Category Archives: Uncategorized
Very Important: Major PowerPoint Vulnerability
I wanted to let everyone know that Microsoft announced about a week ago that there is major security issue with PowerPoint, in which a bug in how Object Linking and Embedding (OLE) works could give malicious attackers full access to your machine.
OLE is the means by which you are able to insert data from one type of program into another program, for example embedding a spreadsheet into a PowerPoint presentation. But there are a couple of things to keep in mind regarding this flaw:
First, there is a fix, even an automated one. You can find out all about it on this page at the Microsoft support site.
Second, the attacks using this vulnerability have been very limited, no widespread havoc just yet.
Third, if you were attacked, the attacker would only get the level of control you had. So if you were a regular user, those are all the rights they would have. If you were an administrator, on the other hand, which many home PC users are, things could be different. Administrators have the ability to do things other users don’t, like install programs, make system changes, etc.
Fourth, *you* have to let it happen by opening the PowerPoint file in the first place. Here’s a bit of advice that I hope we all already know: DON’T OPEN EMAIL ATTACHMENTS FROM PEOPLE YOU DON’T KNOW! It’s very, very easy to avoid this issue altogether, and why the attacks have been limited. It requires you to open the mysterious presentation from the person you’ve never heard of. Don’t do that, and you’ll be fine.
Header image credit: techaeris.com
Ebay Lunacy

After the retro-ish post yesterday, I was inspired to see what was available on Ebay from the days of computing’s past. I was instantly reminded why I rarely buy vintage computer stuff on Ebay.
I used to, and once in the bluest of blue moons still do, but I would like to draw your attention to a few auctions that exemplify why I pulled away from it long ago.
It used to be that you could find fun vintage tech stuff on Ebay: Osborne luggables, IBM Convertibles, Northstars, all sorts of great stuff could be rummaged up.
Not any more.
I found one auction, the first one below, that so absurd in its price it spawned this whole post, but I decided to dig deeper and see what else was priced so ridiculously that my eyes would widen even further in disbelief. I arranged the auctions by price from highest to lowest, and I wasn’t disappointed. Actually, I was supremely disappointed.
Trumph of the Nerds

You may remember my mentioning in class that I was considering having movie screenings for tech-related movies that also happened to be good movies. That would include titles such as TRON (the original, not that G-d-awful remake), WarGames, Hackers, Her, Minority Report, and a couple of Simpsons and Futurama episodes for starters. If you’re wondering, I’m working with the legal standing that it all falls under the ill-defined idea of fair use since it’s being shown, ostensibly, for educational purposes.
I was going to do all that using a site called cytu.be, however I am still wrestling with it. Therefore, I thought in the meantime, and since we have a couple of weeks before we will be gathering again in class, I would present to you a documentary about the history of the personal computer and the industry that grew up around it, called Triumph of the Nerds.
It’s not the greatest name, I know. It’s even derogatory in parts, although some of the characters live up to the title. And Robert Cringely who wrote and narrates the whole thing certainly means no harm. In fact, Bob Cringely is the well known (and fake) name of long-time technology writer Mark Stephens, but the Bob Cringely name has actually been owned by many people and in fact two people are using it as pseudonyms right now!
Talk about an Apple premium!

Way, WAY back in the day I had an Apple IIe, and I loved it. So much so that I still have it, as well as a few other vintage Apples including a Power Mac, a Mac Classic, IIc, and the very rare Bell & Howell black Apple IIe. Here’s a picture of the Power Mac and the Bell & Howell in my garage, along with some additional Apple floppy drives and an old AT&T PC just visible on the right for good measure.
But I always wanted to get my hands on one of the original motherboards designed by Steve Wozniak in the Cupertino garage at the home of Steve Jobs’ parents, which, by the way, is right down the street from where I (and they) went to high school, and just up the street from where I grew up.
Virtual Machines and My Time With Windows 10 (image heavy!)

As we all know, especially if you read the Windows 10 reveal post on this very blog, Microsoft recently announced that Windows 9 was going to be Windows 10. They skipped a whole number for various theorized reasons, but response to the new OS has been cautiously optimistic. This was helped by Microsoft’s standard practice of releasing an early build that people could download, install, and play with if they were so inclined.
It’s not an alpha release, in which the software is very early, very unstable, and only tested by people inside the company, it’s more closely related to a beta, which is a later, more refined but still buggy pre-release version tested by the public or outside testers/focus groups. Rather than call it either of those however, it’s what Microsoft labels a ‘Technical Preview,’ a current, non-optimized and incomplete yet generally functional version of the still-one-year-away Windows 10. It may have bugs, it may crash, it may behave erratically or unexpectedly, it may even destroy all your data, but you agree to take on that risk if you decide to download it and give it a try.
So of course I downloaded it!
But I’m aware of the risk, and I would never install it on a machine I actually use. Well, not quite anyway. I use what’s known as a ‘Virtual Machine,’ which is a simulation of dedicated hardware on other dedicated hardware. To put it more clearly, I installed it in its own little corner of my Mac.
My first-ever blog post from a plane!

Or maybe not.
There was no way I could pass up the opportunity. Not only am I making this post while in the air over…well, somewhere, (UPDATE: I’m not!) I’m going to use it to tell you a little about how exactly in-flight WiFi works, or doesn’t, what the complexities are, and where it’s expected to go in the future.
The service, or more accurately the idea, is nifty, but there are some major, and I do mean majorly major, caveats. Frankly, and I’ll say this again, it’s so slow I just couldn’t post this from the plane. Failed uploads, 404 errors, and dropped connections, and it didn’t get any better once I arrived at the hotel. Before I get to all of it, here are some screens showing the fun things you can do with in-flight wi-fi, and learn why you should always be careful on public networks.
Welcome to the new site layout! What do you think?

As is painfully, overpoweringly obvious, I have found another reason to use my screenshot from Young Frankenstein. Also, the site has switched over to the new layout as previewed in the blog post here. The feedback was very positive even though I was only able to show a video, and there were some good suggestions as well, some of which I will try to address right here.
While the enthusiasm was almost universal, one of the most commented aspects was the background. Some loved it, some liked it, some thought it was too dark. Two suggestions were made regarding the background about which I’d like to comment (Remember, you have to click on the post title or ‘Read More’ to read more):
Create art with your mouse
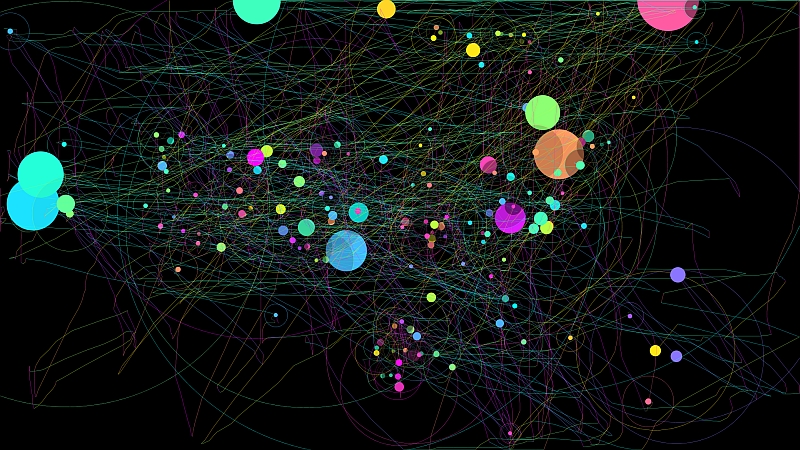
See that nifty work of art to the left there? That’s actually all the mouse movements I made over the course of just under 90 minutes while using my PC. It’s the result of a tiny program called IOGraph, and it doesn’t even require an install. You simply download it, double-click the .exe, click the button to start, and it uses very little resources (I couldn’t find it at all in Process Monitor, which is disconcerting) while it runs in the background graphing your mouse movements.
The lines represent mouse movements, and the circles indicate when and how long the mouse is at rest (the larger the circle, the longer the mouse was resting).
Bad USB!

First off, my apologies for the late post. I spent all day recording the lecture for the week I’ll be gone, and it turned out to be much more involved than I had anticipated. I think it ultimately came out all right, but it took about six and a half hours.
So we’ll see how it goes, in the meantime here’s a late post.
There was, earlier this year, the revelation that every single one of the billions of USB devices out there has a fatal flaw in its firmware, in which a malicious user or hacker could reprogram it to fool the machine into which it is plugged that it is some other type of device. In other words, it may be a thumb drive, but its firmware could be reprogrammed to fool a PC into thinking it’s a keyboard, which would then allow it to send keypresses to the host machine and a malicious user to then get the host to carry out malicious tasks. The flaw is known as BadUSB.
New technology brings new, serious security concerns
Technology, and its advancement, is a great thing. With every passing moment, some new development is announced that will make our lives, and ourselves, better, or faster, or more efficient, or healthier, or more accessible, or a host of other things that make everything we do better.
The problem is, there are always people out there who want to exploit that technology for their own gain, their own end, or their own purpose. And now, although it’s been a concern for quite some time, it has now been predicted that the first ‘Online Murder’ will happen by the end of the year.

