Tag Archives: HP
Almost all HP laptops have a dormant keylogger

If you have an HP laptop like me, you’ll want to read this. For the second time this year, it turns out that (almost) all HP laptops have a deactivated keylogger hidden in their innards. Before, it was a component of the Conexant audio driver and was actually logging keystrokes, while this time it is part of a debugging component for the Synaptics TouchPad software, something most laptops – not just HP – have, so you might want to take a look or inquire with your manufacturer anyway. HP even states on their patch site, linked below, that the driver affects all Synaptics OEM partners, which means there will be a lot more than just HP laptops affected.
While the keylogger is not activated by default, it could be if someone has administrator privileges and knows which specific registry key to edit, a task that is itself no small matter, as anyone who has done registry edits will know. Interestingly, in an odd take on the situation, some in the security field have noted that if someone has administrator access to a machine, they won’t need to modify a registry key to activate a dormant debugger-based keylogger as they could simply install an actual keylogger. The counterpoint is that the driver-based keylogger, because it’s actually part of an integrated debugging / tracing function, would be harder to detect and leave less of a trace than a full-blown logger, so it would be a less intrusive and more opportune choice for those looking to listen in; there’s a built-in excuse for why it might be doing what it’s doing.
That’s assuming it’s detected, of course. The fact is, detecting them is notoriously difficult. Things have gotten better, but even the best antivirus program has trouble identifying them, and that’s even more true of one that’s operating at the system level – you might want to try a scanner that looks for keyloggers specifically. Since nothing is easy, those types of programs are few and far between because of the difficulty in detecting the logger in the first place. The one most often recommended is KL-Detector, but I’m not convinced of its effectiveness and definitely uncertain of the last time it was updated, which is critical in security software. While it will run on Windows 10, the only systems it explicitly confirms are Windows 2000 and XP, not something that gives me confidence as to its currency. Plus, it’s not a removal tool, only a detector. I don’t know why it’s so often recommended.
Physical keyloggers are easy – check where your keyboard plugs into its port. No additional device, no keylogger. Honestly, these are practically obsolete and were mainly used when keyboards still plugged into PS/2 ports, but don’t be fooled – USB physical keyloggers are out there, but are not commonly used because the chance of discovery is high.
It must also be noted that while there are obvious nefarious uses for keyloggers and that is why we generally hear about them, they have valid uses as well. If you are a parent who’s concerned about what your kids are doing online, a keylogger might be one option, especially these days. If you’re conducting a legitimate investigation, a keylogger is an option and has been used in the courtroom, both successfully and unsuccessfully. And, as alluded to above, they have valid testing and debugging uses. It’s similar to peer-to-peer sharing software; we mainly hear about how it’s bad, but it can also be very useful.
In a way it’s better than the previous time this happened because the keylogger is not active, but it’s worse because so many more models are impacted. HP acted right away and issued a patch, although if you received a Windows Update in the last couple of days you should be fine as well. If you’d like to be doubly sure, you can check HP’s patch site to download a patch for your model. There are a lot of links, so you’ll need to know your exact model.
“The Machine,” and a new OS
Back in the beginning days of this semester, we talked about a storage technology developed by Hewlett-Packard known as the Memristor, which is capable of storing massive amounts of data in small spaces, and in state. In other words, it doesn’t rely on the binary construct of 1 or 0, but rather the ability to store data as any value between 1 and 0.
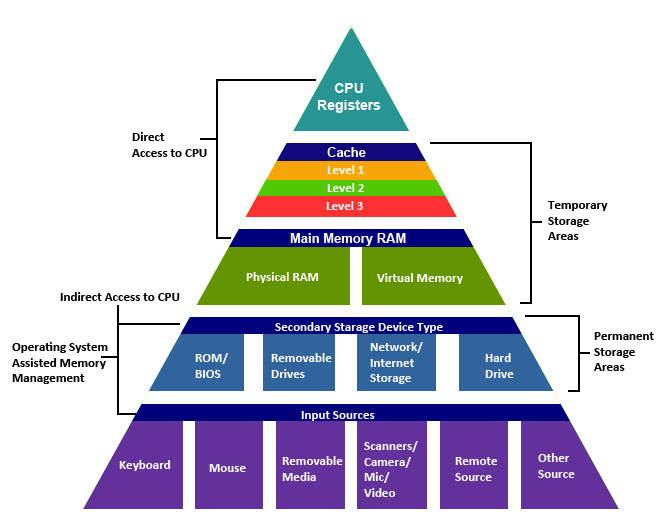
Recently, HP announced an ambitious new project they have dubbed The Machine, which is meant to improve system architecture by using its Moonshot servers as well as fiber to connect the CPU directly to storage without the physical proximity constraints copper requires, vastly increase memory performance by using memristors (which is still considered a misspelled word by editors) to flatten the memory hierarchy we learned about, and top it all off with an operating system based on Linux that HP has cleverly dubbed Linux++. On a side note, ‘++’ in programing is how you increment a value, and it comes up in naming conventions a lot; for example, the notepad I use over the built-in Windows notepad has the name of Notepad++, and coincidentally if you do any programming, it’s a necessity.