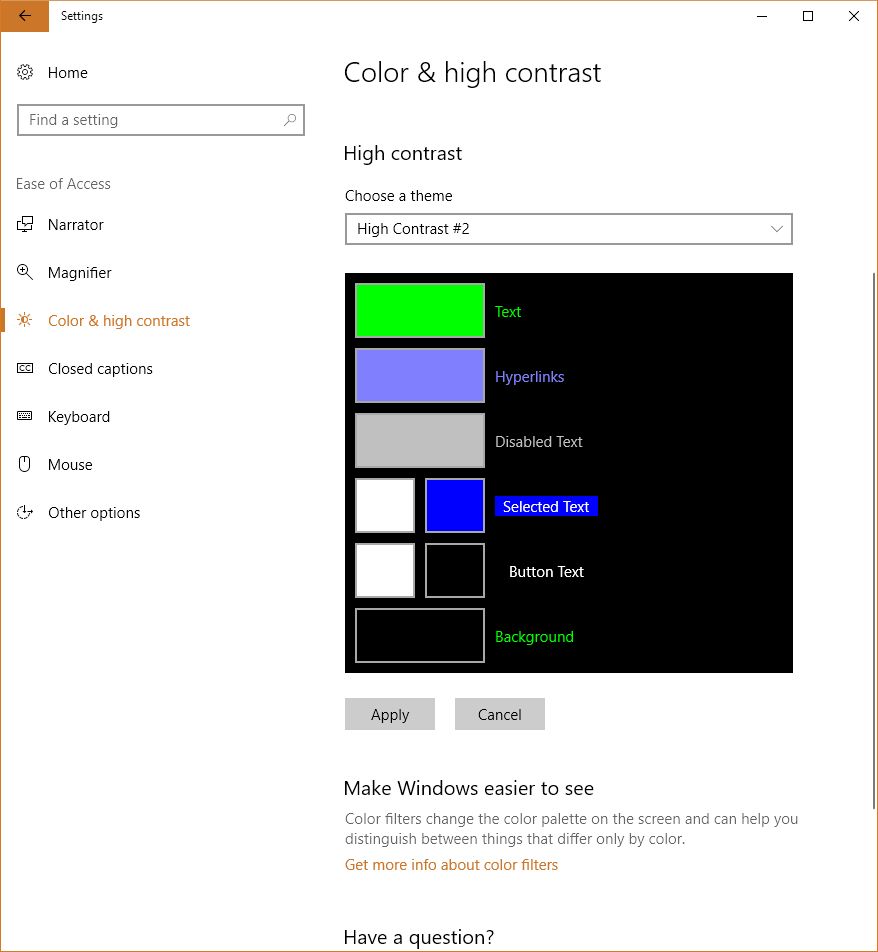
There is much more to this feature than simply switching between color and shades of gray, however. That capability in Windows is simply foreshadowing for much more important color-based adjustments that can be made. To see what they are, go into settings, select ‘Colors,’ (Alternatively: Right-click on your desktop and select ‘Personalize’), and scroll down until you see ‘High Contrast Settings.’ Click that, and whatever is selected under the heading ‘Choose a Filter’ is what will Windows will switch to when the shortcut Windows key – Ctrl – C is pressed. You can see the choices below.
So what do these do? The first three should be obvious; grayscale converts to shades of gray, or black and white informally, ‘Invert’ inverts the colors on the screen, although what ‘Invert’ actually means cans be complicated. Factors to consider include whether you are using RGB or CMYK color standards, the former being additive and the latter being subtractive, and what you’re trying to invert. Normally, when colors are inverted they are switched to their Complementary Colors, which are those opposite each other on the color wheel and offer the highest contrast to each other, although that high contrast can be a nightmare for text (red and green are complementary on a CMY color wheel, for example), so always consider application and the color scheme you’re using.
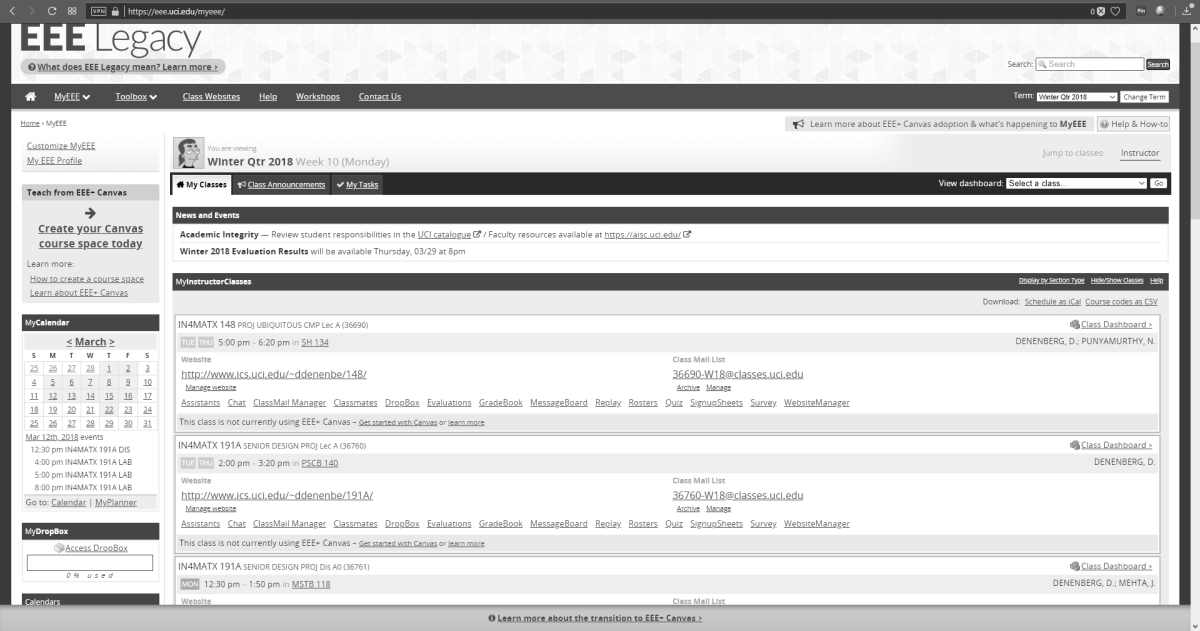
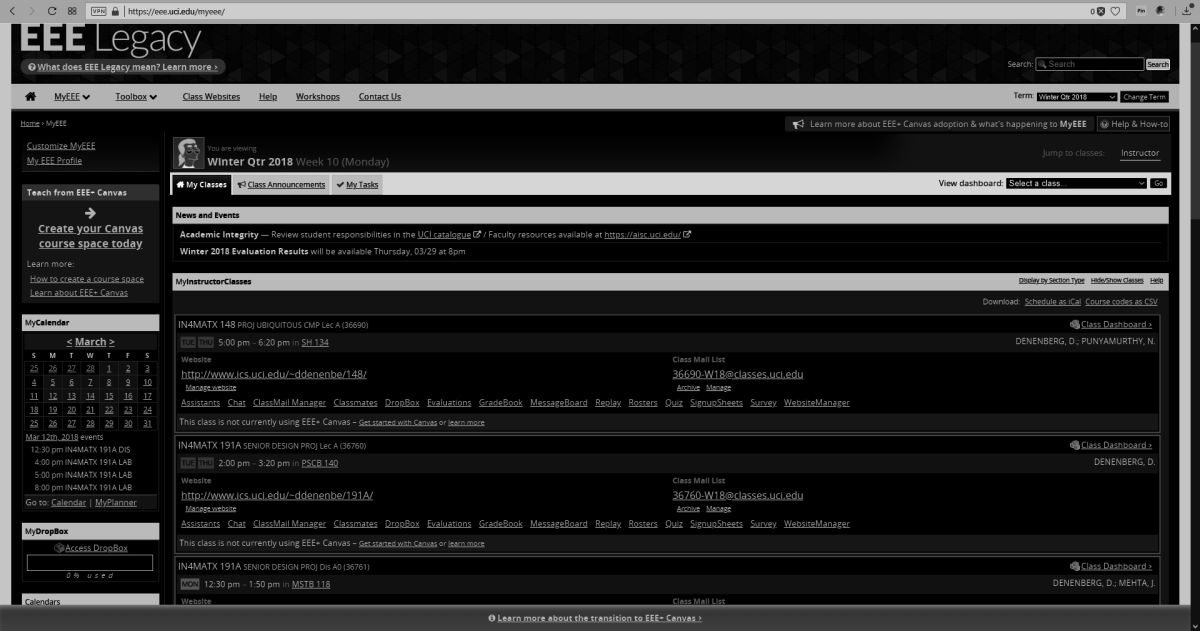
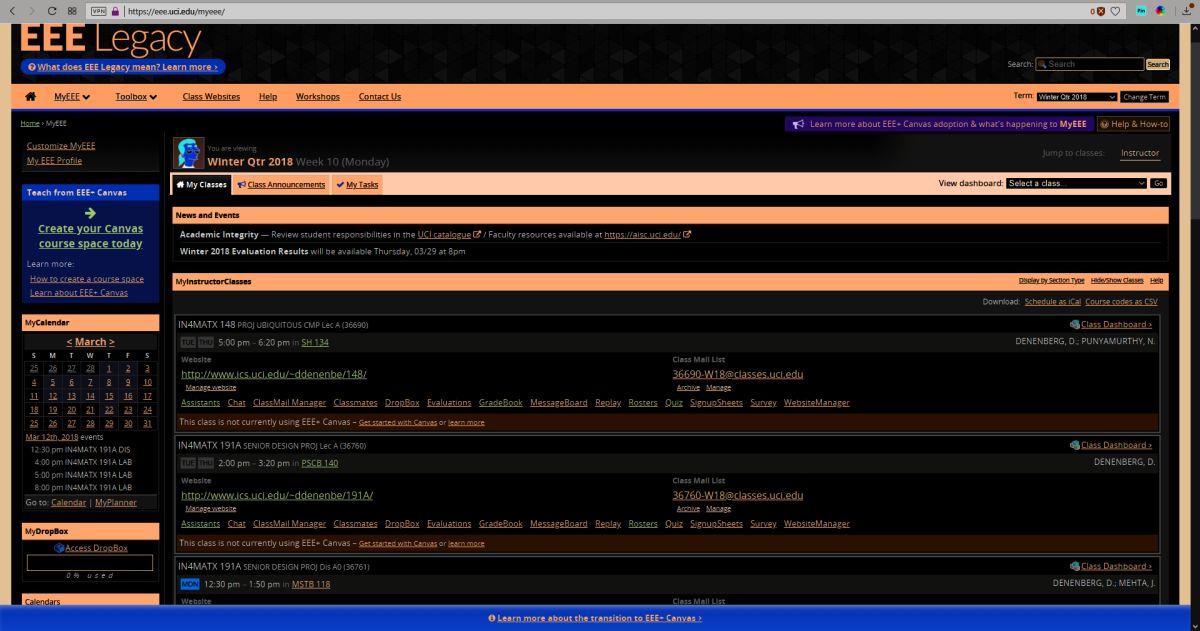
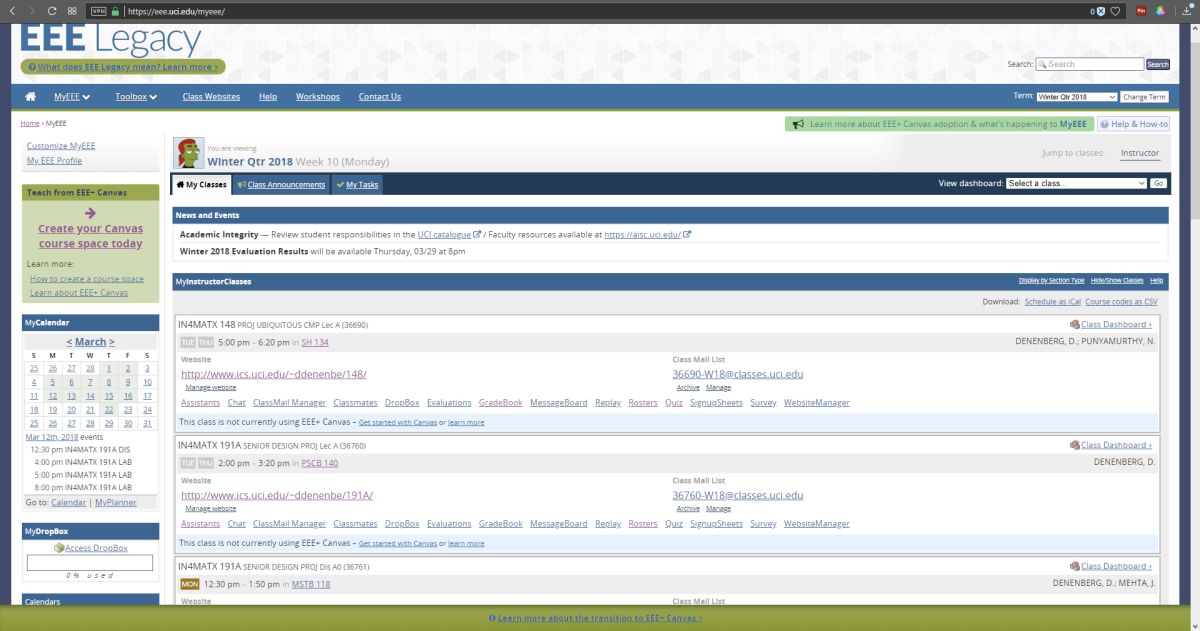
I’ll be using UCI’s EEE page as I see it to show what these selections do, since it has an interesting combination of colors including various shades of blue and yellow which are sort-of-but-not-quite complimentary, my avatar has red hair, the ‘Learn about’ box in the upper right is green, and if you look closely you can see the ‘MON’ in the lower left is a shade of orange.
As you can see, these allow a user to change the color scheme to fit their particular needs for viewing web pages or images or whatever, however it is the next three options that deserve our attention, as they are a cornerstone of accessibility and design in the user interface and HCI in general.
If you look back at the earlier image showing the filter options, you’ll notice the last three are ‘Deuteranopia,’ ‘Protanopia,’ and ‘Tritanopia.’ These are types of color blindness – a term that I really don’t like even though it’s accurate – that affect someone’s ability to process colors. We also need to distinguish between some terms here, as they are often, at least from my experience, misused. All of these conditions can manifest in two primary ways: -opia and -omaly. The former, which are the ones indicated in Windows’ color settings, mean you are missing the related cones altogether. In other words, Deuteranopia is a complete lack of red cones (known as L-cones, for long-wavelength), Protanopia is a complete lack of green cones (known as M-cones, for medium wavelength), and Tritanopia is a lack of blue cones (known as S-cones, for short wavelength). The latter is a form of blue-yellow color blindness, although Tritanopes don’t confuse those two colors so it’s not an appropriate name, while the former two are versions of red-green color blindness.
In contrast to the previous circumstances in which the cones are entirely absent, it’s also possible that the cones are present but weak to a particular color stimulus; those cases use the ‘-omaly’ suffix. So Deuteranomaly is a weakness to red, Protanomaly is a weakness to green, and Tritanomaly is a weakness to blue, and very rare; about 1:1,000,000. But the cones are not missing as they are in the previous cases; they are simply weak or mutated. Therefore, one way to address it is to increase the amount of or saturation of the color in which a person is weak, although this in itself is not a complete solution. Additionally, how these manifest in someone’s vision can be wide-ranging, from little impact on color-vision to something very close to the -opia variant.
These types of color deficiencies can cause real problems in distinguishing elements in any visual field, especially a computer screen. Research into accessibility has not only been ongoing for many years, but guidelines for the use of color are in place for all large companies such as Microsoft, Apple, Google, and all the way to the U.S. Government (Usability.gov is overseen by the Department of Health and Human Services, by the way).
So in returning to the color / filter settings in Windows 10, I can’t say with certainty whether Microsoft actually means, for example, Deuteranopia, as indicated, or Deuteranomaly, or is using it as an umbrella term. They aren’t the same, and can only be addressed as such through design to a certain, limited extent, but there aren’t separate settings so…I don’t know.
When switching among these filters on EEE, there was no impact as there is no red or green, however there was a noticeable effect when applying the ‘Tritanopia’ setting, as that refers to an absence of blue cones. As you can see, the yellow sections were switched to green, which makes sense as Tritanopes have generally normal red-green vision.
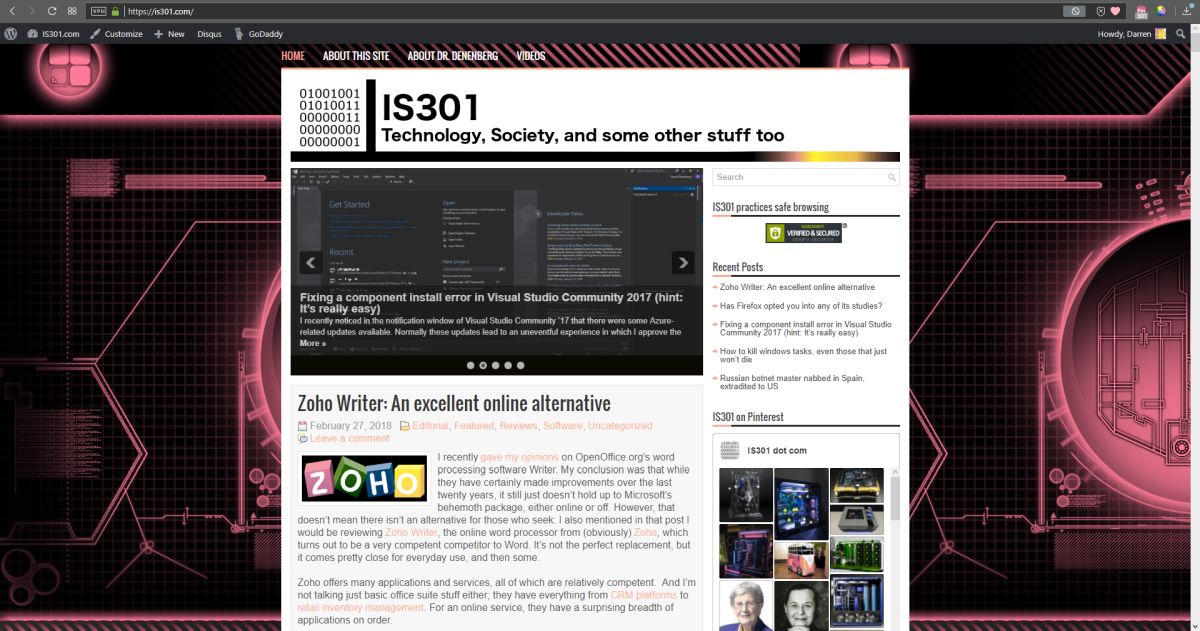
For the Protanopia setting, a good example to use instead of EEE is IS301.com itself. because this condition results in a weakness to red light, and IS301 has a strong red background, the setting reduced the saturation of red in all elements on screen for a noticeable change.
When set to ‘Deuteranope,’ the only change was an increase in saturation of the red elements of the screen, but nothing dramatic.
I also want to mention that you can set up your own high-contrast color themes, tweaking the color for every aspect of the display so it fits your needs perfectly; there are a lot of options for configuration.
On the other hand, apps and programs and everything else have to be designed with that in mind or else they will be negatively impacted by your adjustments, and that results in another problem: Windows will natively adapt to your specification, but it doesn’t mean any of the programs you run under Windows will. That’s something that needs to be enforced more clearly and strictly in Microsoft’s design guidelines.
So what was s simple fix of a black and white screen turns into a deep dive about accessibility and color blindness – I love it when that kind of thing happens. If you just wanted to fix your screen, then you’re not reading this anyway, but we really need to be aware, especially software and interface designers and developers, that for usability and accessibility these options and many others need to be available so everyone can benefit from the functionality your software brings.
On a related side note for those who may be reading and and are living with color-blindness, I discovered that there are glasses that claim to fix the problem. Apparently they create a bespoke filter on the lens for your particular condition and severity, and can bring you to almost normal. I’m not affiliated with the company, I have no idea how well they work, but for the cost they’d better work pretty well. if your’e interested, the company is called EnChroma. If anyone tries them, let me know how it goes!
So long Toys R Us, my old friend

As many of you may already know, Toys R Us is finally closing down for good. While this post is outside the normal scope of this blog, it’s also relevant in so many ways, because it illustrates not just an upheaval in the retail landscape that has been brewing for some time, but also how failure to respond to those kind of tectonic shifts in market trends, consumer demand, fiscal realities, and not exploiting the second most enviable on-line presence can tank a company like Toys R Us. Even now, it still has enough market presence that the closings will have significant upstream and downstream impacts.
More than that, I used to work there many moons ago. I loved it, so this has a powerful personal angle for me.
And they sold games. Rows of glorious games.
I first started working at the Sunnyvale, California Toys R Us back around, what, 1988 or so, in the stockroom, and the header image for this post is the front of the very store where I used to work (added bonus: It was haunted!). My secret plan was to eventually get to the game cage in the front of the store – those of you who have been around for a while may remember that cage, but if not, fear not: I’ll take you there in a moment, but when I started I worked in the stock room in back, and even there I loved it. It was a two-story, seemingly endless room with rows and rows and stacks and stacks of boxes; big items on the top floor and smaller boxes filled with merchandise to be put on shelves on the bottom. And when someone would order something big, like a plastic above-ground pool or a bike or a swingset or something, they would have to drive around the building to receiving, and we would pull the box from stock and put it on a slide – yes, a slide like you’d see in a playground – and send it down to the lower floor, then slide down ourselves and have the customer take it to their car.
We’d also unload the semis that pulled in, filled to the top with boxes in a not-at-all organized manner. The boxes were just thrown in haphazardly, not stacked, we’d have a manifest on paper, and we’d have to climb up into the back of the semi, climb to the top of the pile, and start checking off each box on the manifest, and throw it out of the truck on to the landing, where someone else would, or possibly would not, take it back to the stockroom. And those semis are BIG; they could have hundreds and hundreds of boxes. We never knew what we would get, it was completely random, and it was great. Good times. I saw on Google maps the semis still pull up to the back like always, I just hope now they have at least somewhat automated the progress, although I guess it doesn’t matter anymore.
After a while, I was moved out to bikes, then for some reason to baby stuff which was, surprisingly, still pretty fun – all the excited new parents made it enjoyable (crib recalls were *not* enjoyable, though), and then, I started getting asked to man the game cage.
Finally, I had arrived.
You see, in the 8-bit and 16-bit eras, and even into the 32-bit eras, games were simply represented by their covers in the game aisle. There would be a card that had a picture of the front of the box and the back of the box, and underneath each card were slips of paper with the name of the game and the price printed on them; it’s very similar to how Office Depot does furniture sales now, if you’ve ever seen those. Anyway, if you wanted a particular game, you would take the paper up to the register, pay, and they would give you a ticket you would take to a small booth at the front of the store, and inside that booth was nothing but games. Games everywhere. So many games! You’d give the ticket to the person in the booth, often me, and they’d give you your game. For me, it was a paradise being in there, seeing all the games that were available, reading the boxes and looking at screenshots, getting the excited kids – and sometimes adults – their games, even keeping it clean and organized was a joy. At that time in my life, there was nowhere else I would ever rather be. As I started school on the east coast, I would occasionally work over the summer, but eventually I had to dedicate more time to school and life, including summers, but I never forgot how much fun that job was at Toys R Us.
Also, I looked high and low for a picture of the game cage, but amazingly, I could not find a single one. I did find a couple of the game isles with their paper tags, though, although I’m surprised that even they are hard to find. If anyone out there,anyone reading this has any pictures of TRU game cage, please send it/them along – even Reddit couldn’t help!
I suspected something was wrong all the way back around 2001 or so, when the stores were redesigned to be more ‘playful’ and less like narrow grocery-store isles, only taller. I don’t recall anyone have much of an issue with it, but I suspected that it was a response to ‘something;’ you don’t embark on a complete redesign of an iconic store without being motivated to do so. Later I learned it was because of slagging sales, something that has plagued the chain for a very long time. They tried again in 2015, and we all see where that went.
It took them clear until 2017 to realize the importance of a well-designed, functional, aesthetic website, yet this is also a result of an epic, colossal screw-up on their part many years earlier. See, when Toys R Us first developed their online presence, they did so by partnering with -wait for it – Amazon, all the way back in 2000! That’s when the Internet was still in its fledgling stages, although to the point that e-commerce was starting to take off. If Toys R Us had taken a different path, they could have ridden a wave that saw Amazon become the behemoth, retail landscape-shifting e-commerce megacompany it is today, so much so that Jeff Bezos is now the richest man in HISTORY.
But no, they screwed up, and screwed up big. Instead of leveraging their partnership, in 2006 they sued to get out of their agreement with Amazon in 2006 by saying Amazon breached the terms by allowing other vendors to sell toys as well, which prompted Amazon to countersue claiming TRU didn’t fulfill its obligations and left many orders unfulfilled. It ended badly for Amazon at that time, but it foreshadowed a bad ending for TRU in the future. My guess is they wanted to create their own online presence, although Amazon was, even then, generally king of the hill for this kind of thing, and TRU never did get it right. Other companies had partnered with Amazon as well then broken away, TRU was not the only one, but those other companies, such as Circuit City, well, we see where they are now. Not that leaving Amazon was the sole cause of their demise, but they could have utilized those partnerships much better than they did.
There was also Bain Capital. Yes, Mitt Romney’s Bain Capital. In 2005, they made a leveraged buyout of TRU, shifting all assets to a holding company. The problem is, the toy market has always had narrow margins, and with a leveraged buyout using the assets of the bought out company to leverage (hence the name) the huge loan that is used for the buyout, the assets themselves need to be worth something. Toys aren’t a good asset group in that in that way, and it ended up dumping an enormous amount of debt on top of the company, about $5 billion, and I would have thought anyone could see that would never work out. With $400,000 annual payments towards that loan, they were crushed form the get go. Ironically, or more saddening and angrily, it was Bain Capital that also bought out KB Toys, only to force them to sell thanks to crushing debt as well, and who did they sell to? Toys R Us! Those two aren’t the only ones Bain has impacted, either. Although in fairness, Bain has also had many successes; they wouldn’t exist otherwise. It’s just that these hit close to home for me.
Even so, none of it would have been necessary if Toys R Us hadn’t been mismanaged to this point. To me, they are the Sears of toy stores. Grossly overpriced, absolutely not competitive in any way, worrying on store design instead of competitiveness, yet also haveing been, at one point, the trend setter (remember the Sears catalog?). They couldn’t see the forest for the trees, and focused on the wrong things at the wrong time, allowing competition to blindside them. What could one expect when they bring in the former head of F.A.O. Schwarz, the most expensive toy store to ever exist, to turn things around? Oh right, TRU bought F.A.O. Schwarz in 2009, along with KB Toys, then closed it down. Oh the irony. I think the writing was on the wall a while ago.
Many people online are lamenting the closure of TRU, however it seems many of them never actually went to TRU, but they don’t want it to close either because of overpowering nostalgia. That’s me; I haven’t actually been inside a TRU in years, and the last time I went it was quiet, a little dirty, the people working there seemed like they wanted to be somewhere else, I didn’t find anything of interest, I usually just went to the Target across the street. But I can understand how these people feel, I of all people can understand, and it has also hit me hard, perhaps harder than those who went there as customers. I loved it there, I could tell so many stories, from both the employee and customer perspective, and I am very sad to see it go.
Zoho Writer: An excellent online alternative

I recently gave my opinions on OpenOffice.org’s word processing software Writer. My conclusion was that while they have certainly made improvements over the last twenty years, it still just doesn’t hold up to Microsoft’s behemoth package, either online or off. However, that doesn’t mean there isn’t an alternative for those who seek: I also mentioned in that post I would be reviewing Zoho Writer, the online word processor from (obviously) Zoho, which turns out to be a very competent competitor to Word. It’s not the perfect replacement, but it comes pretty close for everyday use, and then some.
Zoho offers many applications and services, all of which are relatively competent. And I’m not talking just basic office suite stuff either; they have everything from CRM platforms to retail inventory management. For an online service, they have a surprising breadth of applications on order.
As you can see, there is a lot there. For this review I’ll be focusing on their word processor Writer, which I feel is a highlight of their office productivity suite, but it’s important to note the range of capabilities they have, especially as compared to other online options. I also want to mention that their PowerPoint equivalent, Show, is absolutely fantastic as well, while their version of Excel, Sheet, is also very good. It doesn’t quite live up to the rest of the suite in terms of functionality or design, but that’s not to say it’s not good – it is. But it has significant room for improvement, especially considering its less involved and less usable interface, with sparsely-populated toolbars, buried commands, and no sidebar, especially when considering it’s for such a powerful program as a spreadsheet. Indeed, it’s the one instance in which I can say OpenOffice’s alternative, Calc, is the better option, with more features, a more familiar interface, and better design all around.
That being said, Zoho is the superior option for everything else, and OpenOffice doesn’t provide any enterprise functionality or features beyond the basic office suite anyway. Here we’ll be talking about Writer, a name shared with the OpenOffice equivalent (so don’t mix them up!) and it will hopefully give a good impression of how it all works.
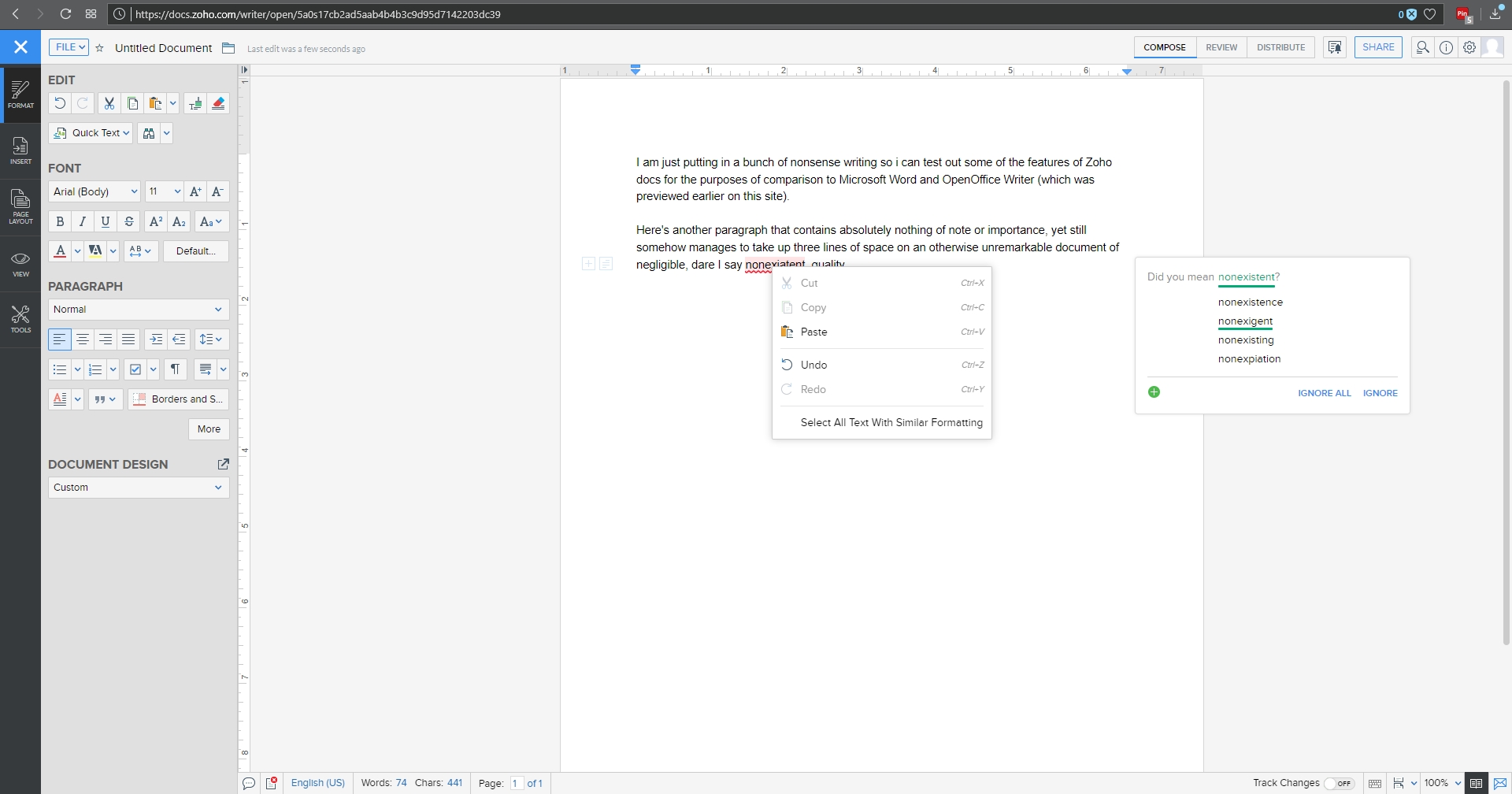
I threw together a nonsense document to mouse around with, and below you can see the spell check, which gives the initial suggestion as well as alternate suggestions, which is nice, although it doesn’t offer meanings / definitions as does Word. You can also see the Format menu in the sidebar to the left with all the functionality you would expect, including Cut / Paste / Format Painter / etc., as well as standard font and paragraph formatting options. Two additional features I think are very useful are the Quick Text option, which allows you to specify a particular piece of text that can be inserted with the click of a button or shortcut key; very good if you frequently use the same phrase or sentence or whatnot in a document. The other nice feature is evidenced by the very faint two boxes you can see in the left margin; the plus and text boxes. See those? You might have to look closely. The box with the plus is an insert menu, and the text box opens a formatting menu. They follow your insertion point automatically, and they turned out to be quite a convenience.
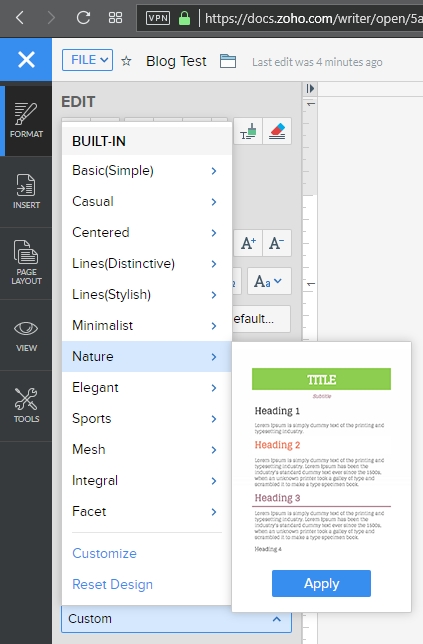
A variety of page layout templates are also readily available, with more available for download and very easy to implement.
Although this document is hardly complex, inserting an image and table is something that can trip up even stalwart word processors, and that was true here as well. Inserting the image was easy and worked fine, however arranging it for word wrap was more problematic. Smaller images resulted in much more layout success.
Inserting a table was also quite easy, and I especially like the live preview it provided as I hovered the mouse over the design options, all of which were neatly contained in the Design tab of the table options window. This is very similar to how Word will open custom contextual tabs that provide additional functionality depending on the specific element you’re working with.
Manipulating the table was much easier than manipulating the picture, which wanted to jump around the page, and even manipulating individual cells was very smooth; everything from changing their dimensions to their color to their alignment and everything in between worked perfectly the first time.
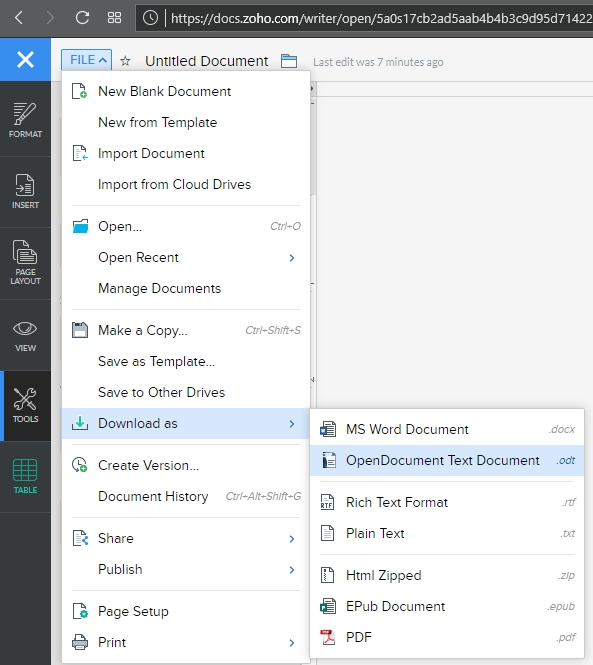
Now is when I need to mention the biggest advantage of (Zoho) Writer over (OpenOffice) Writer: .docx compatibility. OO Writer doesn’t have it, and that’s a huge knock, a terminal knock, actually, against it. With Zoho Writer, when saving a document, you have multiple options: You can save to a cloud service, and Zoho has collaborated with many as you can see (although I couldn’t help but notice the logo for OneDrive is oddly blurry, while the others are very clear), or you can download the file as a Microsoft Word .docx, or even as an .odt file, which is the open standard used by OpenOffice itself.
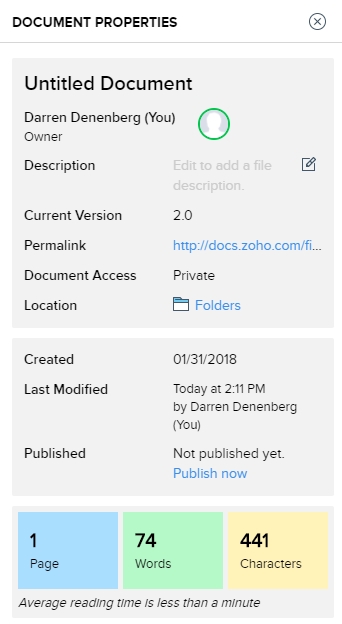
As one would hope, there are also multiple ways to get some statistics about your document. They run along the bottom as one would expect, but I am also a big fan of the Document Properties as accessed by clicking on the ‘i’ with a circle around it at the upper right of the window. Not only does this provide a wealth of information about the document itself, but coming from an HCI perspective, having the page count, word count and character count in individually shaded, easy to see and immediately locate, is genius. In terms of information presentation and information availability it puts those interrelated metrics right next to each other yet separated visually and thereby forces them in a cognitive whole.
Not to get too far off topic, but the reason I’m so enamored with this design choice is that humans, in order to make sense of, and order out of, information and stimuli presented to them, engage in several practices that help them in organizing what they see. One of them is known as Proximity, in which spatially similar images are considered as part of a larger group, even if they’re not related, so when they are related, as these three metrics are, our ability to process them, their meaning and their relation to each other is increased even more. Another is Similarity, in which when considering multiple individual field objects, those that are similar in some dimension, whether it be shape, color, orientation, or whatever else, are considered to be part of the same group, again even if they aren’t. Those are two reasons presenting that specific document information is so brilliant – it addresses the way we as humans process information.
Consider the Windows logo below. This is an example of both proximity and similarity. We consider the logo as a single shape because the four smaller squares that comprise it are both similar and proximal.
This is the Writer document properties pane, that uses these concepts to such great effect.
It even estimates the average reading time. There is nothing I don’t like about this information window, it’s one of the best interface designs I’ve ever seen, and I’ve seen a lot.
Before I just put up the rest of the menu dialogs for your perusal to give you an idea of how they’re implemented, I also want to address a nice usability touch they have incorporated in the form of a support icon. See that little blue envelope there way on the right hand side?
That’s the Writer support icon, and it opens up a window that allows you to offer feedback or ask questions directly. For a free service, that’s pretty remarkable. It really gives the idea – true or not – that they are at least receptive to feedback or requests for help. I was very surprised by that, and pleasantly so.
As you can probably tell, I think Writer is a great program. It’s not often I get to gush over software, but this company is so unknown, comparatively, yet they have such a well-designed and functional, free service, I’m surprised we don’t hear about it much more often. According to their webpage, they are a private company but one with five thousand employees! They hold user conferences and expos – that is not small time, yet their name recognition, even with millions of users, is small. If I may be so bold, even sacrilegious to some, I’ll even go so far as to say it destroys the offerings from Google. The only service that can compete is Microsoft’s Office 365, and even then it’s just a little better, plus Zoho integrates with all of them anyhow. Zoho has really created something great, and I encourage anyone interested in alternatives to standard office suites to give it a try.
Here are some functional dialogs if you’re interested in seeing all the options available before taking the plunge.
[Best_Wordpress_Gallery id=”8″ gal_title=”Zoho Dialogs”]
Has Firefox opted you into any of its studies?
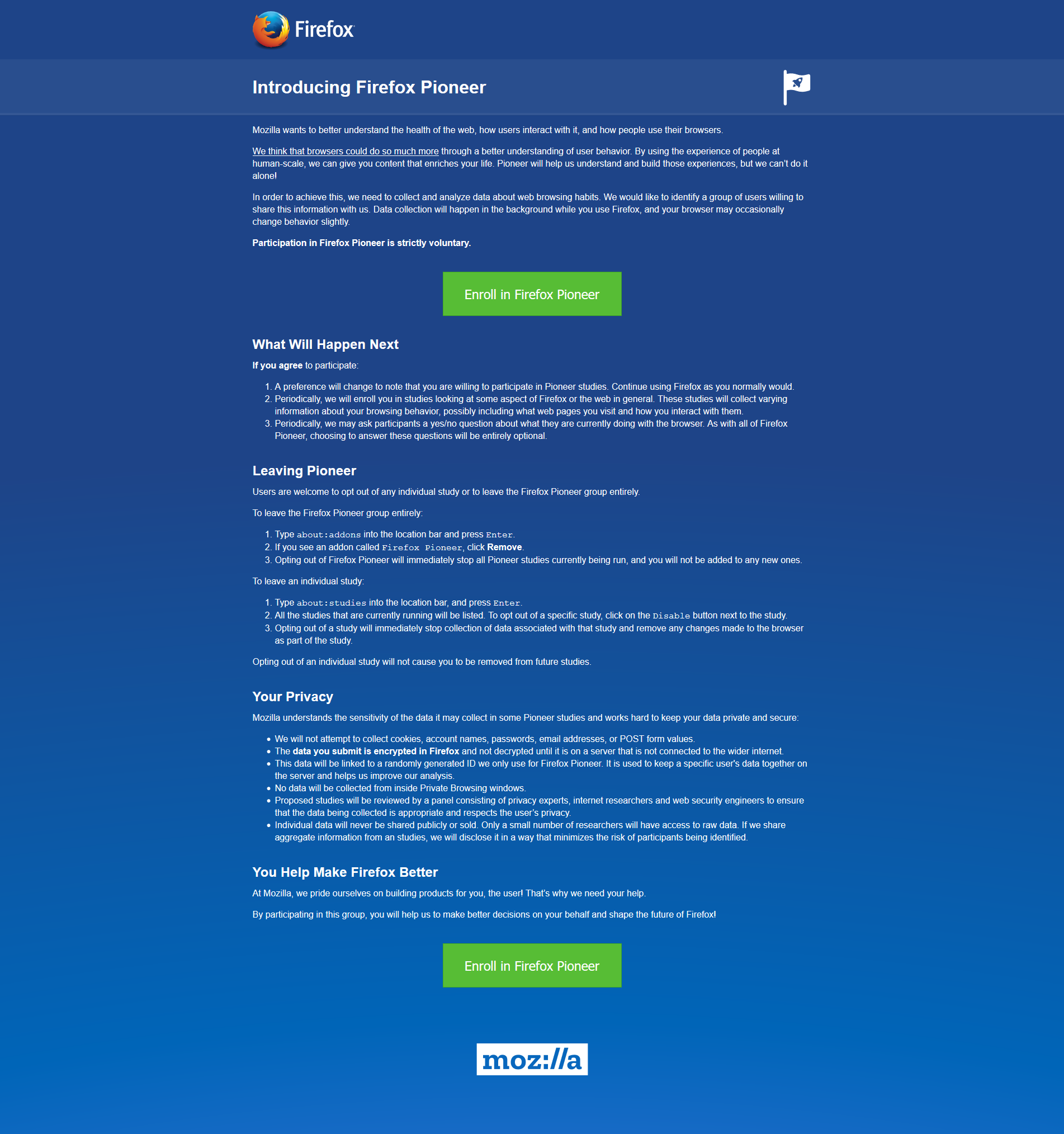
Remember my previous post that talked about the fantastic new version of Firefox, especially the full-screen screenshot capability? I still haven’t adopted it as my main browser, but I was so impressed with th overall changes that were made, I’ve found myself using it more and more; certainly more often than I have in the past. High five for no more memory leaks! Anyway, when I started it up today, it opened to the screen you see below. I was intrigued, especially considering the great improvements they’ve made so far, but as I read through it I also became a little curious. It’s talking about tracking us for usability study purposes, which I’m completely for, but is there anything they perhaps are not telling us? I had no idea the drill down that was about to happen.
This is a new initiative called Firefox Pioneer, which aims to discover how people use their browsers, as well as what they vaguely refer to as ‘health of the web.’ They are careful to note that you need to opt in, which is good, and they are pretty clear about what they will and will not do, and what you can expect in terms of privacy, monitoring, opting out, how private sessions play in, and so on. I do get the feeling they are striving for high-level transparency here and acting in good faith, but perhaps a deeper dive into what they could do is warranted.
I should also mention that while Firefox allows for full page screenshots, that option was not available here. I had to open the page in Opera, save it as a pdf which Opera allows compared to Firefox’s screencap capability, open the pdf in Firefox, and then I could save a full-page screenshot. Very curious, but a triumph for ingenuity.
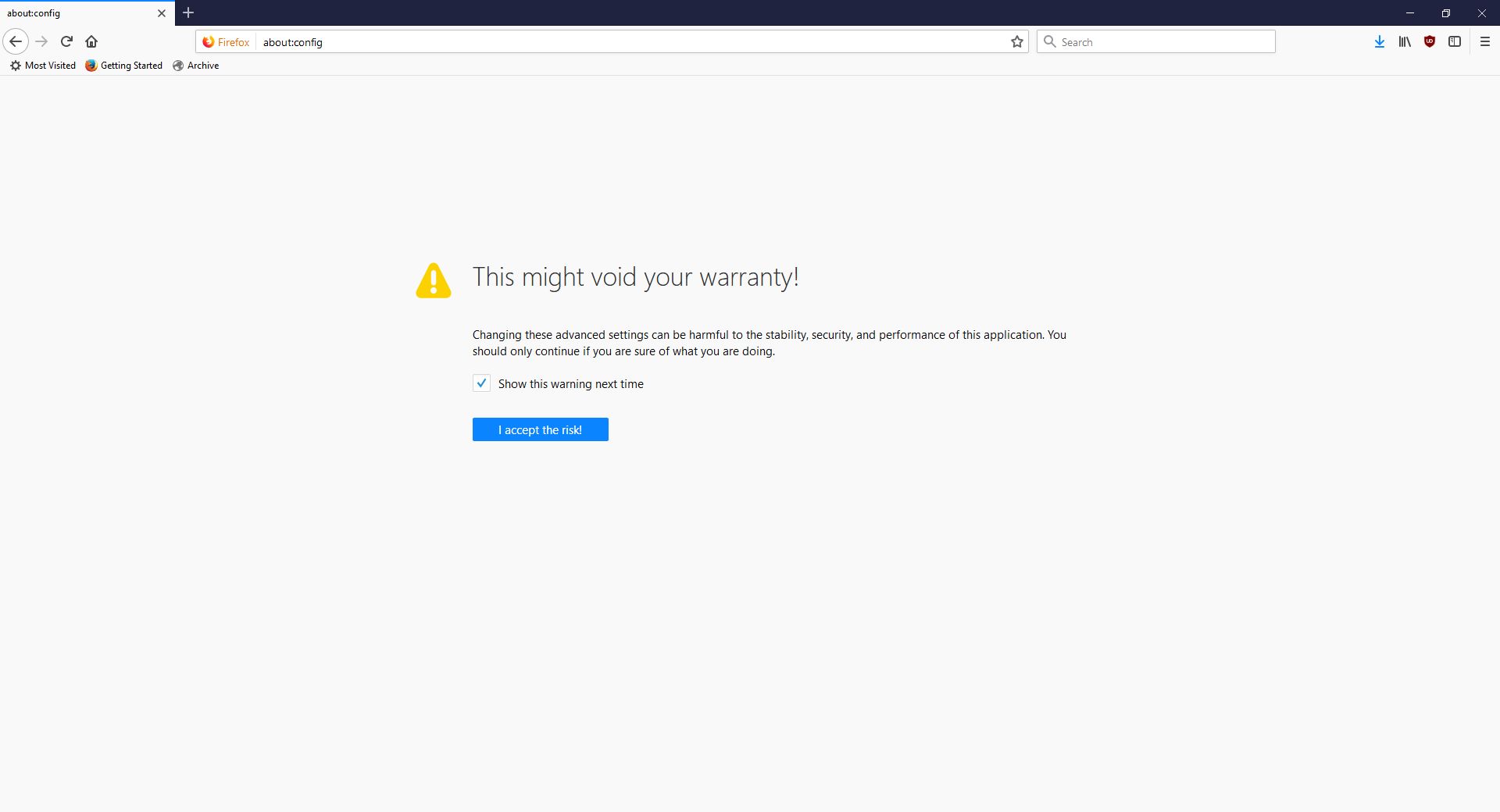
As the page indicates, you can type about:studies into the address bar and see which studies you’re part of, which have completed, and which are available. In fact, you can type about:[topic] into the address bar to discover many interesting things. To see how extensive this capability is, you can see a list at this link. For a real fun time, try about:config – it shows this not at all scary warning, which is really just trying to be funny before letting you access settings. I would normally be for this, however it’s incredibly unclear as to what’s going on if someone isn’t familiar (it fooled me too), especially as it says ‘this application’ and not ‘Firefox.’ Why the pseudo-third person?
Clicking ‘I accept the risk!’ takes you to a configuration page that isn’t much better in terms of readability or functionality.
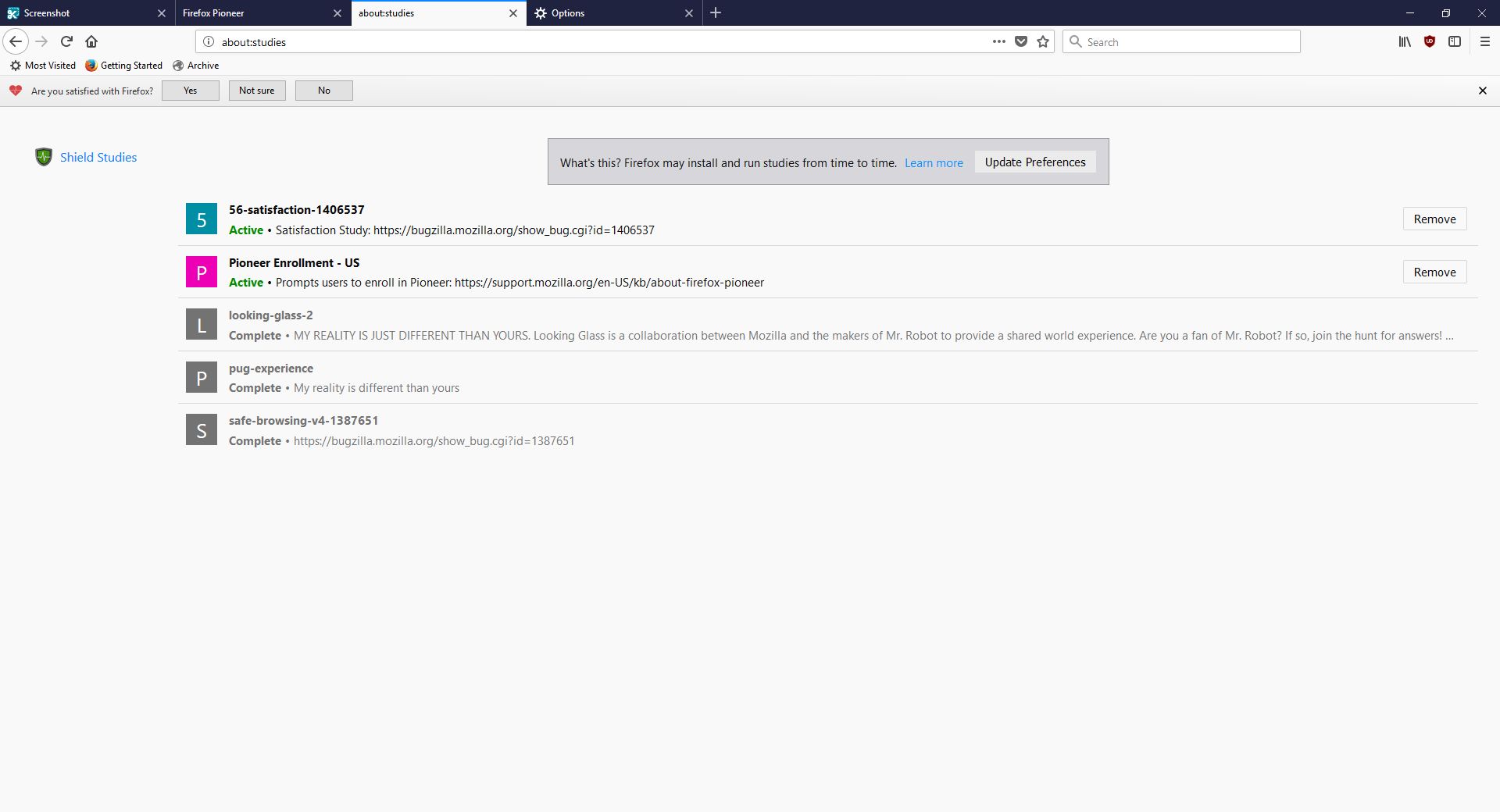
I don’t usually check this kind of thing, but I certainly should. We all know that companies use your data for many things, sometimes not asking first, so it’s important to keep an eye on what any program you’re using is doing. Typing about:studies showed me this screen, which I have to admit got me to wondering what exactly has been going on behind my back:
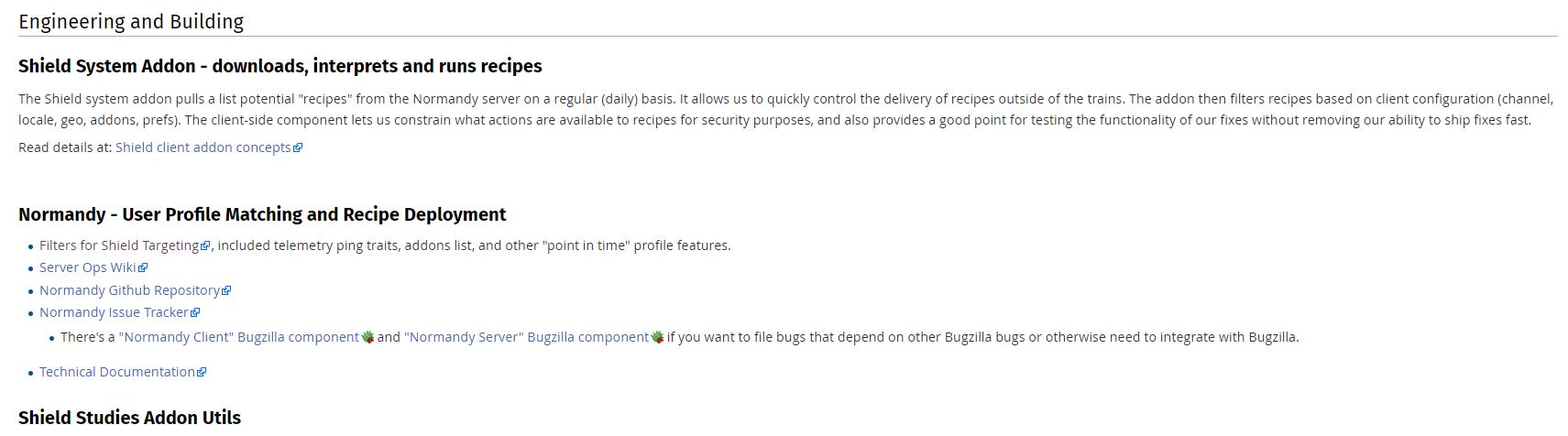
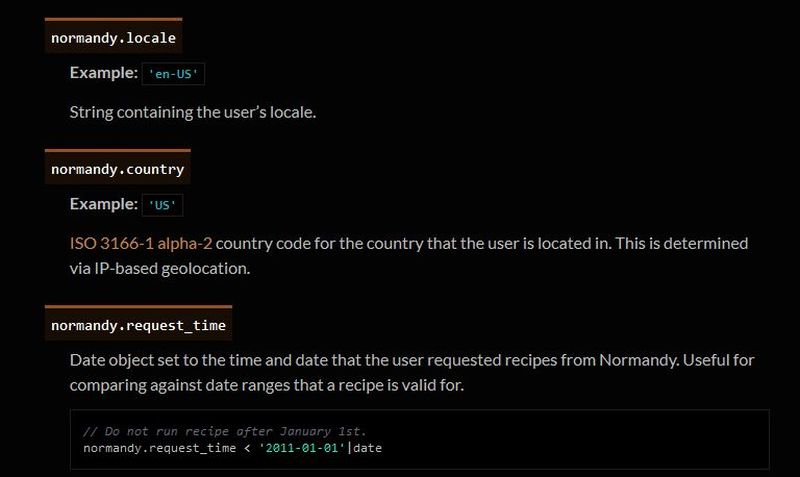
A collaboration between Mozilla and the creators of Mr. Robot? Someone’s reality is different than mine? What is going on here exactly? I clicked on Learn More and was taken to their SHIELD page where I learned all about their SHIELD studies, which they claim are to test new features, however from the original request it’s clear they test more than that. I also can’t figure out why it’s capitalized in such a way; I found no evidence it’s an acronym. A deeper dive led me to another Shield page where it’s maddeningly no longer capitalized, and that’s where I found, towards the bottom, a very concerning entry called ‘Normandy – User Profile Matching and Recipe Deployment.’ I wasn’t completely sure what that meant, but it stood out as sounding perhaps not so good. Just the name is curious: If you’re not familiar, and you should be, Normandy happens to be the location in France where the United States, Britain, Canada, and some of France itself launched the D-Day invasion against the Nazis in 1944. Did you ever see Saving Private Ryan? The opening scene was Normandy. I can’t help but wonder why Mozilla has named this bit of its process in such a way. It may be common knowledge, I don’t know, but it was new – and enlightening – to me.
You’ll notice the first item there, “Filters for Shield Targeting.” That took me to another interesting page, the very first paragraph of which states how certain users can be pegged for recipe execution in their browser, and the means by which that is done has access to location and locale (I’m uncertain as to how those differ in Mozilla parlance). It’s further down the page that you begin to see all the ways you can be tracked and monitored.
I was going to take a screenshot and crop in the sections that were most troublesome, but there are SO MANY it simply was not possible. To give you an idea, here’s what a screenshot of the page looked like in my image editor. I should also add that from a pure design perspective, they are really not using space efficiently.
So there’s a Normandy server, and Normandy is also an object that contains what they call ‘general information’ about the client. Client in a case like this should indicate the browser itself, not the person using it, but separating the two is not so easily done, and as a designer / developer, you’re ultimately trying to learn about the user, about their wants, needs and habits, so you can provide a better product. I have no problem with that, and in fact am completely on board with their Heartbeat initiative, but that is relatively benign.
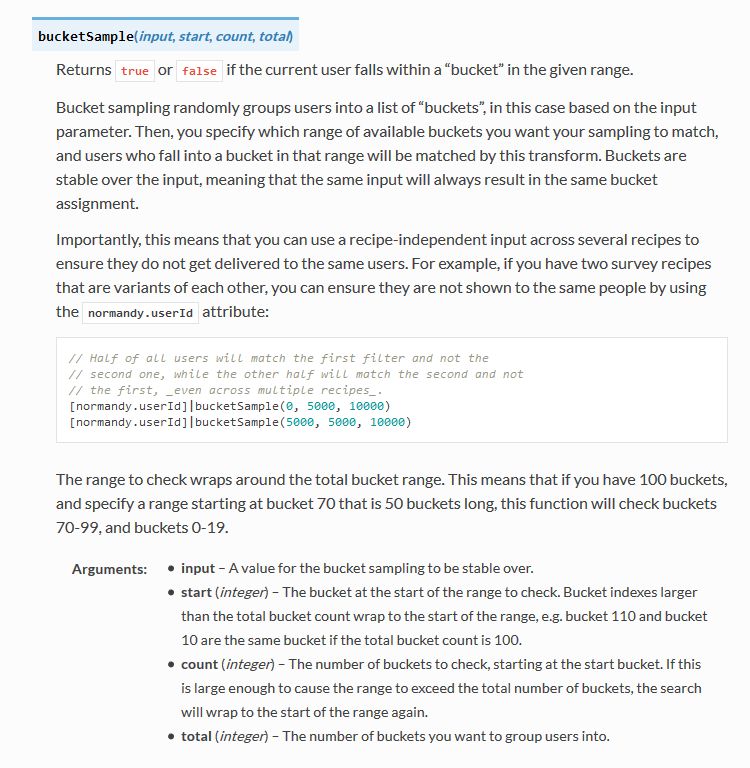
Anyway, back to the above screenshot. They can track a lot, and in the crop below, you’ll see they do something interesting called bucket sampling. I’m intrigued by what this would be used for and how / why / when / etc., so I will have to dig even deeper. I’m guessing it’s some kind of parsing via demographics / usage statistics, but I’m not completely sure. I only found one mention of it on Mozilla’s site, on this page towards the bottom under the heading “Filling the Gap,” but it does lend credence to my assumption. While there’s no formal method known as bucket sampling, it’s something we do, in effect, all the time. I’m looking at you, marketing!
So what does all of this have to do with the study that started this whole post? To be quite honest, this rabbit hole didn’t tell me anything I, or any of you, didn’t already know: It’s very easy to track you online, and not just the websites you visit. Where you are, what software you use, what OS you have, whether you’re a new user or experienced, how many mobile and desktop clients you have, how long you stayed at a site, they can even track if you’ve enabled Do Not Track!
And while this sounds like a conspiratorial, tinfoil-hat rant, I actually am not overly bothered by it. I don’t do anything outrageous online other than download Sega Genesis ROMs, because I’m dangerous and like to live life on the edge. But other than that it’s all pretty boring. My issue was mainly that Mozilla may be opting us in to studies without formally informing anyone, and that I just can’t get behind. This was originally going to be a very short post that I thought could be whipped up in about fifteen minutes, but it instead turned into a downhill slalom.
If you’re interested in reading more about Normandy, Mozilla has a helpful website where you can learn all about it and what it can (and does) do, and it really is an interesting, dare I say fascinating, read. http://normandy.readthedocs.io/en/latest/
Oh, one ore thing – In the latest build of Firefox, Mozilla has also made individual cookie management much more cumbersome. I don’t use that feature a lot, but it is definitely not something people should have to go in to the developer console to access. I love the new Firefox, but this isn’t good – user control should be at the center of all commercial software development. Get it together, Mozilla.
Fixing a component install error in Visual Studio Community 2017 (hint: It’s really easy)
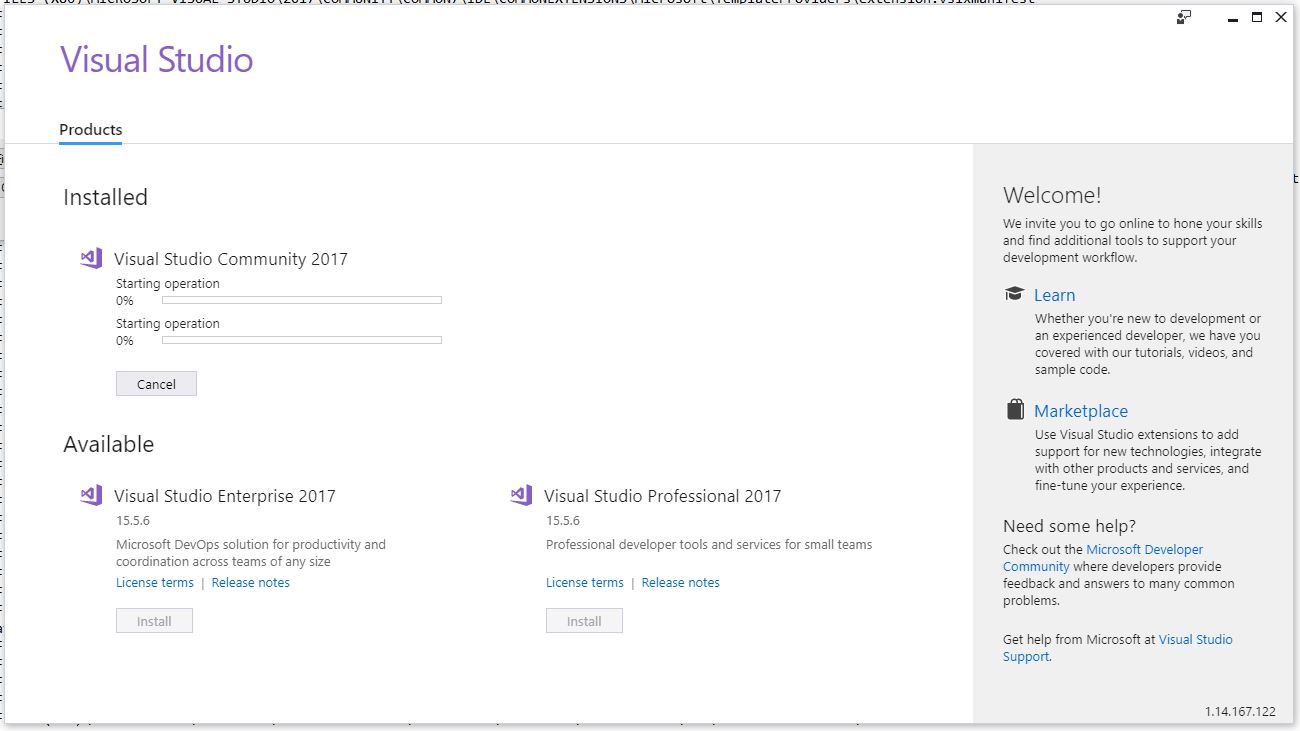
I recently noticed in the notification window of Visual Studio Community ’17 that there were some Azure-related updates available. Normally these updates lead to an uneventful experience in which I approve the updates, VS takes a loooong time to download install said updates, then everything moves forward as planned. This time, however, was slightly different so I thought I’d bring you all on my journey of discovery and illustrate why Visual Studio’s attempt to help me figure out what went wrong was so unhelpful. Even so, it’s an easy fix that I’m guessing many of you could figure out anyway. Indeed, my approach takes the slightly longer way round.
The story begins with the update notifications. This is a very common thing to happen with this particular Integrated Development Environment (IDE), and now that I think about it, I can’t recall a time there weren’t updates to be had. Anyway, as I mentioned they’re normally uneventful, and these two were for components I don’t use too terribly much – Azure Data Lake and Stream Analytics Tools, and Azure Functions and Web Jobs Tools. The former are tools to aid and assist with the streaming, gathering, and analysis of the massive amounts of data gathered from IoT connected devices, and that is an area in which I have significant interest, so these tools will be useful for me soon (I hope). Azure Functions and Web Jobs Tools are of less interest to me, but I can’t have an incomplete update hanging in the air above me. So, without thinking too much about it I clicked the notification, clicked on [Update], and went about my business.
As expected, the process began without much of a hitch.
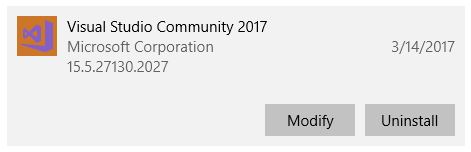
I should mention that when it comes to Visual Studio, you don’t ‘update’ or ‘patch,’ you instead ‘Modify.’ All just a big semantics issue. Anyway, although things had gone well up to this point, that was about to change.
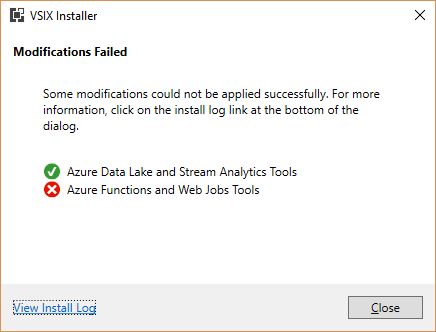
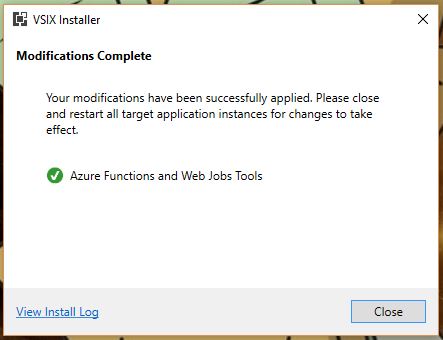
So the Data Lake and Stream Analytics tools installed fine, but the functions and Web Jobs tools was another story. I don’t even need those, and I probably should have let it go, but I just couldn’t. That red X would have haunted my dreams.
The obvious next step was to check the install log, as the Installer so helpfully suggested. Speaking of the installer, and if you’re interested, VSIX is a method of deploying updates to Visual Studio, and does so in the right place with the right components and so on. It’s a compressed file, and you can even rename a VSIX file to .zip and extract it. Just wanted to get that out of the way.
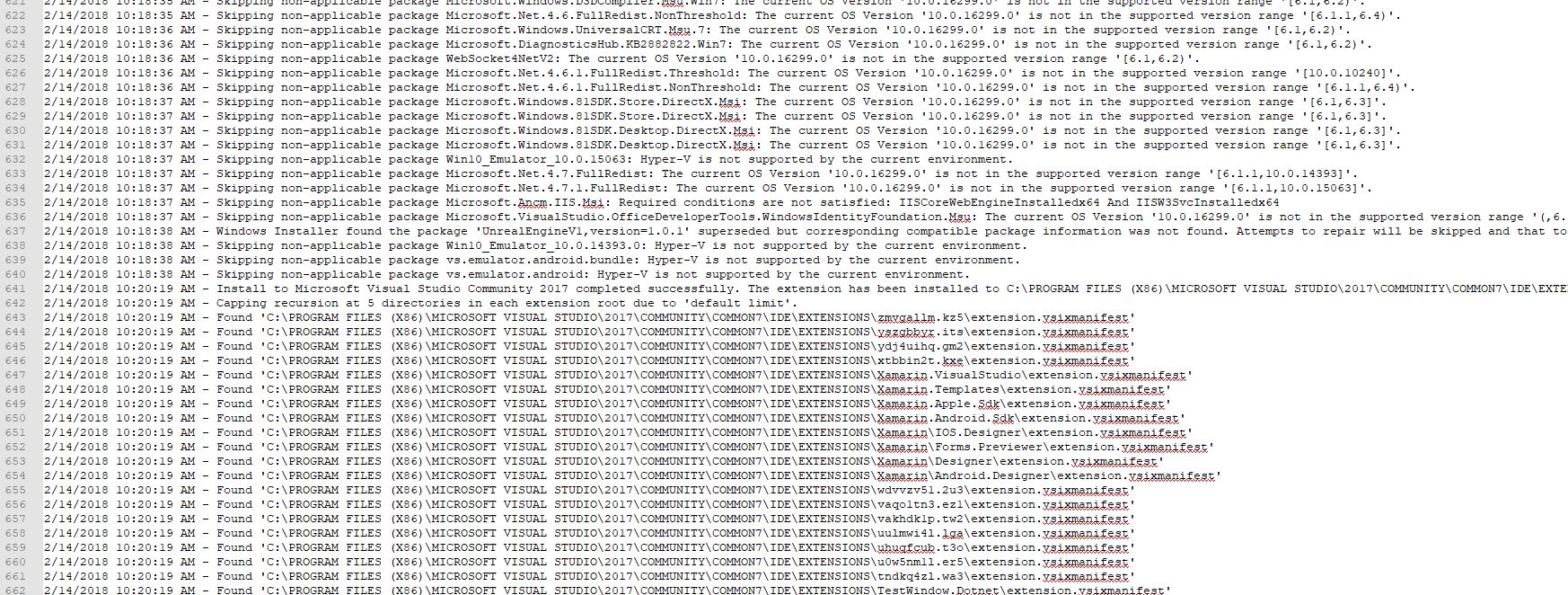
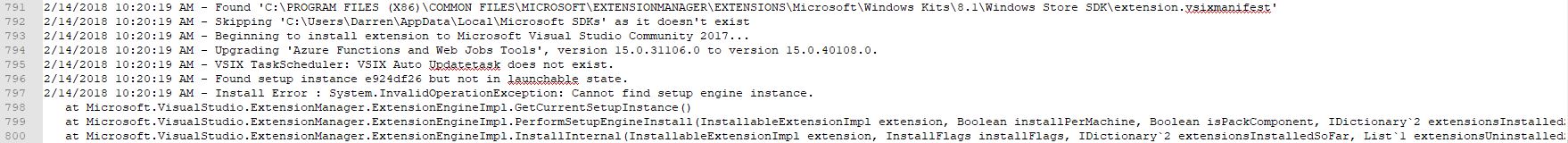
I clicked on “View Install Log,’ and the result was a log that was a breezy 865 lines long, and mainly, but not entirely, comprised of stuff that looked like this:
This log punches you in the gut twice, because A) You have to find the part that identifies the problem in those 800+ lines all on your own, and B) the part that identified this particular problem was all the way at the very end. Luckily, ctrl-F helped out significantly here.
Luckily, I knew, or at least suspected, that from here it would be easy. That the update task didn’t exist and the setup instance was not in a launchable state indicated to me that there was a disagreement between the installer and Visual Studio, and not that some fatal, unrecoverable error had happened. Fortunately, my suspicions turned out to be correct and it was really easy to fix. In fact, I could have just done it from within Visual Studio, but this is more illustrative. At least I think it is. Maybe it’s not.
I didn’t even need to go full control panel on it. I simply went in to the apps section of settings, scrolled down to Visual Studio, and selected ‘Modify.’
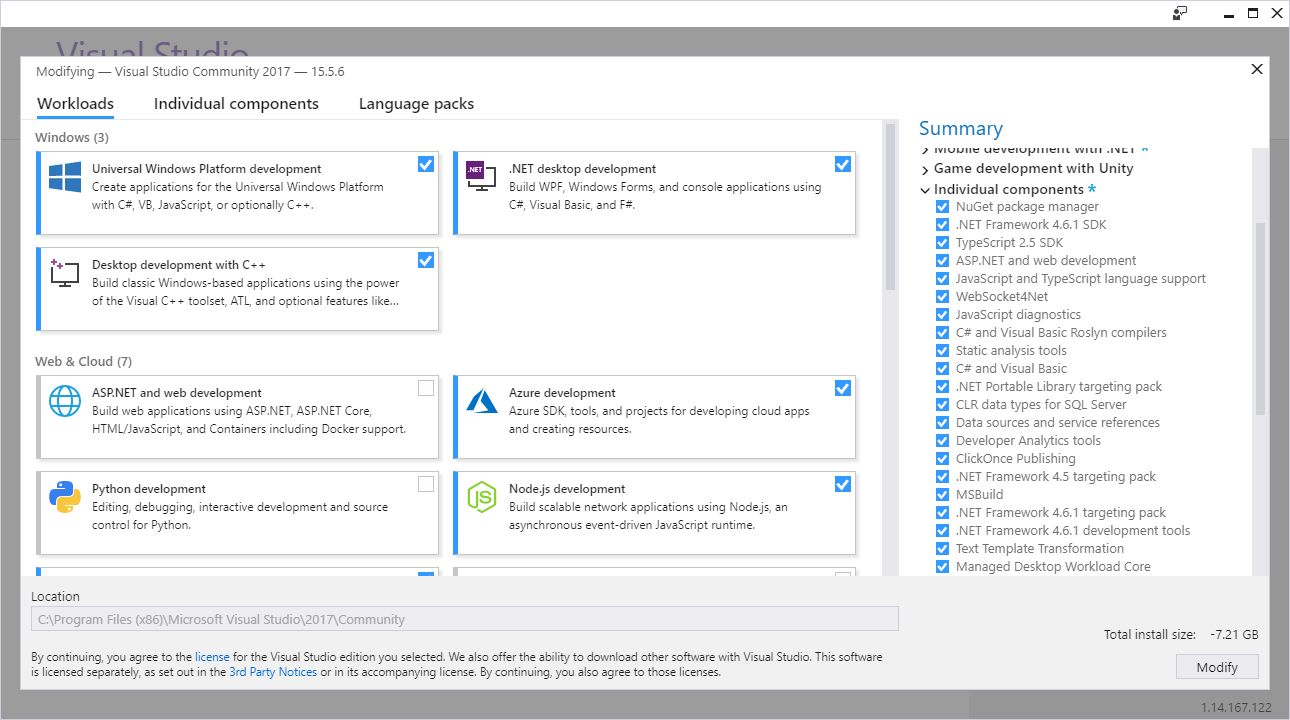
That brought up the Modification window with the ‘Workloads’ tab highlighted, but we want ‘Individual Components.’
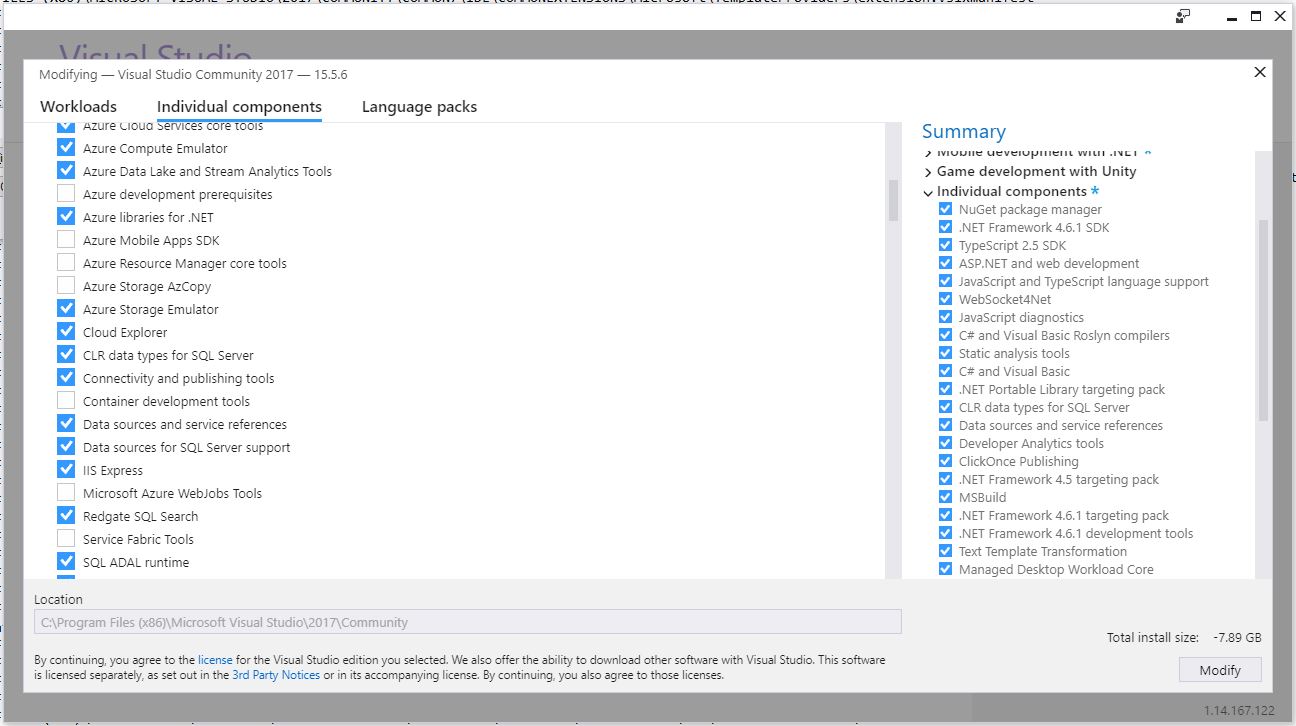
You’ll notice that ‘Microsoft Azure WebJobs Tools’ isn’t highlighted, so easy fix. That’s also the reason I mentioned earlier that it could easily be repaired from within VS itself. Clicking that checkbox caused almost all the other checkboxes to become selected, and after clicking [Modify] there in the lower right-hand corner, the long, slow update process began anew!
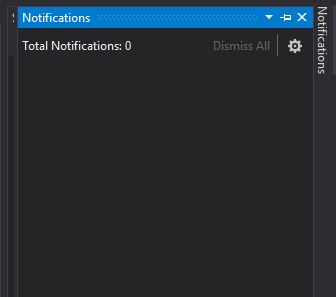
It was at zero percent for a long time, but that’s normal for Visual Studio. Its updates are never a quick thing. After it chugged along for a while, success!
Remember, I don’t actually need these components, but I was not going to let the VSIX installer win, and now I could raise my head in triumph. Plus, I can experience – for a brief moment anyway, if I know Visual Studio – the blissful Zen of the empty notifications window.
When it comes to a failed component update, I have seen others suggest uninstalling and reinstalling Visual Studio, clearing caches, even making changes to the registry! I have never needed to do any of that for any kind of installation or update hiccup. I don’t know why people think that, especially when a straight repair or modify, as shown here, always works. This is not an advanced technique or a hidden trick Microsoft doesn’t want you to know about; it’s a standard, Occam’s Razor approach that should always be the first line of defense and action for this kind of thing.
If this helps anyone out there avoid all those unnecessary machinations, then I’ve done my part.
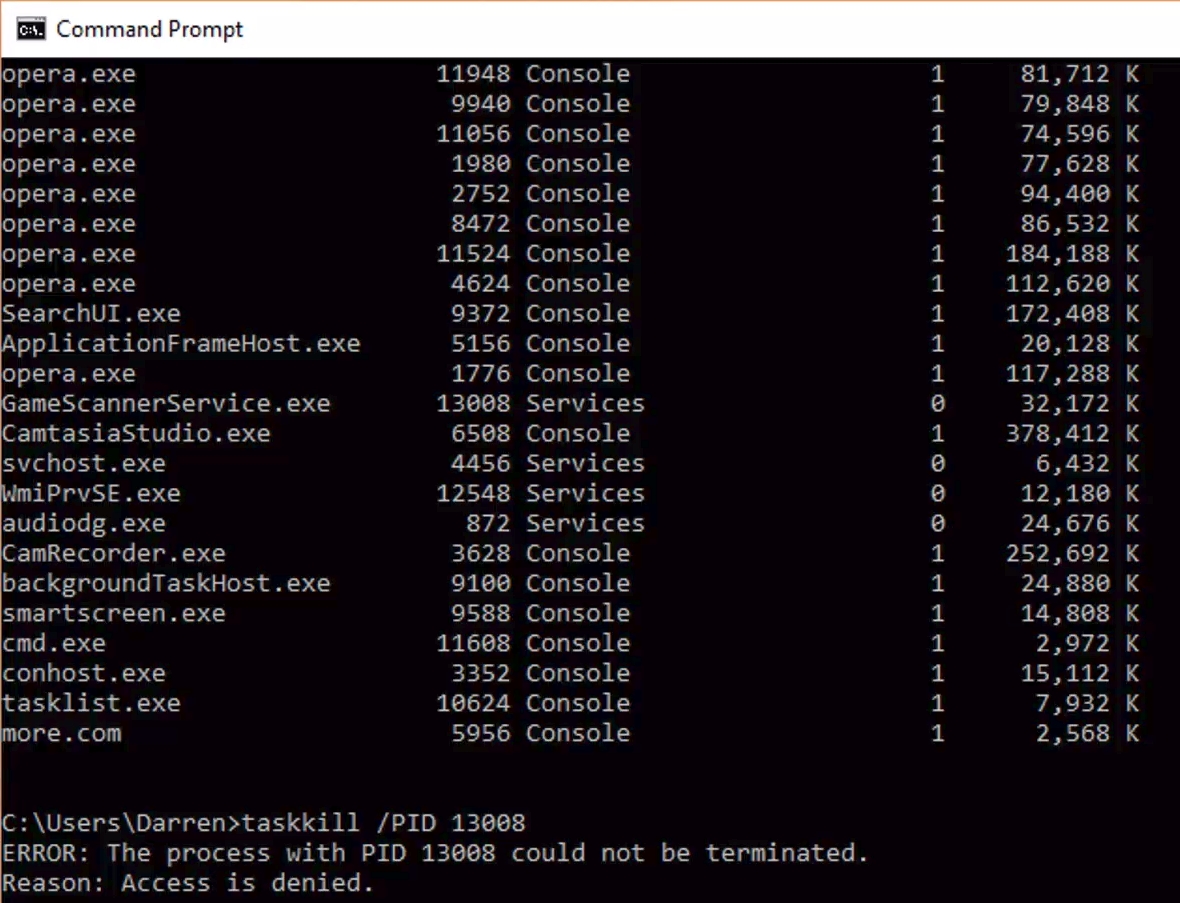
How to kill windows tasks, even those that just won’t die

I recently created a video that shows how to kill tasks via the command line, and if that doesn’t work, how to kill them via Process Explorer, and if that doesn’t work how to disable them using the Services window. It’s embedded just below, but if you’re not in a video mood, fear not! I have summed up its contents, although the video shows you the steps and comes complete with witty commentary.
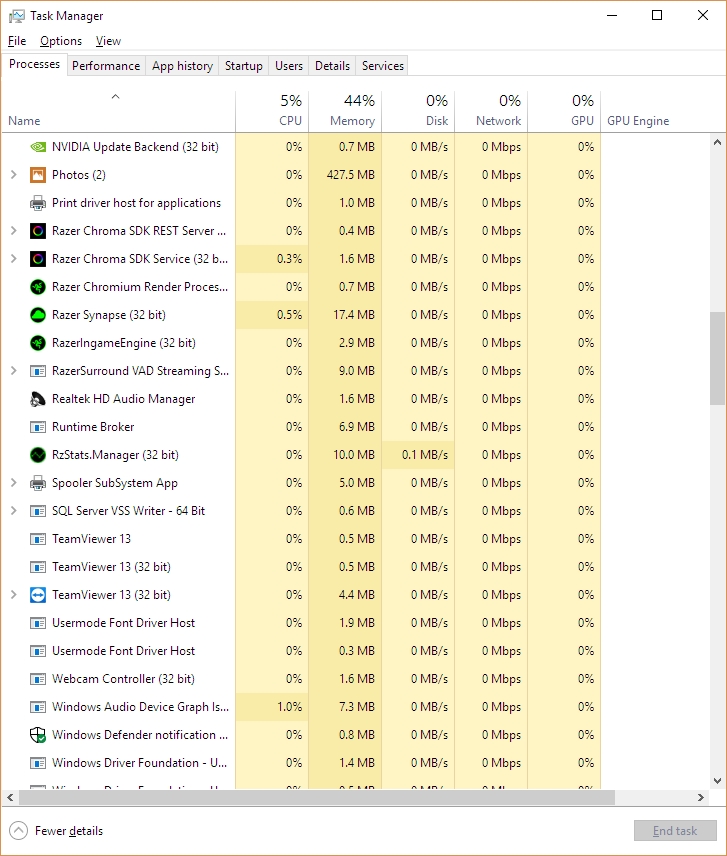
If you’re running Windows, any version of Windows, you know there are what seems like thousands of things going on in the background. All you have to do is bring up the Task Manager ([Ctrl]-[Shift]-[Esc], or the well-known [Ctrl]-[Alt]-[Delete] if you’re old-school and enjoy the extra steps) and you’ll come face-to-face with the process party happening inside your machine.
As you may also know, each of those running tasks requires some of your machine’s resources; sometimes a little, sometimes a lot, and you can see in Task Manager how much of each resource each process is using. If the process is something you don’t use or don’t need, then it’s not a bad idea to stop the process and recover whatever amount of system resources it’s hogging to itself, and it even turns out that while taking the above screenshot I happened to notice Windows’ Photo App, Movies & TV app, and Messaging app were taking up a lot, so away they went! Right-clicking brings up a menu that allows you to ‘End Task.’
But that’s also where an insidious problem lies. Sometimes, when you right click and select End Task, the task just doesn’t end. This can manifest in a couple of ways: The task may continue to run, mocking and taunting you to click End Task again, reveling in your failure to stop it. It might stop for a moment, only to reappear a second later, better, stronger, faster (not really better or stronger or faster, but it will reappear).
This even happens when using the command line to kill tasks. Normally this is done by listing the running tasks using tasklist, then, once the Process ID (PID) is known, using taskkill /PID actualPID, however even here that doesn’t guarantee a termination, with a similarly mocking response from your system.
Why does that happen? The main but not necessarily only reason is that it is actually part of a complex hierarchy of tasks that prevent it from being shut down. Either it is a child spawned from a parent process and upon being stopped, the parent just restarts it, or it’s a parent process that can’t be terminated because we can’t have orphaned tasks.
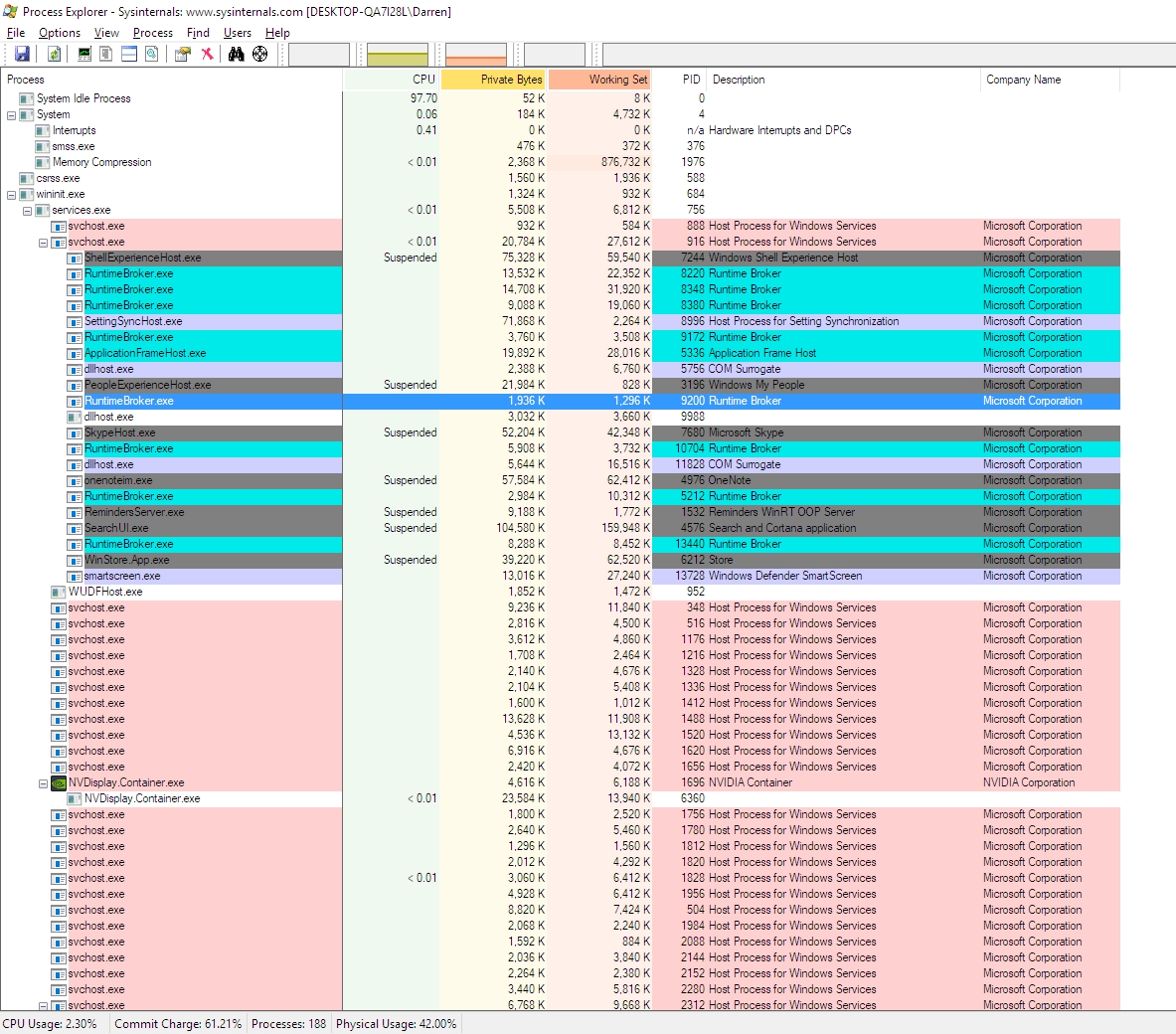
To determine which of these is the case, I am a big fan of Process Explorer, part of Microsoft’s SysInternals software suite that helps maintain and monitor Windows. If you click on the link, you can see in the left-hand sidebar the other packages available; They’re quite comprehensive.
Process explorer shows you everything that is going on, how many resources are being used by each process including specific and shared memory, the Process ID (PID), the name of the company that developed the software, it color codes by category, it’s a great program that shows a lot and really gives an idea of not just what is going on but how it all relates.
You can see that some processes are child processes and some are parent processes and whether you can or can’t kill a process is very dependent on the nature of that hierarchy. Trying to stop a task even here will prove futile as the hierarchy is the same. Interestingly, in Task Manager right clicking gives the option to End Task, while in Process Explorer it gives the option to Kill Task. Hmm. The deeper we go, the more violent we get.
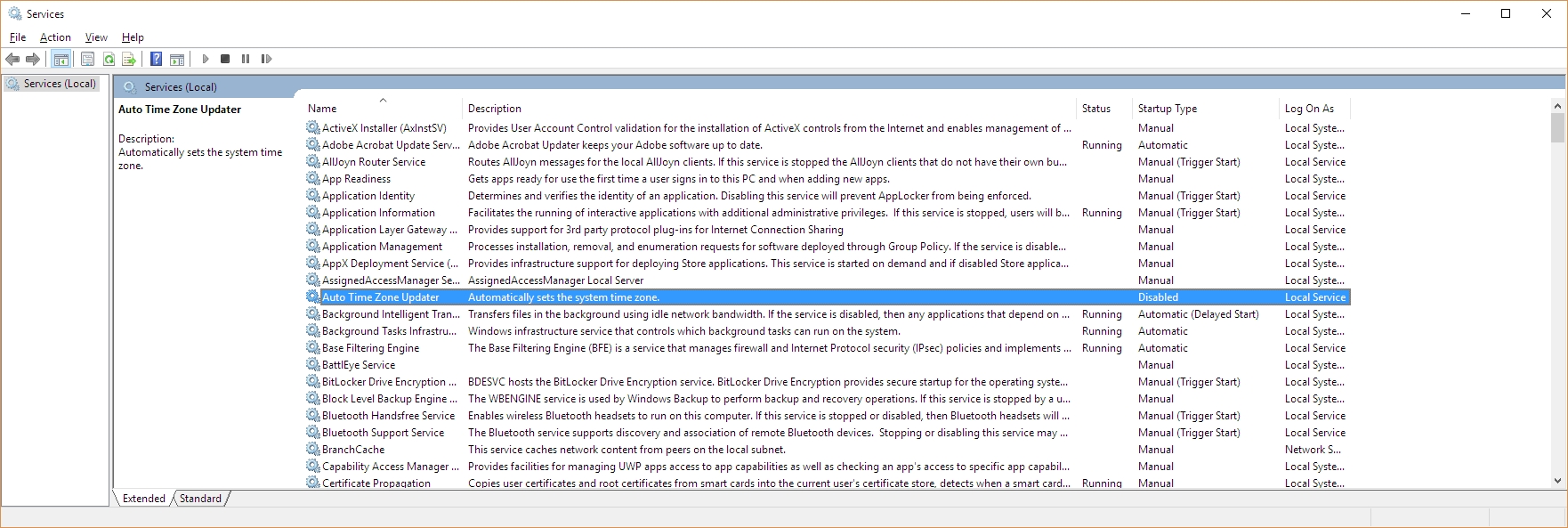
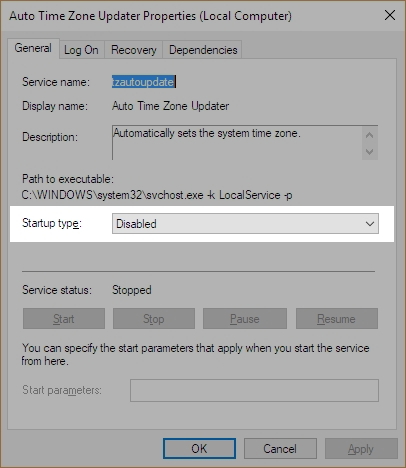
Ultimately, if you really want a process to not run, you should first make sure it’s not something you need. Google, even Bing, is your friend. If you are certain the process is just leeching resources, then you’ll have to go into services.msc, which you can run by typing it in to the search bar there by the start menu, and disable the service by right-clicking the service and selecting Properties, then Startup Type. Don’t set it to Automatic, obviously, or even Automatic Delayed Start, but also don’t set it to Manual, because then it will just start up again if the system decides it’s needed. Be sure to set it to Disabled.
That will stop the process from starting up, even if the system thinks it should. Remember, though, that if you *do* end up needing the service, you’ll have to go back into Services.msc and start it up yourself again, as this shuts it down completely. And I have to say it again: be careful about disabling processes. If you disable one that you need, or worse, the system needs, you may find your device acting very strangely, or in a worst-case scenario, software or even hardware not working at all. Even if you don’t disable anything, this is a good way and a good opportunity to learn what your system is actually doing.
Russian botnet master nabbed in Spain, extradited to US
This is a story that has been ongoing for some time. Pyotr Levashov, a well-known and well-established Russian cybercriminal who was arrested in April of last year (2017 if you’re reading this in the distant future – welcome alien overlords!) while vacationing in Spain, has finally been extradited to the U.S. Apparently cybercriminaling does pay well sometimes. The arrest was based on a formal U.S. Department of Justice indictment against him for, among other things, operating the Kelihos Botnet, a long-running, expansive, global botnet that bombarded the world with all kinds of spam for nonsense like get-rich-quick schemes and enhancement medications; if you’re interested, and you should be, you can read the DOJ press release about the indictment and the actual search warrant that allowed for their infiltration of the botnet.
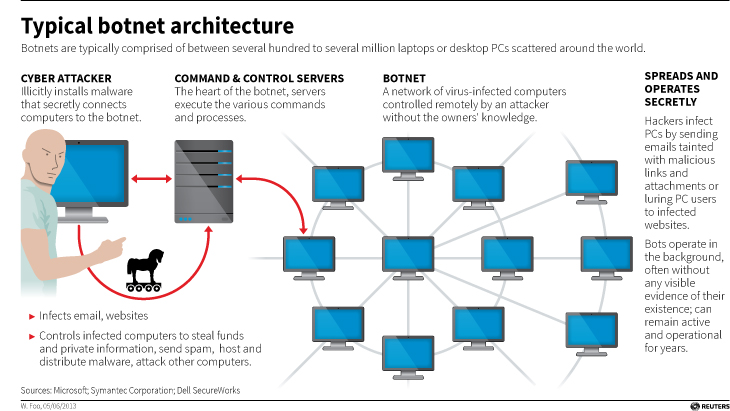
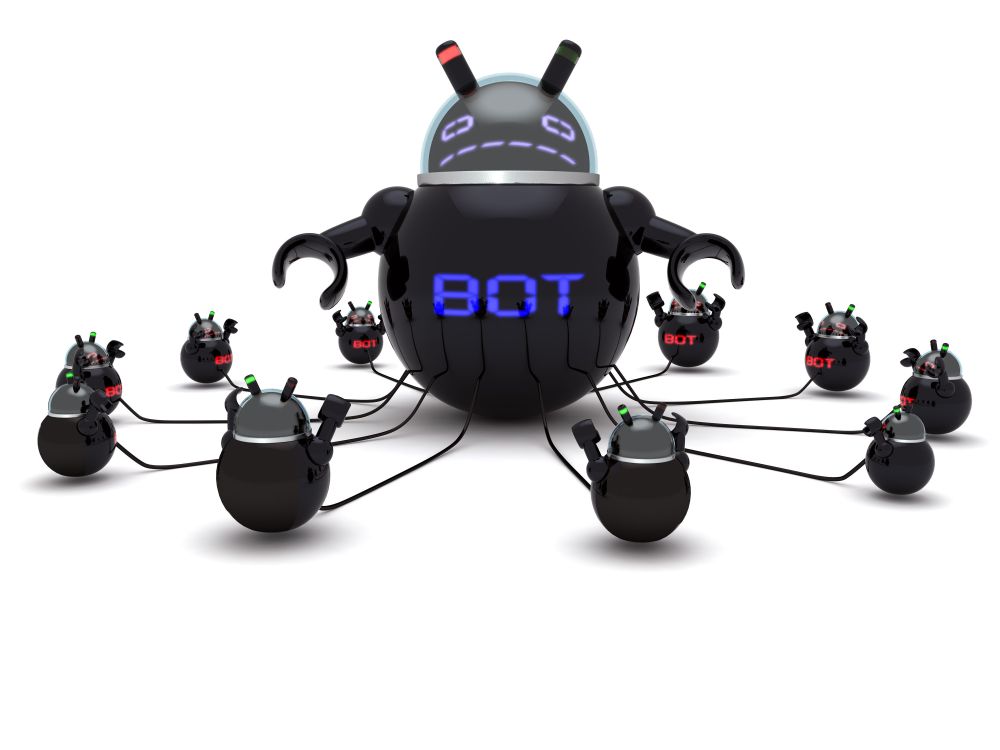
Before we continue, let’s talk about what a botnet is. When malware, or bad software (get it? Mal ware?), is surreptitiously installed on your machine, either through a drive-by attack in which it’s embedded in a Flash ad, or you click on a link or file from a rogue email, or one of many other attack vectors, it will use your machine to carry out tasks without your permission, involvement, or even knowledge. And just to be sure, those tasks it’s carrying out are bad. It can use your machine to send spam, participate in DDoS attacks, store harmful or illegal files, and many other unethical / criminal activities, all without you ever being privy to what’s going on. When that happens, your machine is what’s known as a zombie computer, or more commonly, a bot. Now, imagine hundreds of thousands of these infected machines all acting in unison, for a common goal or under a central control authority. That’s a botnet. Here’s an effective graphic from Reuters that illustrates the architecture of a botnet.
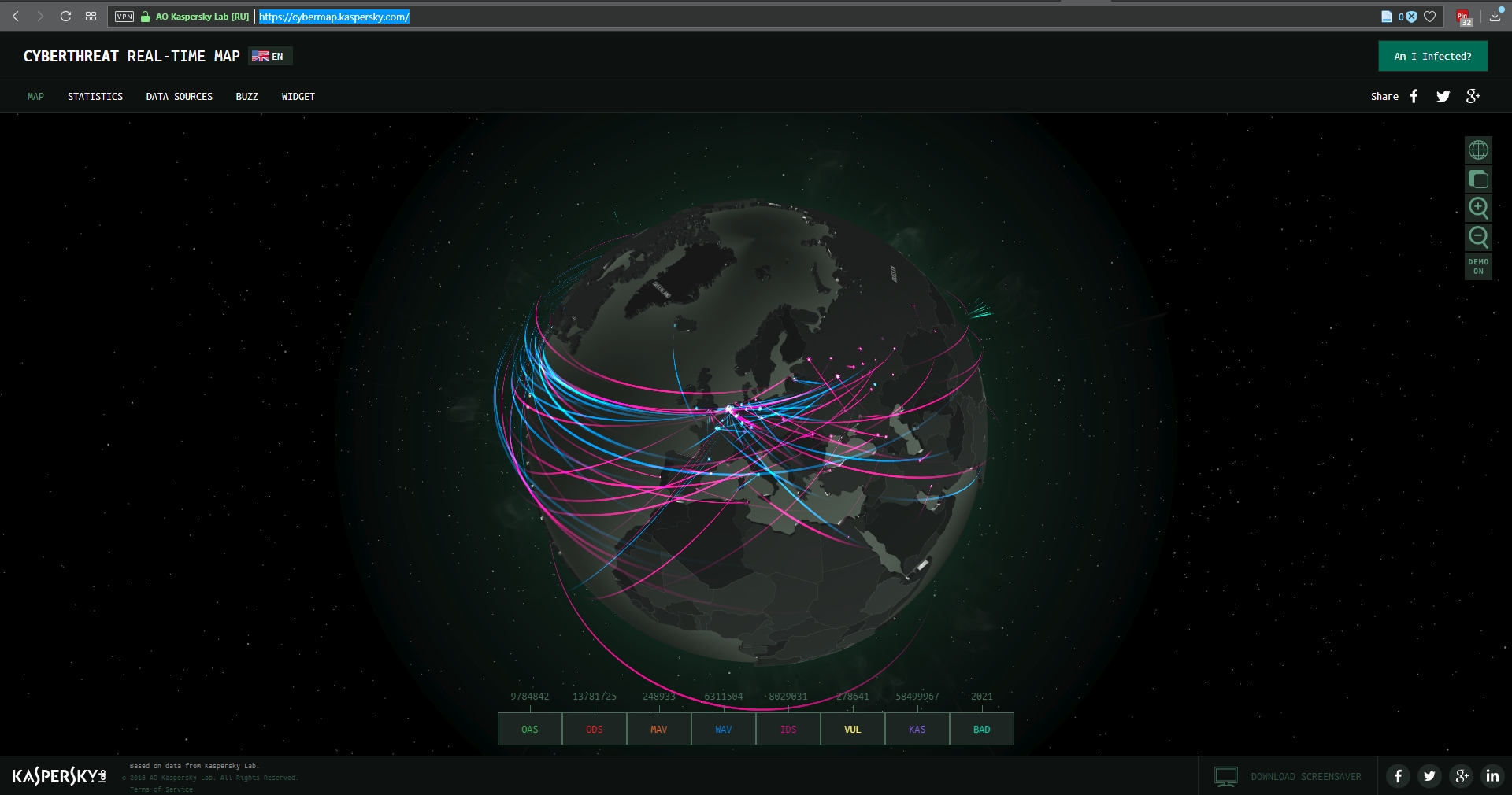
I wanted to embed an interactive map from Arbor Networks that shows real time attacks happening right now, and provides historical data, but their embed code which uses iframes doesn’t work on WordPress. I find it strange a security firm would still be supplying iframe embed codes, but who am I to judge? No matter; there are other sites that provide similar information using their own honeypot networks, such as Kaspersky’s real-time threat map and the well-known Norsecorp map. Actually, I had intended to use Norsecorp’s IPViking map, however it is now run under HP’s banner, although powered by Norse, and I simply couldn’t get it to work in any browser. Their map linked above works beautifully, though.
There are several interesting facets to this case: The first is, this guy has been around a long time and was one of the bad actors behind the Storm botnet that first manifested all the way back in 2007. That botnet was eventually dismantled by the combined efforts of Microsoft, malware firms, and the feds, a partnership and collaboration that continues to this day. We’ll come back to this particular botnet soon, because the architecture of these things is going to become important.
By soon, I mean right now! Another interesting aspect to this case is that the botnet was very sophisticated. It used a hybrid structure that is unusual for this kind of thing. Botnets are typically peer-to-peer, in which all the infected machines communicate with each other to coordinate and carry out their nefarious activities, or they use what’s known as a C&C, or Command and Control server, that oversees the whole thing and controls the botnet form a more centralized location. That allows better control and oversight of the bots.
Kelihos, however, was a hybrid, in which there was a C&C server, but there was also a peer-to-peer aspect as there was some autonomy in the architecture that allowed the bots to continuously update among themselves a list of secondary control servers to which they would report, and those would be directly overseen by the main C&C. This is in direct contrast to the Storm botnet mentioned earlier, which was pure peer to peer. A hybrid network also allows for rapid updates to, and distribution of, associated malware.
That leads to the next neat(?) thing about the botnet: It was aggressively and frequently updated. In fact, when a live sinkholing, in which the bots are redirected to to different targets that can then help track the bots or even deactivate them, took place at a 2013 RSA security conference, a new version of the botnet rapidly took its place which indicated that the creators were prepared for just such an emergency and had pre-planned a contingency.
And this was not just a spamming botnet. Along with pushing spam of both the email and desktop pop-up kind, it also stole bitcoin and targeted banks and other large industry outlets with industry specific malware that could rake in millions of dollars while running undetected. For botnet software, this had a wide range of functionalities, both general and specific, although for all it could do it was not hard to track.
The next interesting aspect of this case is Russia fought vigorously against Levashov’s extradition. Not by attempting to block it, but rather by filing an extradition request of their own based on crimes they say he committed in Russia itself. A smart move, regardless of whether the Russian charges are true or an attempt to protect one of their own, that is a clever way of approaching it. It didn’t work, ultimately, and Levashov is now in U.S. custody, but it was an interesting tactic to counter the original extradition request. Not only that, it has happened before.
A really interesting story all the way around, and I’m curious to see how it concludes. In the meantime, be careful, ensure your OS is up to date and fully patched, be sure you are running up-to-date anti-virus and anti-malware protection, try not to visit questionable sites, don’t activate or respond to emails from unknown sources, use an ad-blocker (uBlock Origin is my preferred choice, and I have no connection to them; purely my own opinion), and just generally practice safe computing.
OpenOffice Writer: Good, better, but not yet great

People are always looking for a free alternative to costly productivity software, and never has that been more true than with Microsoft’s Office Suite. While they now have their subscription-based, $99/year Office365 Software as a Service offering, it used to be that regular updates to Office could cost hundreds of dollars, especially if you were including Access in the package. People didn’t like the repeated substantial costs associated with new versions of software, and that was not a sentiment limited to Microsoft.
The thing is, while free options, substitutes, are often available, they are also often simply not as good as the software they’re attempting to replace. Consider GIMP (GNU Image Manipulation program). Intended to be a free option for those who don’t want to purchase Photoshop, as well as for those who would like to experiment with image manipulation and the like, it’s also much more cumbersome to use. Not that Photoshop is easy, but in terms of usability GIMP isn’t an ideal. Simply drawing a straight line is a process, dragging handles is awkward, finding the right tool dock can be confusing, and if you’re just experimenting with it to get a taste of what image manipulation software is like, that taste will be bitter. Even the name itself is difficult, with GIMP being an acronym for “GNU Image Manipulation Program,” and GNU itself being the awkward acronym “GNU’s Not Linux.” It used to be the General Image Manipulation Program, and I’m not actually sure when the name change took place.
Not that isn’t effective – it is. In fact, I often use it myself for the images on this very site that require some touchup, such as adding text or combining multiple images into one or adding illustrations to name a few, and I even have an academic license for Photoshop! Quick and dirty manipulations are easier with GIMP, but as a functional, full-featured piece of software it’s functionality, not so much usability, that drives the development of GIMP. For very simple things like batch resizing / converting, pixeling out info, or cropping, I just use the IrfanView image viewer, which is much more effective and easy to use for that type of thing. But not adding text. it’s terrible for that.
So why do I mention all of this? A friend who recently lost her job needed to get her resume updated and out to potential employers fast. However, as she doesn’t make boatloads of money she had an older laptop and no Microsoft Office installed or available to her. She was trying to edit said resume in a reader, not realizing it doesn’t work like that, and without having the finances to acquire Office, she asked me for help.
My first bit of advice was to use Zoho online, a remarkably feature-packed online office suite that deserves its own, dedicated post, so I will add a followup soon with screenshots, samples and impressions. The problem is, they don’t offer a locally-installed solution and she doesn’t have Internet access, so that solution was out. I then suggested OpenOffice, a free Office alternative that has been around for a long time, and that I hadn’t tried out in years and years. I guess I should refer to it by its proper name, Apache OpenOffice, as the original OpenOffice, originally developed by a company called StarDivision, which was acquired by Sun, which was acquired by Oracle, no longer exists. Did you follow all that? It’s like a software soap opera. Anyway, OpenOffice was turned over to the Apache Foundation, which is dedicated to community-built open-sourced projects, and it has a staggering number of them. Their web server is, and has been for a long time, the most widely-used web-server on earth.
When I last used OpenOffice, long before it was taken over by the Apache Foundation, it was bad. This would have been back in the late 90s, and even then it couldn’t hold a candle to Office. The icons were unintuitive, the functionality limited, the compatibility wonky, it just wasn’t a good alternative. I’m glad to say that after twenty years it’s better than it was, it’s good, but it’s still not great and has one glaring flaw that really holds it back.
First, the good: The interface is much closer to what one would expect from a standard word processor. You can see in the image below the standard toolbar, which is also replicated in the ‘Properties’ dialog located in the sidebar. While the icons are much better, meaning much more standardized, the duplication of them across the top and side can cause issues. Functional and graphical replication is poor interface design, one you often see on webpages. And while the icons are generally much better, they’re not completely standardized. The top menu, however, uses the standard “File | Edit | View | etc.” menu with expected submenus under each entry (see ‘text boundaries’ image at end of post). You can also see in the below image(s) the icon for ‘Properties,’ one of four down the far right side, is a green and blue cube, bespoke for this program, while underneath it are the icons for ‘Styles,’ ‘Gallery,’ and ‘Navigator,’ which is ultimately used to move through the document itself via various elements. All of these are unique in function and design to OpenOffice.
It also has an extensive array of settings that covers every aspect of the program you could hope for, even how you allocate memory and VBA integration.
Using a sample resume I downloaded from the Internet, I tested how well it handled inserting elements, specifically an image and a table. This is something that can even trip up Word itself, but I am happy to say it handled both swimmingly, accurately integrating, aligning and formatting both with ease. The text adapted to any changes in size or position easily and the results were always pleasing. It also pops up a task-relevant toolbar to help further with fine tuning or further formatting the element being inserted.
Again, after insertion both of them were easy to adjust and format, and the rest of the document was very responsive to those changes. While this post doesn’t cover all you can do with Writer (you can imagine how long a post covering everything you can do in Word would be, and it’s the same here), you can get an idea from the images, specifically the ‘Navigator’ image included above.
I’m also not a big fan of the text boundaries that are shown by default; they make the whole document look as though it is too small on the page. I get that they are trying to illustrate the margins as well as provide a quick and dirty print preview, but ultimately I find them distracting. Fortunately, they can be turned off completely (which makes it look more like Word, and the familiarity is welcome).
The two big problems with OpenOffice are, unfortunately, major issues that prevent me from recommending it completely, especially as there are other programs and online options that don’t have these concerns.
The first is an issue primarily if you are importing a .docx (Word 2007 – present) file to work on a document. If you create your document from scratch in OpenOffice, it works quite well and is feature rich enough to complete even if you are doing fancy stuff. On the other hand, if you’re importing in Word’s latest format, forget it – processing hidden Word formatting codes is not Writer’s forte. Writer will destroy enough of the formating that fixing it is not worth the effort, and copy – pasting without formatting and re-formatting is likely, but not always, the only viable option. Even so, the common outcome is that no amount of tweaking will right the formatting ship: You can recenter and re-format and unbullet and rebullet and tab all over the place all you like, but it will never get back to the way it was; it will simply not play nice with undoing damage from an import.
Building on that is the most glaring issue of all: Writer simply doesn’t recognize the .docx extension. You can’t save using that extension, only .doc, a format that hasn’t been used for about ten years. Writer has its own format, .odt, that is unique enough that trying to go the other way, and opening a Writer file in Word will also yield unfortunate formatting issues. Other alternatives like the aforementioned Zoho handle them easily, but not OpenOffice. In fact, when creating a new document in Writer, it asks if you want to create a new Text document, which in Windows or Mac has a specific meaning, and it’s not a fully formatted, functional, professional document.
This post only covered OpenOffice’s word processor, Writer, although the other applications exhibit similar behaviors and limitations. They work well if you are working solely within OpenOffice, but not if importing or exporting.
I want to see OpenOffice succeed, especially under the Apache umbrella, but as of now I simply can’t recommend it as it is. That’s distressing, since I haven’t been able to ever recommend it over the last twenty years, although it’s always been very, very close. It works well on its own and with its sister programs, and has incredible potential, but the fact is it doesn’t play well with others, and until it does it simply won’t be a viable alternative.
And now it’s Opera’s turn

In a recent post, I lauded the new release of Firefox, known as Firefox Quantum, or Firefox 57.0 if you’re in to numbers. The release introduced new features and fixed many issues that have plagued it, in some cases, for years (memory leaks, I’m looking at you). One of the things I really appreciated was the ability to take a full-page screenshot that would capture the whole page, regardless of how much of it was off-screen. For someone like me who uses screenshots in class and on this blog frequently, it’s a godsend.
Having said all that, I also mentioned right at the beginning of that linked post that I’m an Opera guy even though the new Firefox has really narrowed the gap, and since Opera just released version 50.0 with some features of note, I thought it would be only prudent to mention a couple of them here. It won’t get the same coverage as Firefox because it’s not as significant of an upgrade.
Indeed, I’m only going to mention a couple of its features: full-page PDF capture and anti-Bitcoin mining technology.
As I mentioned, Firefox allows for a full-page screencap of a webpage, even if you can’t see it all in the browser window, and the cap is then saved as a .jpg image. As I mentioned, since I use screenshots extensively in my classes and on this very site, that’s invaluable. Now, Opera has the ability to do the same thing except it captures the page as a pdf. It works perfectly, I’ve had no trouble at all, and I can see how it would be useful, especially as opposed to a .jpg. If you wanted a hardcopy version of a recipe, or a series of lessons, or set of instructions then it’s ideal. If you wanted to have a permanent copy of a webpage, or send a copy of it that could be used at a meeting or for whatever reason can’t send a link then it would be very useful there as well, as it would certainly be easier to read then an image. I’m quite impressed with its functionality, and it offers a nice other option alongside Firefox’s full-page .jpg image capture. Both options are fantastic, work flawlessly, and definitely have their own specific use cases. The image below shows a multiple-page post from this site that was saved as a pdf and how it appears; it’s exactly like reading the site itself, but without links. I should also add that Firefox has an advanced ability to select page regions for capture and editing features, a feature not shared by Opera.
The other interesting feature Opera has developed is anti-Bitcoin mining technology. Bitcoins are obviously all the rage, and whether that’s because of the nature of buzzwords or legitimate hype, mining them (a topic far beyond the scope of this post but you can read about at this obvious site) requires extensive use of a PCs resources, somewhere in the neighborhood of one hundred percent, and while smart people will simply build dedicated machines for the task, other smart but misguided people instead want to use yours, and will hijack it through scripts to do so. The obvious downside is that your machine will slow to a crawl and use up insane amounts of power while it tries to mine Bitcoin for someone else. Never fear though, Opera to the rescue. According to their blog, simply turning on their built-in adblocker – another nice feature by the way along with their built-in VPN – will prevent drive-by Bitcoin-mining hijackers.
By the way, I say Bitcoin as a proprietary eponym, like Q-tip or Kleenex, however it’s any type of cryptocurrency mining that gets blocked, and Bitcoin is hardly the only one out there. I should just start saying cryptocurrency as it’s the better, general term, and I’m sure someday I will. Just know that there are many viable brands of this digital currency, but that’s a post for a later time.
So the eternal tug-of-war between Opera and Firefox continues, at least for me, and I couldn’t be happier. I’m thrilled at the way they’ve developed and hope they both keep pushing browsers forward.
Intel processors revealed to have major flaw, only addressable by OS updates

UPDATE: I’ve been trying to find out more, but Intel is now claiming it has a fix for the vulnerabilities affecting its chips that it will be rolling out by the end of next week. Details are slim, and I will hold off final judgment of course, but I’ll be surprised if it’s completely effective; these microcode patches can be tricky – it’s not a straight firmware update as it impacts the fundamental operation of the CPU. Additionally, it appears the fixes only address the last five year’s worth of processors. Better than nothing if it works.
Original post follows:
This is bad. It has been announced that Intel processors going back approximately ten years have a major flaw in how they separate the system and software. The details have not been released, but the general idea of the problem is already understood for the most part. To give a very high-level overview of what is going on and the impact of how it needs to be addressed, there is a component of every operating system known as a kernel, that separates the hardware from the software. When a program needs to open a port or save a file to disk or access a printer, or utilize hardware in any other way, it hands off that request to the kernel using what’s known as a system call, and the kernel completes the request (user mode to system mode). The catch is, the kernel is hidden from the program, even distributed in various memory locations to further hide it so that it can’t be exploited by malicious actors; it has to be loaded at system boot, however, in order for programs to use it.
Intel processors, though, use a kind of predictive processing, similar to client side prediction in games, in which a guess is made as to what will most likely happen next. In the case of Intel processors, they try to guess what code will be run next and load it up in the queue, however they apparently do this without any security procedures. The kernel is kept separate because it can contain confidential information such as passwords (which is why you can’t even get your own passwords back and there is no way to recover them if lost), however if the CPU provides no security check when loading up predictive code, it could, theoretically, run code that would ordinarily be blocked, which could then give savvy attackers access to low-level system processes and data.
But wait, there’s more bad news! Because this can’t be fixed with a firmware update or anything similar, OSs have to be written to address the problem. Linux, Windows, and OSX will all require updates that relocate the kernel in memory. Normally, it’s available to each program in their own process, but that will no longer be the case, and having to go back and forth between user mode and system mode in this manner will incur a possibly-significant performance hit on a PC after these updates, estimated by some to be as high as 30 percent.
Again, the details aren’t yet fully known, and the impact isn’t either, but if proven true it could be the worst design flaw I have ever seen. I’ll update when more is known.