Tag Archives: Darknet
Microsoft releases free, cloud-based anti-child pornography tool

One of the most insidious, vile crimes that could be committed is one against a child. Unfortunately, the Internet serves as a breeding ground for those who would do harm to them, and what’s described in the title is about as sick as it be.
With the millions of pictures uploaded to sites like Facebook, Instagram, Pinterest, and all the others, how can those services and others ensure that nothing of the sort is posted to their servers? How do they maintain their reputation and their quality while still allowing freedom and flexibility in what people upload without violating laws or human decency?
Even TOR users aren’t safe now

Not that they should be. You see, there is a dark underbelly of the Web appropriately known as the Darknet. This is the place where people often carry out very illegal activities such as sell and buy drugs, find child pornography, suborn terrorism, traffic in weapons or even endangered species.
How does it happen? Through a project known as TOR, or The Onion Router, so named because it surrounds your browsing experience with many layers, like an onion. Essentially, when you use a TOR-compatible client you are routed through an even more labyrinthine series of points than you are when doing regular browsing. This makes it very, very difficult for anyone to track who you really are or what you are really doing.
Because TOR is so well-known for the bad things that happen, it has also been the target of white-hats who want to shut down those activities. It’s happened again and again and again., it’s a never ending battle.
 Now, a new attack has happened, however in this case it’s to strip away those protective layers and expose those who are using the network. The attackers are believed to be two researchers from Carnegie-Mellon University who claimed to have found vulnerabilities in the network, and are to give a talk at the Black-Hat Conference that will be taking place right here in Las Vegas this weekend! Those same researchers also discovered flaws in a similar anonymizing service known as the Invisible Internet Project.
Now, a new attack has happened, however in this case it’s to strip away those protective layers and expose those who are using the network. The attackers are believed to be two researchers from Carnegie-Mellon University who claimed to have found vulnerabilities in the network, and are to give a talk at the Black-Hat Conference that will be taking place right here in Las Vegas this weekend! Those same researchers also discovered flaws in a similar anonymizing service known as the Invisible Internet Project.
A lot of bad things happen on the Darknet, but it is also important to keep in mind it is also an invaluable tool for those who might have their privileges of communication stifled in any way, such as those living in oppressive (or not-so-oppressive) and restrictive regimes where access to the Internet is strictly controlled or prohibited to hinder dissent. In that sense it’s a valuable tool, but anything used for good can also be used for bad.
(Header image from cyberwarzone.com)
Unbelievable real-time map of global hack attacks
Norse Technologies, one of the leading network-security and monitoring companies, has released an absolutely mesmerizing global map that shows, in real time, global hack attempts, including the type of hack, the origin of the hack, and the intended target. That’s a picture of it in the header, and while writing this post I also was fortunate enough to witness a massive, coordinated attack that you can see in the image below. Fun!
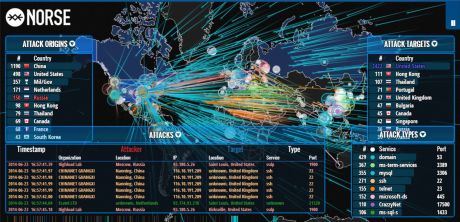 You can hover over any on-screen element top get more information about that particular attempt. Norse achieves all this by using its own honeypot infrastructure. A honeypot is a type of server that sits between the Internet and a company network, and is intended to look like a regular server on said network. However, it is actually specifically designed to attract hack attempts and fool the attacker into thinking they have successfully gained access to a system or network, all the while while monitoring the attempt and gathering as much information as it can in order to learn about network vulnerabilities or to gather information for a potential prosecution. Honeypot servers can be deployed in several ways, however it is not uncommon for them to have a small amount of actual corporate data on them to maintain the ruse for as long as is required.
You can hover over any on-screen element top get more information about that particular attempt. Norse achieves all this by using its own honeypot infrastructure. A honeypot is a type of server that sits between the Internet and a company network, and is intended to look like a regular server on said network. However, it is actually specifically designed to attract hack attempts and fool the attacker into thinking they have successfully gained access to a system or network, all the while while monitoring the attempt and gathering as much information as it can in order to learn about network vulnerabilities or to gather information for a potential prosecution. Honeypot servers can be deployed in several ways, however it is not uncommon for them to have a small amount of actual corporate data on them to maintain the ruse for as long as is required.
They also mention they are following darknet attacks, but I don’t know why that would be necessary. Darknets are networks that run underneath the Internet, using virtual private networks and tunneling protocols and things of that nature to avoid detection and access (Silk Road, in the news a lot recently, was a darknet used to traffic weapons, drugs, in some cases even people), but there are enough regular attacks that darknet monitoring wouldn’t be necessary. I suspect their use of the term is representative of their own network of honeypot servers.
NOTE: I could only get the site to run smoothly in the Chrome browser, and it’s worth downloading just for this. It worked in Internet Explorer and Firefox after a refresh, but very slowly, so be aware.