Tag Archives: Law
Russian botnet master nabbed in Spain, extradited to US
This is a story that has been ongoing for some time. Pyotr Levashov, a well-known and well-established Russian cybercriminal who was arrested in April of last year (2017 if you’re reading this in the distant future – welcome alien overlords!) while vacationing in Spain, has finally been extradited to the U.S. Apparently cybercriminaling does pay well sometimes. The arrest was based on a formal U.S. Department of Justice indictment against him for, among other things, operating the Kelihos Botnet, a long-running, expansive, global botnet that bombarded the world with all kinds of spam for nonsense like get-rich-quick schemes and enhancement medications; if you’re interested, and you should be, you can read the DOJ press release about the indictment and the actual search warrant that allowed for their infiltration of the botnet.
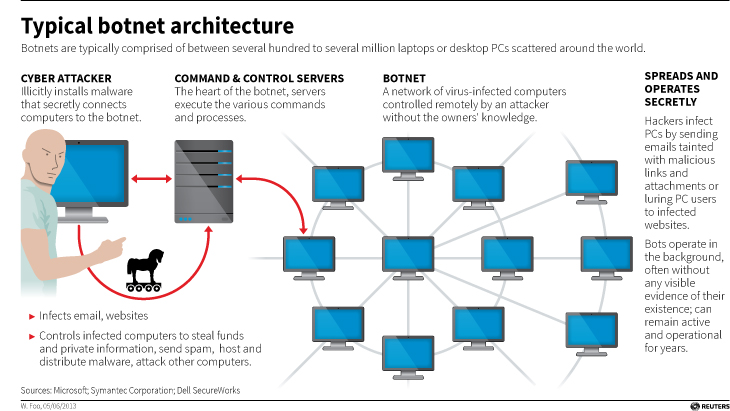
Before we continue, let’s talk about what a botnet is. When malware, or bad software (get it? Mal ware?), is surreptitiously installed on your machine, either through a drive-by attack in which it’s embedded in a Flash ad, or you click on a link or file from a rogue email, or one of many other attack vectors, it will use your machine to carry out tasks without your permission, involvement, or even knowledge. And just to be sure, those tasks it’s carrying out are bad. It can use your machine to send spam, participate in DDoS attacks, store harmful or illegal files, and many other unethical / criminal activities, all without you ever being privy to what’s going on. When that happens, your machine is what’s known as a zombie computer, or more commonly, a bot. Now, imagine hundreds of thousands of these infected machines all acting in unison, for a common goal or under a central control authority. That’s a botnet. Here’s an effective graphic from Reuters that illustrates the architecture of a botnet.
I wanted to embed an interactive map from Arbor Networks that shows real time attacks happening right now, and provides historical data, but their embed code which uses iframes doesn’t work on WordPress. I find it strange a security firm would still be supplying iframe embed codes, but who am I to judge? No matter; there are other sites that provide similar information using their own honeypot networks, such as Kaspersky’s real-time threat map and the well-known Norsecorp map. Actually, I had intended to use Norsecorp’s IPViking map, however it is now run under HP’s banner, although powered by Norse, and I simply couldn’t get it to work in any browser. Their map linked above works beautifully, though.
There are several interesting facets to this case: The first is, this guy has been around a long time and was one of the bad actors behind the Storm botnet that first manifested all the way back in 2007. That botnet was eventually dismantled by the combined efforts of Microsoft, malware firms, and the feds, a partnership and collaboration that continues to this day. We’ll come back to this particular botnet soon, because the architecture of these things is going to become important.
By soon, I mean right now! Another interesting aspect to this case is that the botnet was very sophisticated. It used a hybrid structure that is unusual for this kind of thing. Botnets are typically peer-to-peer, in which all the infected machines communicate with each other to coordinate and carry out their nefarious activities, or they use what’s known as a C&C, or Command and Control server, that oversees the whole thing and controls the botnet form a more centralized location. That allows better control and oversight of the bots.
Kelihos, however, was a hybrid, in which there was a C&C server, but there was also a peer-to-peer aspect as there was some autonomy in the architecture that allowed the bots to continuously update among themselves a list of secondary control servers to which they would report, and those would be directly overseen by the main C&C. This is in direct contrast to the Storm botnet mentioned earlier, which was pure peer to peer. A hybrid network also allows for rapid updates to, and distribution of, associated malware.
That leads to the next neat(?) thing about the botnet: It was aggressively and frequently updated. In fact, when a live sinkholing, in which the bots are redirected to to different targets that can then help track the bots or even deactivate them, took place at a 2013 RSA security conference, a new version of the botnet rapidly took its place which indicated that the creators were prepared for just such an emergency and had pre-planned a contingency.
And this was not just a spamming botnet. Along with pushing spam of both the email and desktop pop-up kind, it also stole bitcoin and targeted banks and other large industry outlets with industry specific malware that could rake in millions of dollars while running undetected. For botnet software, this had a wide range of functionalities, both general and specific, although for all it could do it was not hard to track.
The next interesting aspect of this case is Russia fought vigorously against Levashov’s extradition. Not by attempting to block it, but rather by filing an extradition request of their own based on crimes they say he committed in Russia itself. A smart move, regardless of whether the Russian charges are true or an attempt to protect one of their own, that is a clever way of approaching it. It didn’t work, ultimately, and Levashov is now in U.S. custody, but it was an interesting tactic to counter the original extradition request. Not only that, it has happened before.
A really interesting story all the way around, and I’m curious to see how it concludes. In the meantime, be careful, ensure your OS is up to date and fully patched, be sure you are running up-to-date anti-virus and anti-malware protection, try not to visit questionable sites, don’t activate or respond to emails from unknown sources, use an ad-blocker (uBlock Origin is my preferred choice, and I have no connection to them; purely my own opinion), and just generally practice safe computing.
California’s kill-switch law goes in to effect today

Sometimes I just can’t figure out why an obviously great – and necessary – idea doesn’t immediately become a law, even if it adds a miniscule extra step on the manufacturing end.
In this case, I’m referring to a “kill-switch,” a feature that would allow the owner of a smartphone to remotely render the device unusable in the case of loss or theft. Today in California, a law goes into effect statewide that mandates all smartphones have kill-switch functionality implemented and on by default (something I suspect will not be the case universally). Minnesota is the only other state with a mandatory kill-switch law, however their version does not require the feature to be enabled by default.
Mystery solved, and a little about tech patents

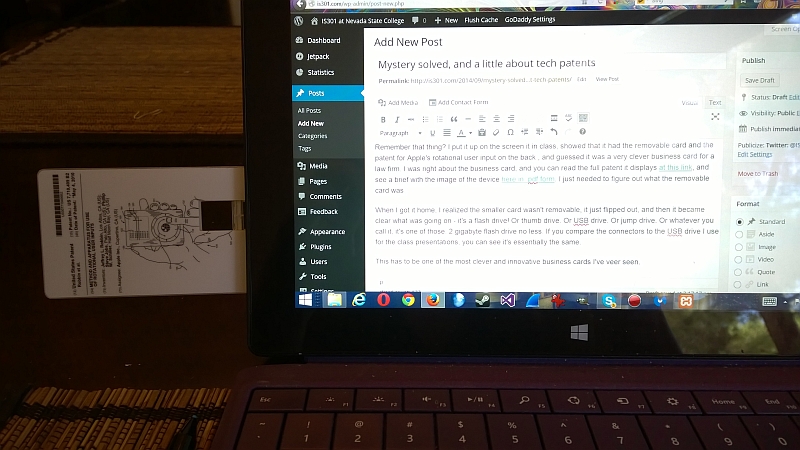
Remember that thing? Jet brought it in, I put it up on the screen in class, showed that it had the removable card and the patent for Apple’s rotational user input on the back , and guessed it was a very clever business card for a law firm that deals with patents and intellectual property. I was right about the business card, and you can read the full patent it displays at this link, and see a brief with the image of the device here in .pdf form. I just needed to figure out what the removable card was.
When I got it home, I realized the smaller card wasn’t removable, it just flipped out, and then it became clear what was going on – it’s a flash drive! Or thumb drive. Or USB drive. Or jump drive. Or whatever you call it, it’s one of those. 2 gigabyte flash drive no less, and even comes with a .pdf primer on patents – try saying that three times fast. If you compare the connectors to the USB drive I use for the class presentations, you can see it’s essentially the same. To be specific, it’s what’s known as a ‘Type A‘ connector even though it’s not enclosed as is typical. The two center pins are the channels through which data is transferred, and as is very common with data channels of all types, one is positive and one is negative.
This has to be one of the most clever and innovative business cards I’ve ever seen, it’s very inventive and frankly I plan on using it as an example in future classes. Plus, I can use it, and if it’s ever lost or stolen someone would be afraid to use it because it’s from a law firm! Well, maybe that wouldn’t deter them, but it’s an added layer of security. It’s so light it can be used without support, as you can see in this (very dark) image that shows it plugged into the side USB port of my Surface.
But because this is the business card of a patent law firm, it also lets me offer an introduction to the idea of intellectual property, trademarks, and patents in the tech industry. I don’t want to go too deep into it now because we have a whole class covering the topic and we will talk a lot about it towards the end of the semester, although in a way the conversation has already begun. In essence, when we talk about intellectual property (IP) or patents, what we mean is something you create or develop or invent and the establishment of your ownership of that creation, or design, or process, or thing, or whatever it is. This often takes the form of licensing fees, which is standard practice; For every Blu-Ray disc or player manufactured, Sony gets a fee. For every Android handset sold, Microsoft gets a fee. For (almost) every HTC phone sold, Apple gets a fee. And the list goes on and on.
There has been a big debate over what is and isn’t patentable, what should and shouldn’t be patentable, and what to do if you feel someone is using your idea without recognition or compensation. If you don’t think it could possibly be that big of an issue, remember that for some companies, their most lucrative – or only – product is its patents and patent portfolio.
So important are patents and the revenue they can generate, especially in the tech industry, that lawsuits happen ALL THE TIME. I’m normally against using bulleted lists for anything when writing, but I think here it’s warranted. Behold, just a few of the recent, and one not-so-recent, tech-industry patent/trademark/IP fights that have happened:
- Apple sues Samsung
- Samsung sues Apple
- Microsoft sues Samsung
- The Beatles sue Apple
- Oracle sues Google
- Apple and Microsoft sue Google
- Google sues Apple (Like all good wars, this actually ended in a truce)
- Google sues Microsoft
- Microsoft and Google sue the government (not a patent issue, just thought I’d throw it in there)
- NVidia sues Samsung *and* Qualcomm
- Bose even sued Beats
These are all recent, and only a few, but this has been going on for years. Many years. This link has 1188 pages of tech-industry patent and trademark lawsuits, and it only goes back to 2003! In fact, according to legal analytics firm Lex Machina, the top 10 targets of patent lawsuits in 2013 were tech firms, with Apple at the top of the list.
Even so, if you have developed something that makes a significant contribution to society, science or industry, you need to fight to keep that patent under your wing and in your portfolio, especially if it’s widely used. I like to think that most companies aide by patent laws (in fact, I was just today reading an article on Tom’s Hardware about building a budget PC, and the liquid-cooling unit they recommend hasn’t been released yet in the U.S. because of unspecified patent issues and a required redesign based on them).
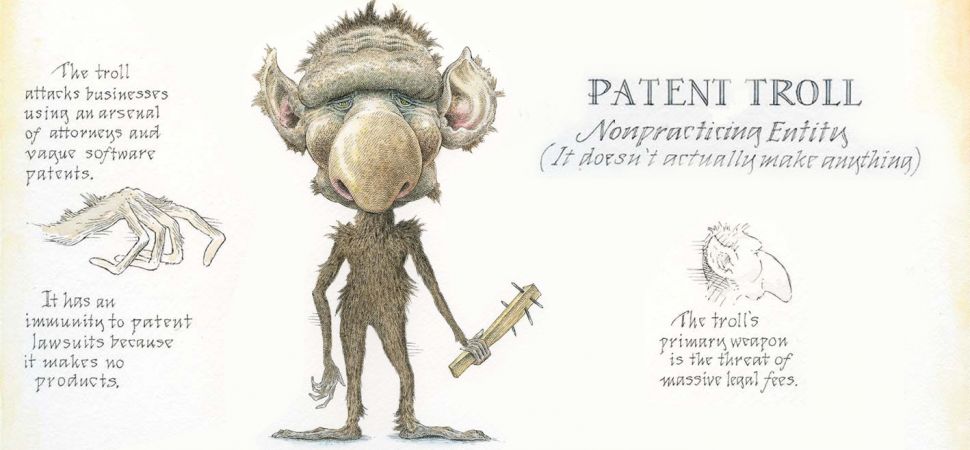
However if you don’t watch your patents carefully, less scrupulous actors could hijack them and claim them as their own, or not pay the licensing fees, or make a knockoff and claim it as original. This also leads to a discussion of something very nefarious in the discussion of patents, something known as patent trolls; companies that create no products, but rather endlessly sue everyone, using questionable legal tactics, over patents they supposedly own. Luckily, they usually get slapped down pretty hard. Prenda Law is the most well-known and loudmouthed patent troll, although because of repeated and brutal defeats in court they’re somewhat quiet as of late. There are others, but it appears what happened to Prenda has made them afraid, with good reason. There are even sort-of patent trolls. The fact is, justified or not, it can be lucrative.
There have been loud calls for reform of patent laws. For example, some say it shouldn’t be possible to patent, say, rounded corners, or taking a photograph of something in front of a white background, or patent something that has been standard practice for centuries but now you’re “doing it on a computer,” which the Supreme Court has said is not enough. It’s very complex and convoluted, and from what I can tell it doesn’t appear there will be a change anytime soon.
I don’t mean to imply that all patent lawsuits are frivolous, not at all; patent ownership is important for the people who own patents. But as patent trolls illustrate, many of them are frivolous, and it’s unfortunate, because lawsuits like this can really stifle creativity and innovation in that case. It’s just that there are so many, it’s hard to separate what’s legitimate form what’s trolling.
You’ll notice we have a whole class on ‘Ethics, Crime, and Security.’ It is there that we will talk extensively about copyright, intellectual property, trademarks, domain squatting, and the general reality that the Internet has always been a haven for theft of not just goods such as songs or videos, but of ideas and attributions. In any industry it is absolutely vital to watch over your patents and ensure that others who use them, which in the tech industry could be a very large number of players, is doing so within their, and your, rights.