Category Archives: Uncategorized
A very brief post about CAPTCHAs
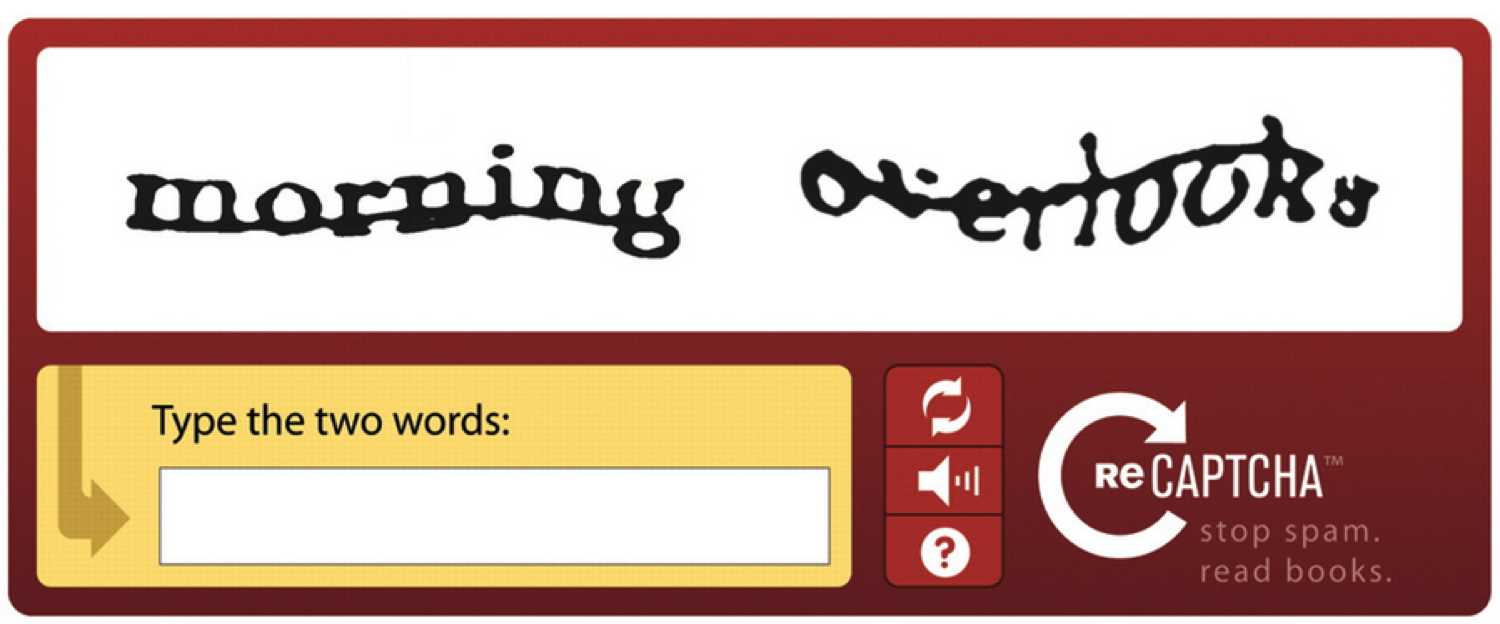
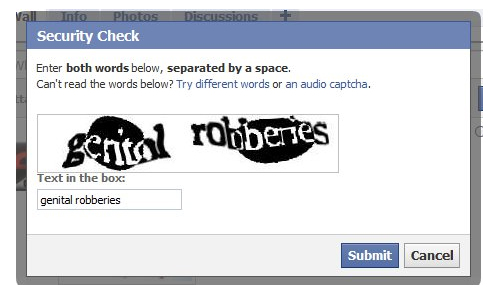
I don’t know if anyone is still hanging around, and I don’t want to start off the break by writing some long technical post, so I’m just going to mention that I found it strange after talking about CAPTCHAs a class ago I happened to come across not one but two different CAPTCHA related pictures. I thought they were pretty amusing, however I’m low-maintenance that way. Your mileage may vary.
The first is a very detailed and well-illustrated cartoon about the odd pairings of words CAPTCHAs often present. It was after reading it that I came to the realization that I laugh at the stupidest things:
The next image is what has to be the most unfortunate word-pairing ever made in a CAPTCHA (Actually, this one is a lot worse, but I just couldn’t bring myself to post it as an image). Word pairings are random, however that also means you get these unintentionally amusing phrases. I got a huge yuk out of this one too, but at least it’s readable!
The End

Today is the last day! As we wrap up the session, I would like to say it has been a pleasure being in class with all of you this semester, you were certainly a dynamic and engaging group and that absolutely made the class a success.
As I mentioned in class, I have been asked by a couple of you if you will still have access to the blog, and you absolutely will – I welcome all (legitimate) visitors and some students from previous semesters still visit the site. As long as you have a WordPress account you can even still make comments.
I will continue to make posts over the break, however I suspect not quite as often as I do during the semester (although I might – not sure), and it will pick back up to its regular pace when the Spring semester starts.
For the last Friday post, here is an oddball thing you can do from the command prompt. If you know how to bring up the command prompt, skip to the next paragraph. If not, to get the command prompt in Windows 8, bring up the tile interface by hitting the Windows key on your keyboard which is left of the spacebar, type ‘cmd,’ and click on the Command Prompt app on the left (or under the search bar in Windows 8.1). In Windows 7/Vista, click the Start menu, then click on Accessories, then click ‘Command Prompt.’ If you’re using a Mac, it’s the ‘Terminal’ program in the Applications->Utilities folder.
Once it’s up and running, if you’re using Windows type ‘tracert -h 100 216.81.59.173’ without the quotes, if you’re on a Mac type ‘traceroute -m 100 216.81.59.173,’ again without the quotes, hit enter, and impress your techie friends with the results of someone who had far too much time on their hands (it may take a few hops to enter the destination system, it usually starts after the asterisks). The tracert / traceroute command tracks each server a packet hits as it goes from a source to a destination across a network, and the ‘-h 100’ forces 100 hops so you can see the whole thing, otherwise it would timeout after 30, so by all accounts this required dedication.
I hope everyone has learned something they can use, I hope everyone got something out of the class, and I hope at least a few of you had fun. Best of luck for the rest of your academic and professional careers, and I will see all of you around.
The end of passwords? Hopefully.
Finally. Finally, formal standards have been published from the FIDO Alliance, whose aim is to do away with passwords through the use of techniques such as two-factor authentication and USB devices, and whose members list reads like a who’s who of big names: Google, Microsoft, Bank of America, Alibaba, ARM, Qualcomm, PayPal and Samsung, among many others.
I have been tired of passwords from quite some time, as you will or already have learned. Not only are you expected to have different passwords for everything, you are expected – in what I feel is the most repellant, counterproductive IT policy of all time – to change them every 90 days or so. Not only that, you can’t change them to something similar to the past five password you have used, and they have structural requirements involving length requirement, letters, numbers, it goes on and on and on. The result is that we end up re-using passwords that are easy to remember. Don’t believe it? Here you go:
“The Machine,” and a new OS
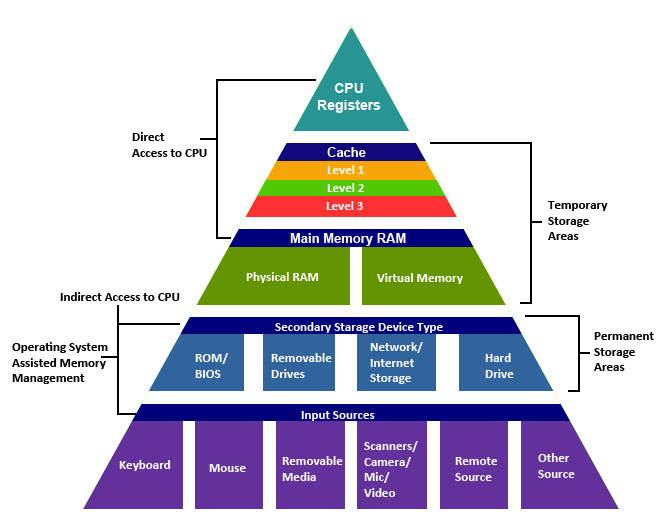
Back in the beginning days of this semester, we talked about a storage technology developed by Hewlett-Packard known as the Memristor, which is capable of storing massive amounts of data in small spaces, and in state. In other words, it doesn’t rely on the binary construct of 1 or 0, but rather the ability to store data as any value between 1 and 0.
Recently, HP announced an ambitious new project they have dubbed The Machine, which is meant to improve system architecture by using its Moonshot servers as well as fiber to connect the CPU directly to storage without the physical proximity constraints copper requires, vastly increase memory performance by using memristors (which is still considered a misspelled word by editors) to flatten the memory hierarchy we learned about, and top it all off with an operating system based on Linux that HP has cleverly dubbed Linux++. On a side note, ‘++’ in programing is how you increment a value, and it comes up in naming conventions a lot; for example, the notepad I use over the built-in Windows notepad has the name of Notepad++, and coincidentally if you do any programming, it’s a necessity.
Class up your joint with some 3-D printing
Finally, a practical use of a 3-D printer: Making your house a trove of ancient artifacts, just like a museum! Not actual ancient artifacts of course, but you know, close enough! Your uncultured lowbrow friends won’t know the difference, so let’s start impressing!
3-D printers are relatively new to the consumer space, the name most well-known in the field being MakerBot, however I have seem them on display in Best Buy and the Microsoft Store, running around $1300. The picture below is one I took of a 3-D printer at Best Buy in late November, but they are boxy looking things into which you feed a thread of plastic, then feed in a design, and it will ‘sculpt’ the design right in front of your eyes!
The Background

Another game related post. I try not to post too many of those, however it just so happens that this week those are the stories that came up for the site. This was actually the post I had coincidentally intended to put up yesterday before I heard about the death of Ralph Baer, but that was obviously much more important.
Anyway, you may notice the new wallpaper for the site. It looks like random code, however it is in fact the actual C programming code for the legendary 1993 PC game DOOM.
Programmed by John Carmack, who as far as I can tell is the only person to become famous for their coding skill, DOOM was the game that introduced gaming to a larger audience. It wasn’t the first to use the first-person approach to gaming, but it was easily the most effective (and he programmed Wolfenstein 3D as well). He is one of the foremost authorities on code and design, and he recently left id Software, where he had been since before DOOM was released, to work for Oculus in developing their virtual-reality headset Rift. It is his belief in the project that gives me the belief that there is something viable in it.
Ralph Baer (1922-2014)

I had planned to write up a post about the new wallpaper, and what it actually is, however I learned yesterday of the terribly sad news that industry veteran Ralph Baer, inventor of the very first videogame console, colloquially known as the ‘Brown Box,’ has passed away at 92.
His importance to the field of technology in general, not just the game industry, can’t be overstated. An electrical engineer whose family fled to Holland from Germany to escape the Nazis – something my own grandfather had to do – then relocated to the United States, he developed a prototype console that could control a “ball,” really nothing more than a square of light, on a television set.
He, or rather Sanders, the defense contractor he then worked for, licensed the technology to Magnavox, they marketed the resulting console as the Odyssey, and the videogame industry was born; it remains a powerhouse even today. If you want to see how we played TV games back in the 70s, you can play all the Odyssey2 (the Odyssey’s follow-up console) games that were ever made over at the Internet Archive.
How it used to be done

We’ve talked a lot in class about the evolution of technology, and the technology we used to use along with all the technology we still use. Although vinyl record sales have, somewhat surprisingly, been surging lately, with so much music being digital many people just haven’t had the opportunity to experience one of the joys of listening to analog music. Mainly, flipping the record.
You see, in the old days we’d use vinyl records, and after the needle got to the end of side A, we’d have to stand up, flip the record to Side B, and start it all over from the beginning. Finding a specific song was worse because we had to examine the record to find where the grooves clearly indicated the silence between tracks.
Stephen Hawking’s speech system gets an upgrade, comes with dire warning
This week there are two important stories, both relating to Stephen Hawking and to topics we have discussed previously in class. The first involves an upgrade to the system he uses to communicate, and the second is a dire warning from the man himself.
First, regarding the system he uses to communicate. For the first time in twenty years, it has received a major overhaul in how it operates. The story was all over the place, however none of the articles about it did a very good job in discussing how it actually works. Instead, they all mentioned a cheek-operated switch attaches to an infrared sensor on his glasses that lets him use the system. That’s a non-explanation, and even the person involved directly with the process did a terrible job of explaining it as you can see in the video on this USA Today page, so hopefully I can add some additional detail that will help explain how it operates.
It’s true that because of his affliction he only has relative control over the muscles in his cheek, and that is how he interacts with his PC. Via an infrared switch on his cheek, which communicates with an infrared receiver on his glasses that then sends a signal to a USB key on the bottom of his wheelchair that then communicates the choice to the PC, he can make selections on a screen. You can see the sensor in his picture below, and it works like this:
Oh no you don’t (Updated – it gets worse, then slightly better)

Another Thanksgiving-related post, and my first ever take down notice! Last Thursday, since it was turkey-day, and since we talk about robots in class, and since Carl Brutananadilewski was our mascot for the chapter on e-commerce, I thought I would post the Aqua Teen Hunger Force episode titled ‘The Dressing.’
This episode revolves around a robot turkey who comes from the future to take Carl, who it turns out is a hyper-evolved chicken from the future, back to save the robot turkeys from annihilation by their chicken overlords. Or something like that. Honestly, it’s a little hard to follow
In order to make it easy to embed in a post, I uploaded it to YouTube who instantly informed me that even though I had set the video to ‘Unlisted,’ it contained copyrighted material and may be in violation of copyrights.