Tag Archives: TOR
New, dangerous ransomware appears in the wild

In class we talked briefly about ‘Ransomware,’ software that compresses / encrypts / locks up your files, then demands payment for the password or key or whatever to get your files back. We also discussed that the amounts of money demanded are never too much to prevent someone from actually paying – if they asked for a million dollars no one would pay it, and the encryption was normally breakable if you knew what you were doing.
Now, in an event that involves many of the topics we discussed in our last class, a scary new ransomware attack is changing all that. Known as OphionLocker (this article shows it may not be as sophisticated as everyone is saying, possibly breakable through a C++ IDE ), it uses what is known as elliptic curve cryptography, a practically unbreakable form of encoding, to hold files hostage, and it is delivered through malicious ads displayed on web pages.
More Facebook, but actually Internet privacy
Boy, this week is all Facebook all the time. Weird, considering I don’t use it.
So a couple of days ago I made a post about why I’m not on Facebook, at least at this particular time in my life, but I know many others are and that’s ok. For those of you who are, have you ever worried that someone might be spying on you while you connect? It seems like a strange thing to wonder about considering the whole purpose is to be visible, but in other parts of the world, sharing photos or other information on sites like that can result in serious consequences.
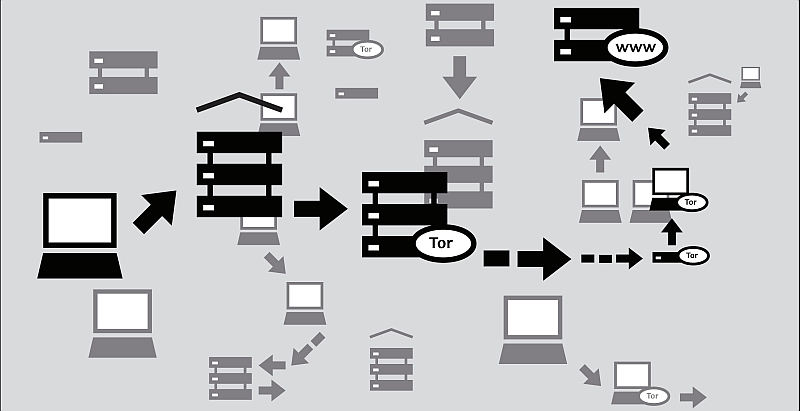
So in a somewhat surprising move, Facebook has created a version of their site that can only be accessed using TOR software. Let me give you some background:
TOR is (was) an acronym for “The Onion Router” (which is why the technically correct way of writing it is TOR, not Tor, although Tor is now the catchall term for it). What it does is bounce your connection to a site through a trusted series of secure points before you head out on to the Internet proper through an exit node, where you exit form the Tor network tot he Internet itself, all of which makes it very difficult to trace your origins or determine the true destination of what you’re doing on line. So if someone wants to monitor your network connections to try and determine where you’re going or what the origin of a particular transmission is, TOR would make that very difficult.
Even TOR users aren’t safe now

Not that they should be. You see, there is a dark underbelly of the Web appropriately known as the Darknet. This is the place where people often carry out very illegal activities such as sell and buy drugs, find child pornography, suborn terrorism, traffic in weapons or even endangered species.
How does it happen? Through a project known as TOR, or The Onion Router, so named because it surrounds your browsing experience with many layers, like an onion. Essentially, when you use a TOR-compatible client you are routed through an even more labyrinthine series of points than you are when doing regular browsing. This makes it very, very difficult for anyone to track who you really are or what you are really doing.
Because TOR is so well-known for the bad things that happen, it has also been the target of white-hats who want to shut down those activities. It’s happened again and again and again., it’s a never ending battle.
 Now, a new attack has happened, however in this case it’s to strip away those protective layers and expose those who are using the network. The attackers are believed to be two researchers from Carnegie-Mellon University who claimed to have found vulnerabilities in the network, and are to give a talk at the Black-Hat Conference that will be taking place right here in Las Vegas this weekend! Those same researchers also discovered flaws in a similar anonymizing service known as the Invisible Internet Project.
Now, a new attack has happened, however in this case it’s to strip away those protective layers and expose those who are using the network. The attackers are believed to be two researchers from Carnegie-Mellon University who claimed to have found vulnerabilities in the network, and are to give a talk at the Black-Hat Conference that will be taking place right here in Las Vegas this weekend! Those same researchers also discovered flaws in a similar anonymizing service known as the Invisible Internet Project.
A lot of bad things happen on the Darknet, but it is also important to keep in mind it is also an invaluable tool for those who might have their privileges of communication stifled in any way, such as those living in oppressive (or not-so-oppressive) and restrictive regimes where access to the Internet is strictly controlled or prohibited to hinder dissent. In that sense it’s a valuable tool, but anything used for good can also be used for bad.
(Header image from cyberwarzone.com)
