Tag Archives: Russia
Russian botnet master nabbed in Spain, extradited to US
This is a story that has been ongoing for some time. Pyotr Levashov, a well-known and well-established Russian cybercriminal who was arrested in April of last year (2017 if you’re reading this in the distant future – welcome alien overlords!) while vacationing in Spain, has finally been extradited to the U.S. Apparently cybercriminaling does pay well sometimes. The arrest was based on a formal U.S. Department of Justice indictment against him for, among other things, operating the Kelihos Botnet, a long-running, expansive, global botnet that bombarded the world with all kinds of spam for nonsense like get-rich-quick schemes and enhancement medications; if you’re interested, and you should be, you can read the DOJ press release about the indictment and the actual search warrant that allowed for their infiltration of the botnet.
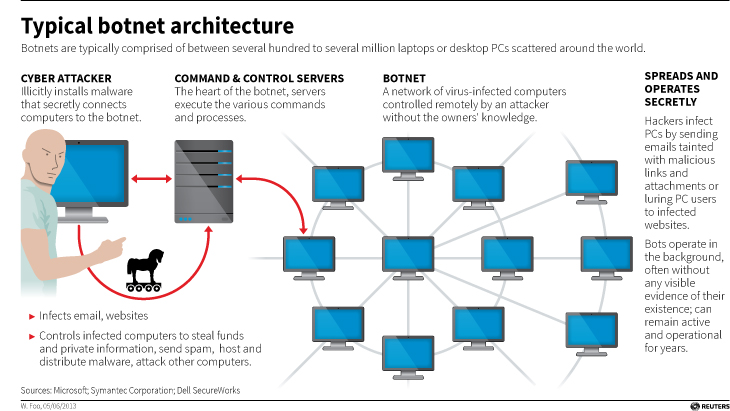
Before we continue, let’s talk about what a botnet is. When malware, or bad software (get it? Mal ware?), is surreptitiously installed on your machine, either through a drive-by attack in which it’s embedded in a Flash ad, or you click on a link or file from a rogue email, or one of many other attack vectors, it will use your machine to carry out tasks without your permission, involvement, or even knowledge. And just to be sure, those tasks it’s carrying out are bad. It can use your machine to send spam, participate in DDoS attacks, store harmful or illegal files, and many other unethical / criminal activities, all without you ever being privy to what’s going on. When that happens, your machine is what’s known as a zombie computer, or more commonly, a bot. Now, imagine hundreds of thousands of these infected machines all acting in unison, for a common goal or under a central control authority. That’s a botnet. Here’s an effective graphic from Reuters that illustrates the architecture of a botnet.
I wanted to embed an interactive map from Arbor Networks that shows real time attacks happening right now, and provides historical data, but their embed code which uses iframes doesn’t work on WordPress. I find it strange a security firm would still be supplying iframe embed codes, but who am I to judge? No matter; there are other sites that provide similar information using their own honeypot networks, such as Kaspersky’s real-time threat map and the well-known Norsecorp map. Actually, I had intended to use Norsecorp’s IPViking map, however it is now run under HP’s banner, although powered by Norse, and I simply couldn’t get it to work in any browser. Their map linked above works beautifully, though.
There are several interesting facets to this case: The first is, this guy has been around a long time and was one of the bad actors behind the Storm botnet that first manifested all the way back in 2007. That botnet was eventually dismantled by the combined efforts of Microsoft, malware firms, and the feds, a partnership and collaboration that continues to this day. We’ll come back to this particular botnet soon, because the architecture of these things is going to become important.
By soon, I mean right now! Another interesting aspect to this case is that the botnet was very sophisticated. It used a hybrid structure that is unusual for this kind of thing. Botnets are typically peer-to-peer, in which all the infected machines communicate with each other to coordinate and carry out their nefarious activities, or they use what’s known as a C&C, or Command and Control server, that oversees the whole thing and controls the botnet form a more centralized location. That allows better control and oversight of the bots.
Kelihos, however, was a hybrid, in which there was a C&C server, but there was also a peer-to-peer aspect as there was some autonomy in the architecture that allowed the bots to continuously update among themselves a list of secondary control servers to which they would report, and those would be directly overseen by the main C&C. This is in direct contrast to the Storm botnet mentioned earlier, which was pure peer to peer. A hybrid network also allows for rapid updates to, and distribution of, associated malware.
That leads to the next neat(?) thing about the botnet: It was aggressively and frequently updated. In fact, when a live sinkholing, in which the bots are redirected to to different targets that can then help track the bots or even deactivate them, took place at a 2013 RSA security conference, a new version of the botnet rapidly took its place which indicated that the creators were prepared for just such an emergency and had pre-planned a contingency.
And this was not just a spamming botnet. Along with pushing spam of both the email and desktop pop-up kind, it also stole bitcoin and targeted banks and other large industry outlets with industry specific malware that could rake in millions of dollars while running undetected. For botnet software, this had a wide range of functionalities, both general and specific, although for all it could do it was not hard to track.
The next interesting aspect of this case is Russia fought vigorously against Levashov’s extradition. Not by attempting to block it, but rather by filing an extradition request of their own based on crimes they say he committed in Russia itself. A smart move, regardless of whether the Russian charges are true or an attempt to protect one of their own, that is a clever way of approaching it. It didn’t work, ultimately, and Levashov is now in U.S. custody, but it was an interesting tactic to counter the original extradition request. Not only that, it has happened before.
A really interesting story all the way around, and I’m curious to see how it concludes. In the meantime, be careful, ensure your OS is up to date and fully patched, be sure you are running up-to-date anti-virus and anti-malware protection, try not to visit questionable sites, don’t activate or respond to emails from unknown sources, use an ad-blocker (uBlock Origin is my preferred choice, and I have no connection to them; purely my own opinion), and just generally practice safe computing.
NATO: Not just for ground wars anymore

As you should all be acutely aware, there is a huge kerfuffle in the east of Ukraine, where Russian troops are attempting to establish a Russian province they refer to as “Novorossiya,” or “New Russia.”
This is a problem because the former Russian-backed president of Ukraine, Viktor Yanukovich, was ousted earlier this year in a revolt by Ukrainians who wanted closer ties with the European Union, the west, and even NATO, but Russia would have none of it since Ukraine shares a border with Russia, and that is too much of a strategic concern for them to give up. Not only that, one of the reasons for the existence of NATO was to defend against a Russian invasion into a member country; to have a NATO member share a border with Russia is unacceptable to the Russian leadership.
(It should be noted that Russia does have some memberships in NATO programs).
Once the president had been ousted in the uprising, pro-Russian rebels took up arms almost immediately and started taking back parts of eastern Ukraine, and personnel and resources allegedly supplied by Russia have been supporting them in their fight. This puts western powers, who back the desire for Ukraine to join them, in direct conflict with Russia who is unwilling to let go of at least eastern Ukraine, and now the reason NATO was created is flaring up once again. Although quite unlikely, it could cause a direct military confrontation between Russia and western powers.
Keeping all that in mind, one of the general purposes of the NATO alliance was to provide security in numbers; if one member of the alliance was attacked, it was considered as if all members were attacked, and there would be a unified response. While they have rarely mobilized troops, they have created a new type of partnership in light of current world events: A cybersecurity force.
It is widely believed that the hacks into J.P. Morgan Chase and Home Depot were the result of Russians attempting to retaliate against the crippling sanctions that have been imposed based on their response in Ukraine, although Russian hacking of US systems is nothing new – everyone hacks everyone.
Because of that, NATO has now decided that their alliance includes cyberspace as well, and member nations have signed an agreement that provides for support, expertise, and response from all members of NATO when any one member is cyberattacked.
Although you wouldn’t know it these days, it is widely stated that future wars will be fought on-line, and even with lasers and robots (don’t laugh, it’s happening) and this agreement appears to be some confirmation of that.
Did Russian hackers almost bring down the nasdaq?

It has just been revealed that in 2010, Russian hackers, likely associated with the Russian government, and using using custom-designed malware to exploit zero-day vulnerabilities (something that should absolutely not be present in systems of this sort) were able to infiltrate the NASDAQs systems for the purposes of snooping around. However, it appears it also had the capabilities of delivering what is known as a ‘Logic Bomb;’ a destructive program that waits until a specific date occurs before it does its damage.
A destructive program destroying the internals of the NASDAQ’s servers would have wreaked havoc across the U.S. financial infrastructure, and the world’s as well. And it turns out that once the malware was discovered it appeared it could have wiped out the NASDAQ’s internals completely. So serious was it, that although no less than five separate federal security agencies had discovered the infiltration, they felt it had to be brought to the attention of the President.
 The investigation discovered that not only did these Russian hackers have access to the NASDAQ’s servers, but Chinese hackers did as well along with other unidentified intruders, and that the servers were very vulnerable to attack with one person referring to it as a swamp. Although the potential impacts were catastrophic, the NASDAQ never reported the attacks nor indicated their severity. Expanding on the investigation, it turns out most banks and large financial institutions were possessed of the same vulnerabilities.
The investigation discovered that not only did these Russian hackers have access to the NASDAQ’s servers, but Chinese hackers did as well along with other unidentified intruders, and that the servers were very vulnerable to attack with one person referring to it as a swamp. Although the potential impacts were catastrophic, the NASDAQ never reported the attacks nor indicated their severity. Expanding on the investigation, it turns out most banks and large financial institutions were possessed of the same vulnerabilities.
The scary part is that no conclusion was ever reached. Even the ultimate purpose of the intrusion is unclear; some say it was to do damage, some say it was just so the Russians could build an equivalent system. It also shows that we are not as far ahead as we often think in terms of security or technology; we still can’t definitively say it was actually the Russians. Great advances have been made since this event happened, but it’s a global race and it seems we’re still in no position to prevent it.