Category Archives: Uncategorized
How to protect yourself from viruses

Well, not you, you know, but rather your digital devices. It came up in class and I was asked again by a few of you as to what programs are available to guard against malware that might infect your machine, so I thought would offer some suggestions.
First, I advise against paid services for your home machines, especially Norton/MacAfee/Symantec. There are many free alternatives that work very well, while those big ones and their ilk are dilettantes, wanting to protect your machine and monitor ports and watch incoming/outgoing traffic and monitor webapges and it ends up using a ton of computing resources and they’re difficult to uninstall, leaving traces of themselves all over your hard drive and registry. The free options have paid versions, but as an individual user you don’t need them, and their virus definitions, which allow them to recognize viruses, are updated just as often.
Also, please be aware that any digital device can be infected with malware, and for those who think Macs are immune I have some bad news for you as well.
Having gotten that out of the way, I have provided some alternatives below. Keep in mind that each of these offers strong virus protection, but their features beyond that are usually pretty comparable, such as HTTP scanning to protect you against visiting malicious webpages, and real-time system monitoring. You also want to be sure the virus definitions are always up-to-date, and in fact right after installation of any of these that’s the first thing that will happen, then set them to update automatically. Ultimately, the one that is best for you depends on what you need and what you want.
One final thing, absolutely do not run more than one simultaneously! Not only will it unnecessarily tax your system resources, they’ll try to scan each other interfering with their ability to perform their tasks and possibly providing false positives.
And now, your choices!
AVG has been around for a long time, and they recently updated their interface to bring it more in line with modern design trends. Their malware detection and removal is effective, it actively monitors your system and your browsing (it even claims to monitor your Facebook browsing), and it has been around for a long time. They have a free version for individual users which can be downloaded from the link provided above.
Bitdefender (PC)
Bitdefender is another stalwart product that has been around for quite some time and is quite popular as an antivirus tool as well. They have also expanded their capabilities, and according to their webpage they will even monitor for rootkits, which are subversive programs that let people access your machine, and it even claims it can determine unknown threats based on how regular programs are supposed to work. Either way, it has been long-trusted as an anti-virus program.
AVAST has been around, in one form or another, longer than all the others. While it’s antivirus capabilities are very strong, there are some opt-ins during installation you want to watch out for; it’s best to choose a custom installation and un-check anything you don’t want. Strictly speaking as an antivirus service, it works very well.
Avira (PC / Mac / Android / iOS)
Although you don’t hear the name Avira all that much, it has been around since the 80’s and is very highly regarded as an antivirus program. It has a small footprint, smaller than most of the others even, meaning it uses less resources (generally) than many of its competitors yet still offers a full suite of protection options. I personally don’t have as much experience with this one as much as the others, so if you’re the experimenting type you can let us know how it worked for you!
Windows Defender (PC, obviously)
Windows Defender is a new program in the grand scheme of things, only becoming available for the first time with Windows Vista, however if you have Windows it’s likely all you need. It can be activated/deactivated from the ‘Action Center’ under ‘System’ settings in the Windows Control Panel. Surprisingly enough, it works very well and is as effective as the other programs I’ve listed, but it doesn’t provide any feedback or too much interaction, while the other programs listed provide a lot of information, detail, and hands-on control.
Malwarebytes AntiMalware (PC)
Very well known, well respected, and well trusted, Malwarebytes Antimalware is an anti-malware program, however the free version needs to be run manually. In other words, while all the others offer real-time monitoring, this one doesn’t, you have to run a scan deliberately. However, it is so well regarded that many people do a once-a-week scan using Antimalware, in addition to their regular protection with one of the others.
That’s all I have for now. Although it’s just a list with some brief comparisons and explanations, hopefully it provides a starting point. Remember, whichever you use is really a personal choice; they’re all comparable and it depends on which one you feel the most comfortable with. Experiment (but don’t use two at once!) and see what you think. The more security becomes an issue, the more you will need this type of thing.
Be sure to do an initial deep scan once you’ve installed your choice!
Interactive map of undersea fiber-optic cables
If you remember our discussion of networking, we talked about the Internet backbones which are vast, high-capacity fiber optic cables that traverse the ocean floor and connect major regions, countries and continents in a gigantic, overarching network that we refer to as the Internet.
Fiber optic cable is used because, as you’ll remember, it is not susceptible to interference from outside forces as it uses light being sent through a shielded, or in the case of fiber optic, ‘cladded,’ cable. These pathways can be owned and managed by academic or government institutions, as well as private telecommunications companies.There’s a great explanation of the physical cable on Wikipedia of all places.
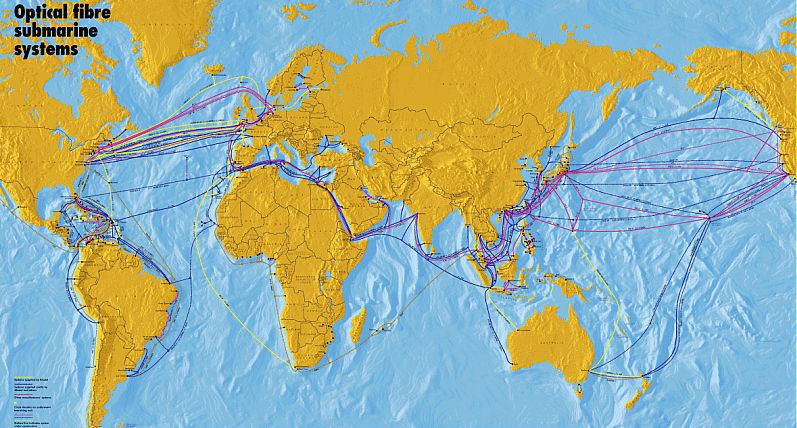
I sensed some doubt in a few of you that cables were truly stretched along the ocean floor. Well, they are, and I would like to present you all with a link to the Submarine Cable Map, which provides a ton of information about each individual sub-oceanic fiber backbone that is out there today. That’s a picture of it below.
 You can click on any of the trans-continental or inter-continental cables you see on the map and it will provide you with a wealth of information for each one, including when it was ready for service, what points it connects, and who owns it with their website. Some of them are owned by 20 or more companies!
You can click on any of the trans-continental or inter-continental cables you see on the map and it will provide you with a wealth of information for each one, including when it was ready for service, what points it connects, and who owns it with their website. Some of them are owned by 20 or more companies!
 The map uses standard controls for zooming and navigating, if you’ve ever used Google Maps you’ll be fine. You can click on any backbone segment to see relevant information, and click on an empty part of the map to reset them all. It’s very interesting to see the ways all the countries and continents connect among and within themselves.
The map uses standard controls for zooming and navigating, if you’ve ever used Google Maps you’ll be fine. You can click on any backbone segment to see relevant information, and click on an empty part of the map to reset them all. It’s very interesting to see the ways all the countries and continents connect among and within themselves.
an interesting selfie conundrum

We all know selfies are inane, unless they’re taken by Lord Vader of course. But Vader notwithstanding, we’ve all seen the dumb trends – from selfies of people wrapped in cellophane to the dreaded Duckface. Or any of these. And, well, all of these. They’ve been analyzed sociologically, and even linked to mental illness. But now, thanks to a wildlife photographer and a dispute with Wikipedia, an issue has cropped up over selfie ownership. It sounds pretty easy, Wikipedia’s stance is that whoever took the selfie owns it, which makes perfect sense. You take a selfie of (obviously) yourself, you own it, even if other people are in it.
But consider the ‘selfie’ below:
 According to this article on itv.com (from which the above image was lifted), this image was taken by the monkey itself when it swiped wildlife photographer David J. Slater‘s camera. The picture was a huge hit around the world, of course, perhaps the only animal selfie ever taken, and nicely framed to boot! Plus, my Chinese zodiac is the monkey, so I have an affinity for it right away.
According to this article on itv.com (from which the above image was lifted), this image was taken by the monkey itself when it swiped wildlife photographer David J. Slater‘s camera. The picture was a huge hit around the world, of course, perhaps the only animal selfie ever taken, and nicely framed to boot! Plus, my Chinese zodiac is the monkey, so I have an affinity for it right away.
Mr. Slater wants ownership of the picture which Wikipedia is now using without recompense to the photographer, because they believe it is public since the monkey took it, and even if it wasn’t it would actually be owned by the monkey since it took the selfie in the first place.
The whole thing is just bizarre. I mean, if your dog or cat or ferret inadvertently snaps a selfie of itself, do they own it? Perhaps it could be re-framed as an issue of who owns the device and the intent behind the image. I don’t know, but what I do know is this is one of the most bizarre intellectual property, technology and ownership stories I’ve ever seen.
I’ll just add it to the list of reasons I don’t take selfies.
The Future of this site

Before I get to the post, I would like to offer a heartfelt thanks to everyone who provided such positive feedback about this blog during the session. It was wonderful to hear all you learned form the posts that were made and what you discovered. It was a risky (remember that?) switch from the tried and true Blogger platform, but I believe the WordPress platform offers more flexibility, administrative tools, and potential for the future. But I really do appreciate the overwhelmingly positive response.
Building on that, and as I mentioned briefly in class, now that class is for all intents and purposes done, I have been asked by several of you if the blog will stay up after Friday. It certainly will, you are all more than welcome to continue to visit and comment if you so wish and I will continue to make posts that you (hopefully) find as interesting and relevant as any of the ones made during the session. I will also try to provide more in-depth how-to’s based on some questions I was asked over the session, and if you have anything you’d like to see or know more abut please be sure to ask. Many students both new and old still ask me questions and I’m happy to respond. If it warrants a post, I’ll put one up.
I will also, at some point in the hopefully near future, move the entire thing over to its own domain. I have already registered is301.com, and while there is nothing there yet, by making the move I intend to add additional interactive and social features making the site more dynamic and inclusive. I’m excited about it and we’ll see how it goes.
I’ll be making a few more posts this week so you have a chance to get any comments in, and thanks again for a great session.
Federal websites don’t screw around

This won’t be a very long post, I just wanted to show all of you that the federal government wants to be very clear in your expectations of privacy when using their websites. It also fits perfectly with the discussion of security and privacy we’ll be having tomorrow (or today, depending on when you see this). I was recently using the IRS.gov site when I was presented with this window:
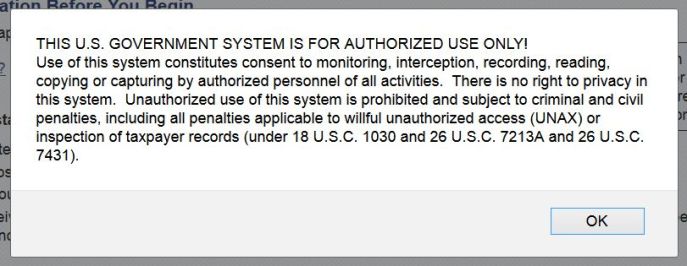 It almost sounds scary, but to be fair it’s no secret this happens. It happens on most websites, actually, government or not. Their wording sounds Orwellian and apocalyptic, but it’s par for the course when conducting business online. I actually don’t have a problem with it, you can’t have 100% privacy and also have 100% security, you have to make sacrifices in one to have any amount of the other. Even so, the wording is so forceful it gave me pause. Maybe I should have used my real name instead of the pseudonym “Gleeson McNasty.”
It almost sounds scary, but to be fair it’s no secret this happens. It happens on most websites, actually, government or not. Their wording sounds Orwellian and apocalyptic, but it’s par for the course when conducting business online. I actually don’t have a problem with it, you can’t have 100% privacy and also have 100% security, you have to make sacrifices in one to have any amount of the other. Even so, the wording is so forceful it gave me pause. Maybe I should have used my real name instead of the pseudonym “Gleeson McNasty.”
Look what I got!

I suspect many of you got the same thing. You will find at the end of this post an email from Cox claiming they have just doubled my Internet speeds up to 50 Mbps. I don’t even have to do anything!
That’s very nice of them. However I’d like to make a couple of points about this email; first, I tested my connection on Speedtest (remember that?), and I pulled about 27 up and (amazingly) 16 down with a ping of 36, which is good, not great. My national grade is a B+ and my regional grade A-, however subsequent tests to Mojave were slower while Las Vegas was faster, as expected.
However, the email has some important word choices in it. First, it says “up to” 50Mbps, and the fact is you never get the max speed advertised as that’s only a theoretical based on ideal network conditions which never exist. It also mentions at the bottom of the email you should use what’s known as a DOCSIS (the Data Over Cable Service Interface Specification) 3.0 compliant modem, and they’re right. If you’ve been using the same modem for more than a year or so, you might want to call up and see if they’ll upgrade you.
Speaking of making decisions

Since the session is winding down, I thought I would make a post about a show that I think is superlative, brilliant, topical, intelligent, and pretty dang funny to boot. It’s Futurama, created by the same guy who developed The Simpsons, and what makes it great is that it has actual Ph.D.’s on the writing staff, including one in mathematics that discovered and proved a mathematical theorem that was worked into an episode! There are also writers with Ph.D.s in chemistry and computer science, and one with a law degree.
Futurama doesn’t do lowbrow. Science and technology are intricately woven into every episode, it’s one of the reasons I hold it in such high regard. While so many television shows strive to make us stupid, Futurama strives to make us smart.
So what does this show have to do with class or making decisions? It turns out that there is an episode (episode 9, specifically) of Futurama from their ninth season titled “Free Will Hunting,” and the whole premise is that the Robot Bender discovers he has no free will and therefore lacks the ability to make decisions, after he lectured Fry on the importance of each decision one makes every day. Indeed, it is the seemingly small decision Bender makes to wear his ‘nerd glasses’ that sets off a chain of events worthy of Scorcese. It is brilliantly written, moves very quickly at first, and really offers an interesting commentary on the importance of making decisions, and the ramifications that can result.
It’s available on Netflix if you have a subscription, or if you know someone who has it it is definitely worth watching. I also thought about having an on-line episode viewing, but I suspect getting everyone together online at the same time is unlikely. But if you get the chance, don’t miss it!
Film may survive after all, sort of.

It appears that there may be a lifeline for stalwart American film company Kodak after all. They have had quite the struggle; filing for bankruptcy in 2012, removing their name from the once-iconic home of the Oscars, the Kodak Theater, an inability to keep up with digital competitors.
One the one hand, it’s hard to feel sorry for them. They screwed up repeatedly, for decades. But to be honest, myself and many others simply love film. It has an imperfect quality to it that coveys a realism lost with digital, and that was really brought to the front with the debate over the 48fps issue in The Hobbit (film runs at 24fps, the same speed at which the brain interprets movement). My TV is a plasma because it presents a warmer image than pure digital that makes any video viewed on it very full.
If you need further proof about people’s dedication to film, though, it looks as if some well-known film-director types including Quentin Tarantino and J.J. Abrams so love film they have agreed buy quantities of film from Kodak, even if they have absolutely no intention to actually use it. I also learned from reading the linked article that the new Star Wars is being shot on film. Now I can be a little more enthused about it, after the last three disasters.
Maybe we’ll see a revival. I hope so, I actually prefer video (maybe not pictures so much) shot on film, it gives real character.
Even TOR users aren’t safe now

Not that they should be. You see, there is a dark underbelly of the Web appropriately known as the Darknet. This is the place where people often carry out very illegal activities such as sell and buy drugs, find child pornography, suborn terrorism, traffic in weapons or even endangered species.
How does it happen? Through a project known as TOR, or The Onion Router, so named because it surrounds your browsing experience with many layers, like an onion. Essentially, when you use a TOR-compatible client you are routed through an even more labyrinthine series of points than you are when doing regular browsing. This makes it very, very difficult for anyone to track who you really are or what you are really doing.
Because TOR is so well-known for the bad things that happen, it has also been the target of white-hats who want to shut down those activities. It’s happened again and again and again., it’s a never ending battle.
 Now, a new attack has happened, however in this case it’s to strip away those protective layers and expose those who are using the network. The attackers are believed to be two researchers from Carnegie-Mellon University who claimed to have found vulnerabilities in the network, and are to give a talk at the Black-Hat Conference that will be taking place right here in Las Vegas this weekend! Those same researchers also discovered flaws in a similar anonymizing service known as the Invisible Internet Project.
Now, a new attack has happened, however in this case it’s to strip away those protective layers and expose those who are using the network. The attackers are believed to be two researchers from Carnegie-Mellon University who claimed to have found vulnerabilities in the network, and are to give a talk at the Black-Hat Conference that will be taking place right here in Las Vegas this weekend! Those same researchers also discovered flaws in a similar anonymizing service known as the Invisible Internet Project.
A lot of bad things happen on the Darknet, but it is also important to keep in mind it is also an invaluable tool for those who might have their privileges of communication stifled in any way, such as those living in oppressive (or not-so-oppressive) and restrictive regimes where access to the Internet is strictly controlled or prohibited to hinder dissent. In that sense it’s a valuable tool, but anything used for good can also be used for bad.
(Header image from cyberwarzone.com)
A most unusual post

Today I am writing two letters of recommendation for former students hoping to attend grad school, and doing a hardware review for a company’s network, so i won’t have as much time as usual to put up posts as I had hoped. Therefore, I am going to do something I have never done before and put up a post that is science-related but not technology-related.
C|net has an article about what would happen to you if your unprotected body was hurled out of an airlock and into unfiltered space. Don’t think it doesn’t happen; if The Hitchhiker’s Guide to the Galaxy, Outland, and Futurama’s treatment of Attila the Hun, Dr. Moriarty and Evil Lincoln have taught us anything it’s that it happens all the time.
So if you’re ever at risk of being sucked out of an airlock, at least arm yourself with the knowledge of what to expect. As quickly as technological advancement occurs, you never know when you’ll find yourself floating in space!