Category Archives: Security
Destroy your stuff with just a USB stick

Hey, now this sounds fun! Want a simple, effective, and inexpensive way to destroy your expensive stuff and all the data on it? Well do I have good news for you! Now, with just a simple USB stick you can blow up damn near any digital device with a front-facing USB port (meaning publicly accessible, it doesn’t actually matter which direction the thing is actually facing. An important distinction).
The USB Kill will charge itself from the USB’s power supply, then discharge itself back into the port, over and over again until the host device is broken. Of course they say don’t use it for malicious purposes, but come on…why else would we want one of these things? Oh right – ‘testing’ purposes.
To be fair, everyone knows USB ports are a haven for malicious attacks, they’re the mosquito-breeding stagnant pond of digital devices, a very easy way to infiltrate a system or exfiltrate (steal or lose) its data.
It’s a pretty nifty device, in and of itself, and another interesting point they make is that only Apple devices are protected against this type of attack out of the box. Everyone else, well, look out (also, it might not destroy the data, and if it doesn’t, then NSA-approved bulk erasers are for you!).
WordFence to the Rescue!
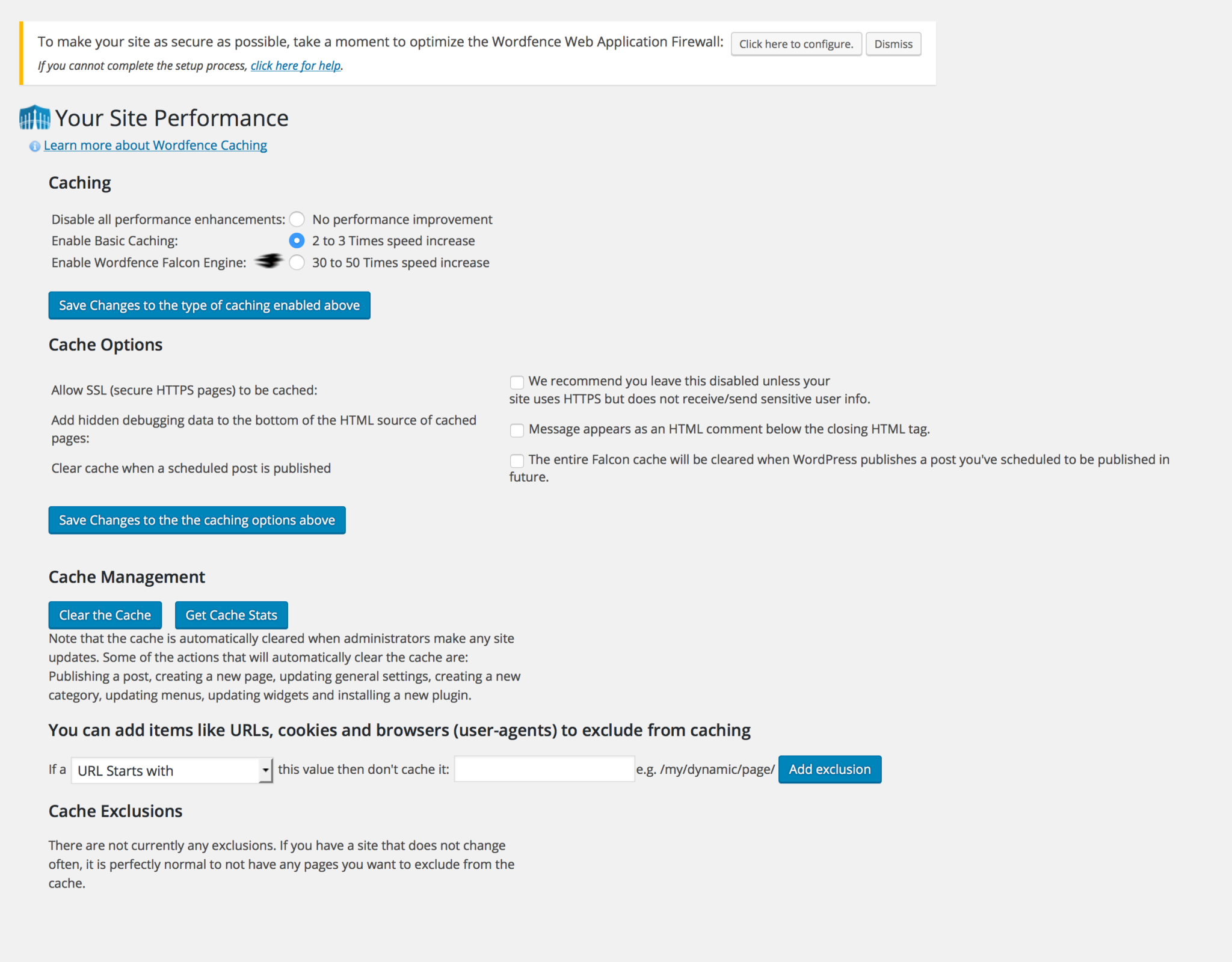
Over the weekend, I added WordFence security to the site. WordFence is a free (with premium option) service that provides backend security and monitors a WordPress site and prevents all sorts of bad things from happening. It has a slew of options and services that can be configured in any way a user would like, providing some peace of mind.
As you can see, the services and options it provides are many:
It has, for example, a firewall that prevents unwanted actors from gaining access to your site, however as with any good firewall you can whitelist sites or block sites as you see fit. It also claims it learns as time goes on, however I’m not able to test that at this time.
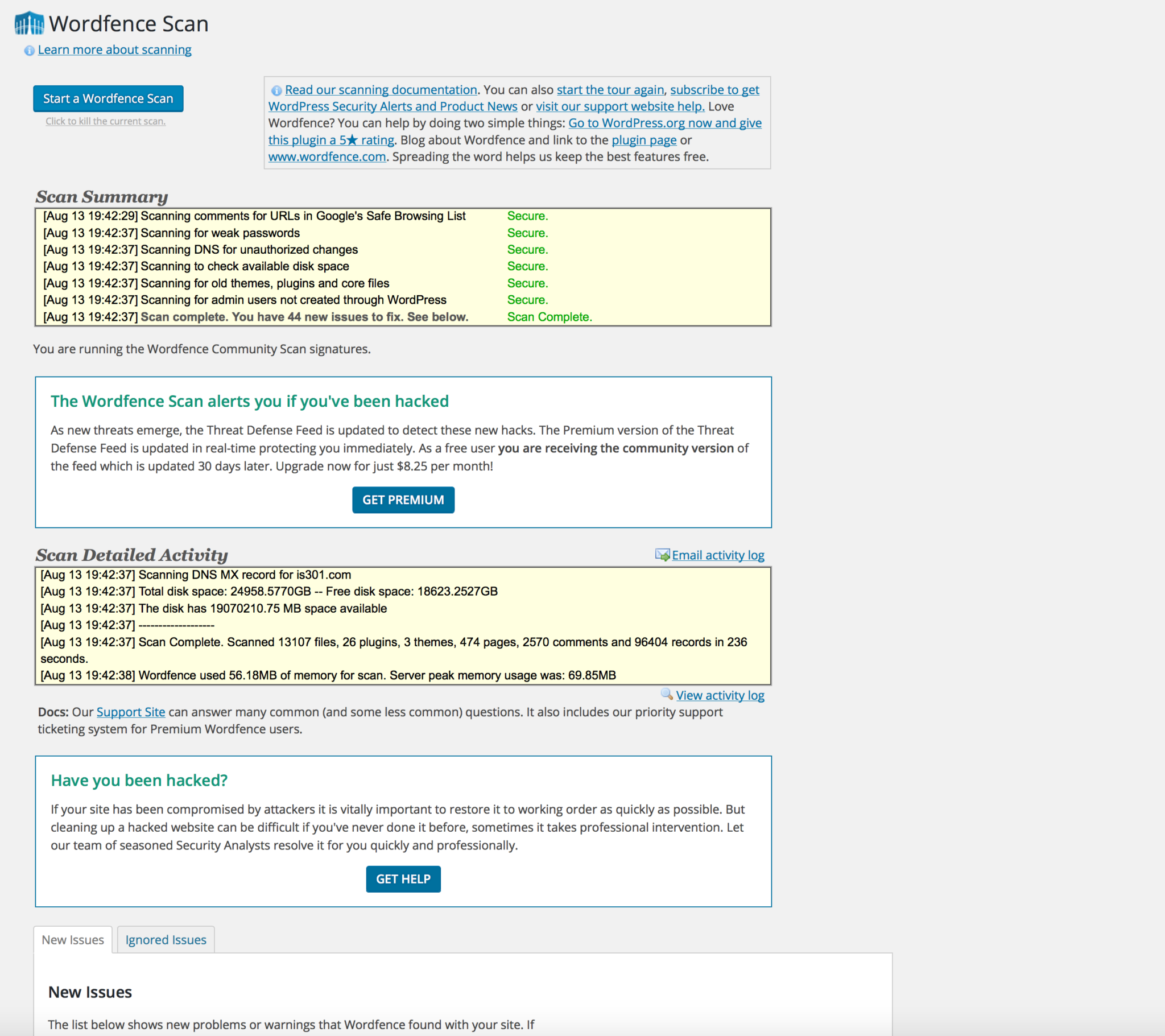
I’ve had this site for several years now, so as you can imagine with all the posts and photos and links there are a lot of potential hazards, and the service did a complete scan to be sure everything was on the up and up. It found a potentially malicious link in one of my posts from two years ago, and although the link was simply giving credit for a header image and not actually malware, I deleted it anyway. It scans everything for malware, the aforementioned malicious links, and any other problems and ranks what it finds in terms of its severity. I’m glad to say this site, to paraphrase Tangina Barrows, is clean.
There are many, many, many options. This kind of thing can often result in a performance deficit, although I haven’t noticed any slowdown at all. On a curious side note, I was asked to download my .htaccess file before WordFence scanned my site and implemented itself which I thought was strange. If you’re not familiar, .htaccess is an Apache-specific file placed in a directory of a website that specifies some site functionality, such as redirects or even password access without having to modify the server settings; WordPress itself states that it “uses this file to manipulate how Apache serves files from its root directory, and subdirectories thereof,” and .htaccess functionality cascades to all subdirectories (it can be overridden with another .htaccess file in a subdirectory, but that’s for another post). Why they wanted me to download that they never specified, but I did and ended up not needing to worry.
Another interesting thing about the .htaccess file is that it has been around FOREVER!
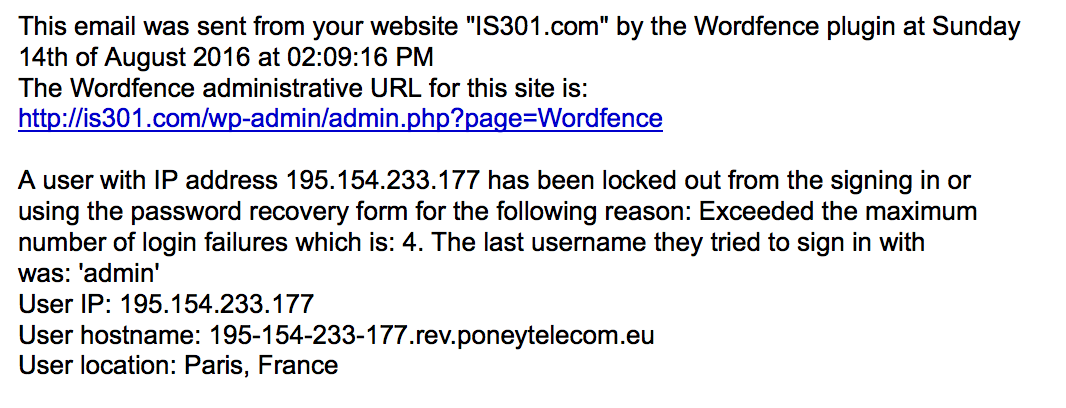
So with that sidetrack out of the way, the site is now more secure than ever, WordFence is running in real time, and I’ve already received some emails telling me about the login attempts they’ve blocked (from both Germany and France – I’m worldwide!) and how smoothly my site is running. I’m very happy with it so far. If you have a site and are interested, it’s very easy to install and can be done from the ‘install plugins’ section of the WordPress backend.
A huge mistake, and disaster averted

Other than not being a woman, I know just how that lady feels. Today was a bad day, and her expression was my exact expression earlier. You’ll notice over to the right, on the twitter feed, the words “OR DON’T.” That was the header image to a post I had written about two separate attacks this month that targeted remote access software. One attack on June 1st compromised TeamViewer, a program I use myself, and the second, more recent attack targeted GoToMyPC, hence the OR DON’T. Get it? Anyway, both were based on password reuse, so change your passwords if you’re affected. Or even if you’re not.
However after I posted it, I noticed that the LightBox functionality was not working on recent posts. LightBox is the function that causes an image to expand when you click on it while darkening the background. It’s only not working on recent posts, for older posts it works fine. I didn’t know why, and started to investigate.
New ransomware method to worry about

(Header image credit: makeuseof.com)
Over on security blog Bleeping Computer, there is a post about a new type of ransomware that presents a triple threat. Known as RAA, what makes this one different is that instead of using an .exe attached to an email which would pop up an alert when a user tried to run it, this one is written entirely in JavaScript, a language often used to encode and provide functionality for web pages, and if a user runs something written in JS it likely would not pop up any alerts, and the damage would be done before you knew it.
Enjoy the Internet while you can

This has been in the cards for a long time, but ICANN, the Los Angeles-based organization that has its fingers in many aspects of how the Web operates, will no longer be managed by the United States, but – according to this article in the Washington Post – by “an international body made up of technologists, businesses, governments and public interest advocates.”
This is a mistake. While I don’t have an inherent problem with a nebulous international body overseeing the continued development of the operation of the Web, what I DO have a problem with is that this will allow oppressive regimes who have no interest in freedom of expression or the open standards and ideas that the Web is built upon, and they could very well turn back the Internet clock, as it were.
I’m not being facetious when I say this could change the way the Web works forever. It could cease being the glorious, anachronistic Wild West that it always has been, and instead be regulated according to the demands of those who wish to stifle it and the free exchange of information it represents. Some governments, who have expended huge amounts of money and effort to limit what their citizens can see on the Internet, have been salivating over this moment for decades; we can all imagine why.
You’ll notice on page six of the transition assessment (.pdf here) states “This model encourages all parties—including businesses, technical experts, civil society, and governments—to participate and to reach consensus through a bottom-up process.” The problem is, governments will have ultimate decision-making capabilities and will overrule other stakeholders. I’m astounded there is not more attention being paid to this, or that the news isn’t covering it and, frankly, that people aren’t rioting. If they’re so willing to riot over the G20, which is *also* a multinational gathering – why not this? We should be very careful about who has influence over the future growth of the Web.
So enjoy the Web while you can, it could be changing soon.
Better change your passwords
Seriously. I’m not just telling you this because it’s World Password Day (it is, though, and I don’t know what Betty White has to do with anything). I’m saying it because it has come out that a security pro at Hold Security discovered an absolutely massive theft of usernames and passwords from Russia’s largest email provider, mail.ru, about 275 million stolen records. Not only that, there was a significant amount of credentials stolen from Gmail, Hotmail, and Yahoo account holders as well. Incidentally, many reports are saying ‘Microsoft’ instead of ‘Hotmail,’ which is a Microsoft property, but they also have Outlook which hasn’t, as far as I can figure out, been hit.
Most surprising of all, even more than the fact this is one of the largest theft of electronic records in history, is that the teenage hacker who acquired them was willing to sell the whole multi-hundreds-of-millions record lot for the grand sum of $1. But wait, there’s more! The hacker was discovered via his bragging of the theft in an online hacking forum, and when the Hold Security employee who engaged offered to leave positive feedback for the hacker, the price was dropped to free. That’s right, free for the mere quid pro quo of a positive review.
Off topic, but that touches on the concept of what is known as the reputation economy, in which someone’s actual worth depends on what others say about them in public and think about them in private. You can read more about it here.
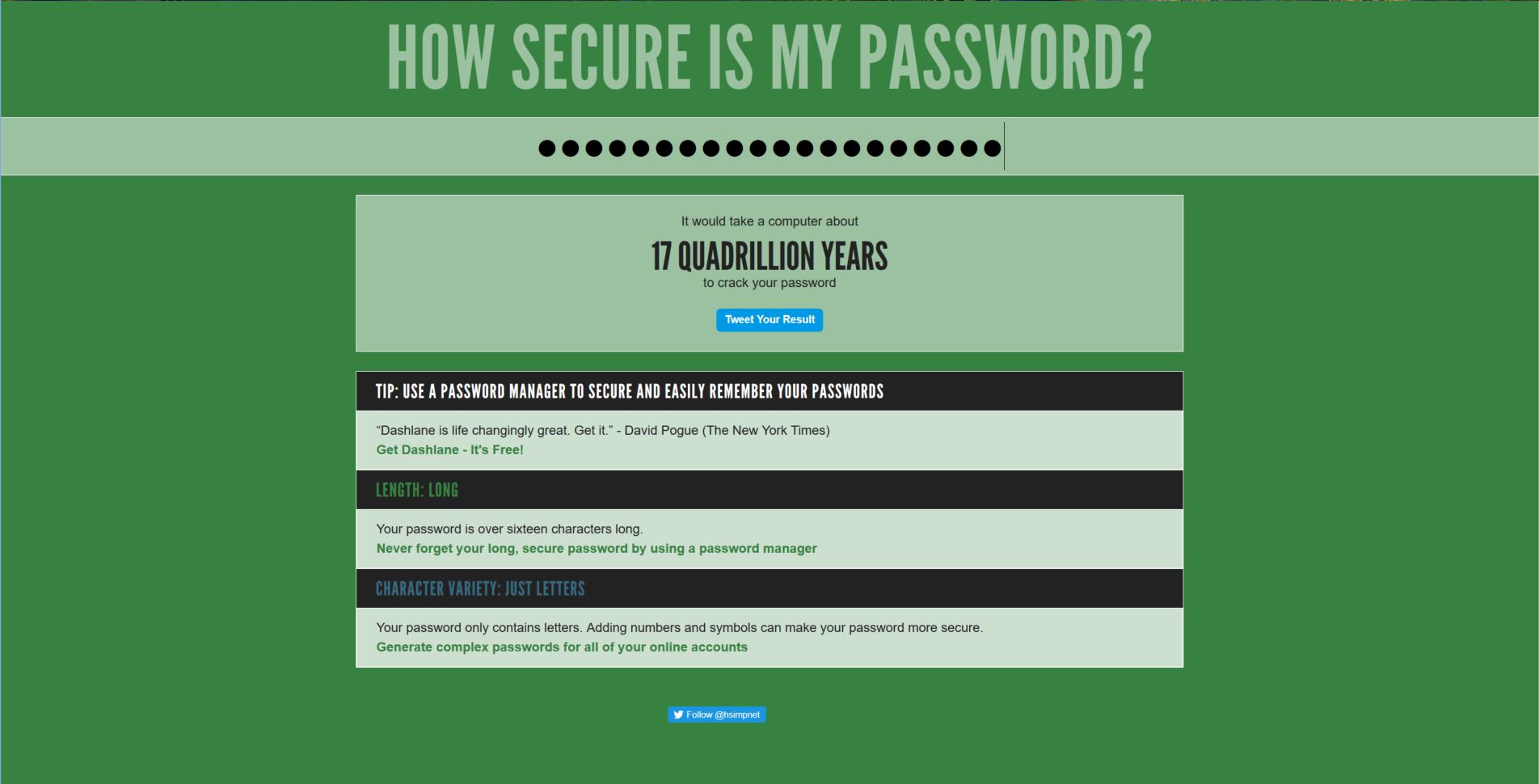
It’s no secret people use bad passwords all the time, and reuse them over and over for multiple functions and sites. Don’t do that! Use a passphrase – in class just today, my students suggested ‘sheturnedmeintoanewt,’ a line from Monty Python and the Holy Grail, which turns out to be a perfect passphrase. It’s long, complex, yet easy to remember. Plus, it would take 16 BILLION years to crack! How do I know? Because we plugged it into howsecureismypassword.net, and that was its estimate. Even if it’s off by a billion years or so, that’s still pretty good. If we capitalize just one letter, the ‘n’ in newt, it jumps up to 17 quadrillion years. This isn’t the be-all end-all for accurately determining password strength, but it’s a good estimator.
If you’d like to use a different password for each site or service, but are worried about keeping track of them all, you can use a password manager like KeyPass to manage them all. Some password managers even enter the passwords for you. I don’t know how I feel about that personally, but it is easier. Beware, password managers often have a master password and if you lose or forget that, you are screwed – you’ll be resetting passwords forever.
Everyone knows I hate passwords and especially the policies that go along with them, and I hope the scourge of passwords is one we can raze from this earth in the very near future, replaced with something more robust – but not 100% foolproof – like biometrics (fingerprint scanners, for example). Until then, just remember: It’s only a flesh wound.
I don’t know why I bother
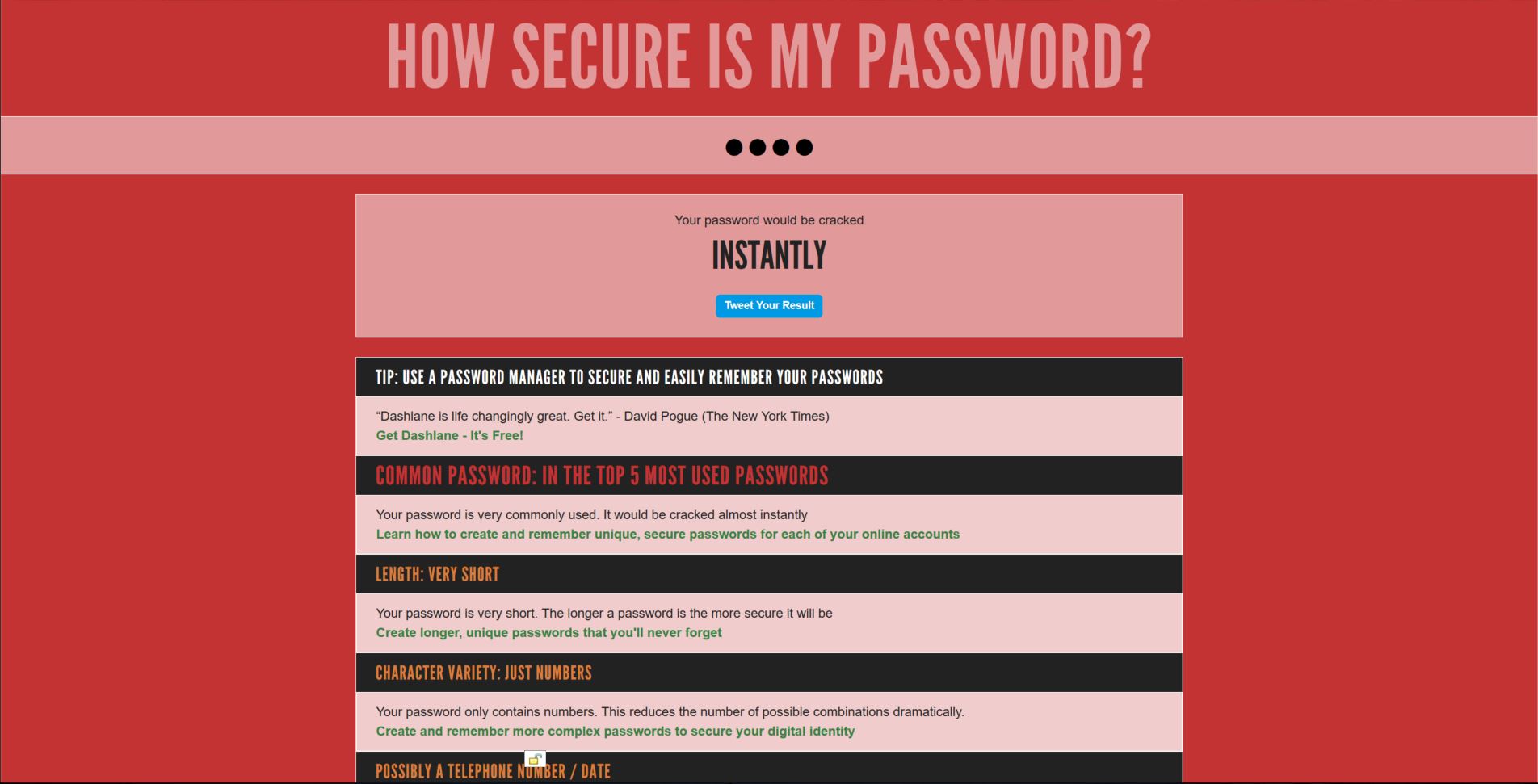
SplashData has, as they are wont to annually do, released their list of the worst passwords of 2015. Definitely look at the link, there’s lot of additional information there regarding how dumb we are when it comes to this. Want to take a guess which terrible password takes the top spot? That’s right, 123456. Anyone suprised? Anyone? No? Frankly, if that’s your password, you deserve whatever happens. Not to be all alone, other number-based passwords made the list as well, including 12345678 and 123456789. Other idiotic passwords include qwertyuiop, login, and passw0rd. That last one is especially offensive, as though the person thinks they are pulling a fast one by having a zero instead of an o. They’re in for an unpleasant surprise.
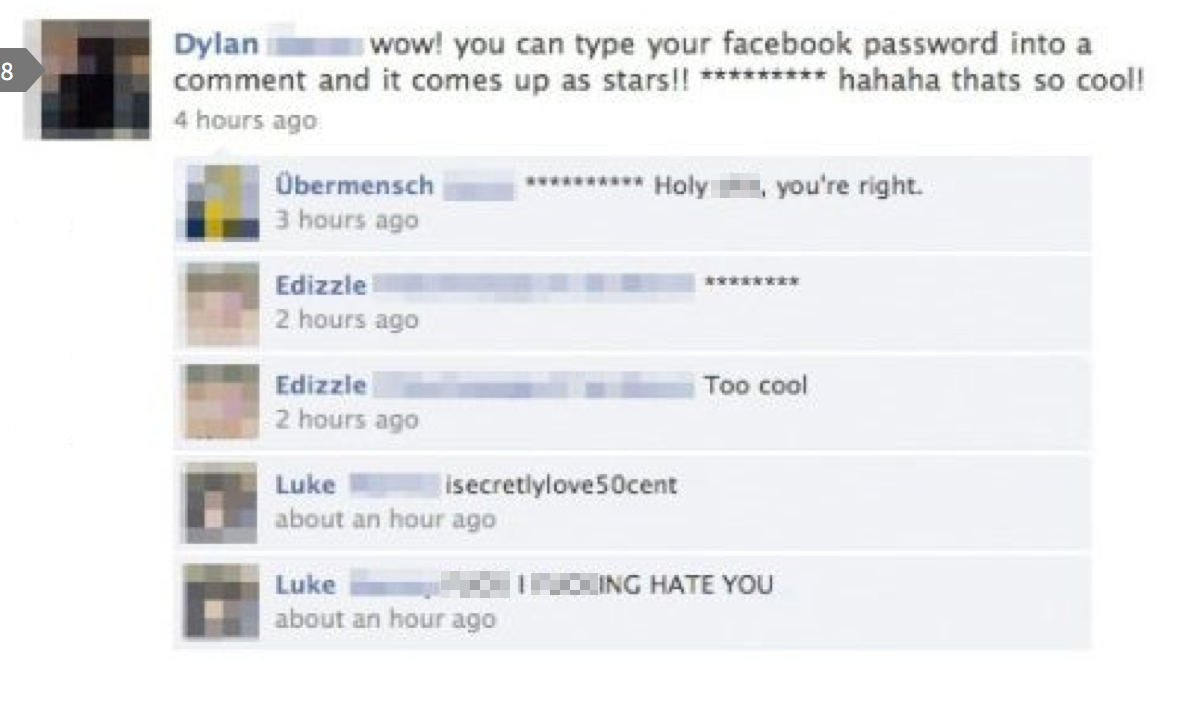
I used a different header image than I originally had intended, one that showed the bad passwords from 2014. They’re generally the same as last year, but I ended up not going with it because it was redundant considering the list below, but the original version of this post still referenced it. So I made a fun edit, and instead I found the Facebook post used in the header which – although I sincerely hope it’s fake – really very much hope that it is fake – shows how gullible people can be. If it’s real, I wouldn’t at all be surprised. Now hold on while I allow a Nigerian prince access to my bank account.
There are some passwords on the list that are less offensive, as though the person tried, including dragon and starwars, but geez oh man, at least throw a capital letter or exclamation point or something in there, even the passw0rd people up above did that. If you really need to make a strong password, remember a sequence of at least four random words is the best alternative, and hopefully one day passwords will go the way of the dinosaurs and disco (although I do love disco), and we can switch to things like biometrics full time. Here’s the full list, pasted from Cnet:
1 – 123456 (unchanged from 2014)
2 – password (unchanged)
3 – 12345678 (up 1)
4 – qwerty (up 1)
5 – 12345 (down 2)
6 – 123456789 (unchanged)
7 – football (up 3)
8 – 1234 (down 1)
9 – 1234567 (up 2)
10 – baseball (down 2)
11 – welcome (new)
12 – 1234567890 (new)
13 – abc123 (up 1)
14 – 111111 (up 1)
15 – 1qaz2wsx (new)
16 – dragon (down 7)
17 – master (up 2)
18 – monkey (down 6)
19 – letmein (down 6)
20 – login (new)
21 – princess (new)
22 – qwertyuiop (new)
23 – solo (new)
24 – passw0rd (new)
25 – starwars (new)
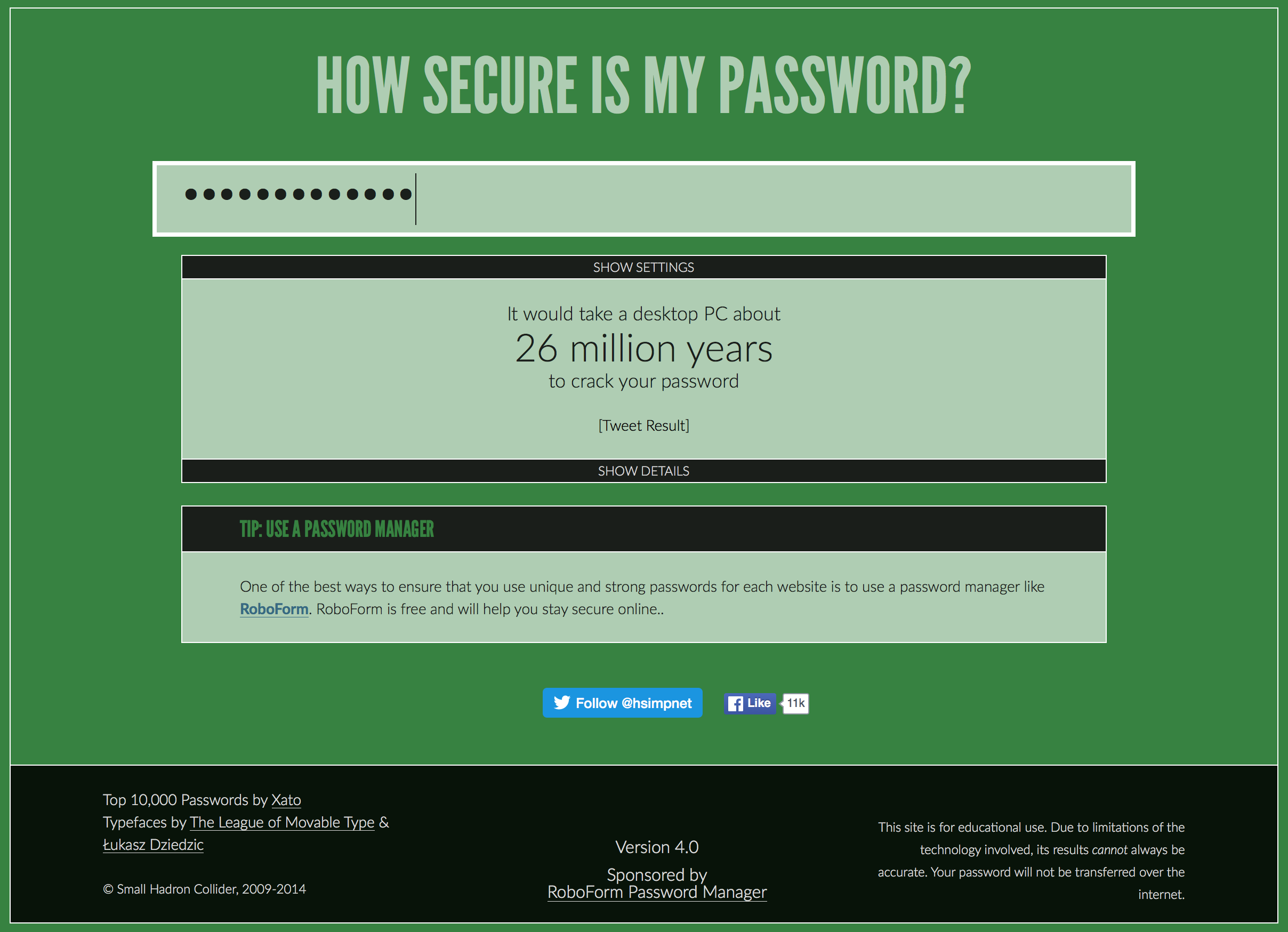
Incidentally, if you think you have a pretty robust password, and want to test if you really have the goods, you can go to howsecureismypassword.net and see. The site is legitimate, I promise, it’s not stealing your credentials or anything like that, and it will show you how strong your password really is. Here’s mine – I’ve got the process down.
The Ogre-Faced spider of drones

As many of you know, I considered going to grad school for biology, specifically because I wanted to investigate the cognitive capabilities of spiders. I believed there were certain species of spider that had the genuine ability to think and plan out strategy, and although I decided to pursue another path, I would also like to note that I have since been proven right. I knew it all along. Not all of them have the ability to think, of course, in fact I frequently use the example of a black widow and her behavior to illustrate concepts in artificial intelligence, specifically to define what is and isn’t intelligence.
So if you take a look at the lovely lady in the header image, you’ll see a spider that is unique in many ways, not the least of which is that it has two different and distinct colloquial names – one based on her appearance, and one based on her behavior. That’s unusual in the insect kingdom (which isn’t really a kingdom in the biological sense, but you know what I mean). Her first name is the ogre-faced spider, for reasons I think are pretty obvious. Her other name, however, is the one we’re concerned with and it describes not just her behavior but what I believe is at least a low-level ability to cognate: the net-casting spider.
That’s right! This spider makes a net, waits for some unsuspecting bug to mosey underneath, then not only traps the bug in the net, but will expand the net to fit the bug if necessary, or in some cases allow the bug to pass if she feels it will put up too much of a fight. And people say spiders can’t think. Or maybe they don’t say that, but if they do, they shouldn’t.
So why all the talk of spiders that can do the thinky thinky? Well, besides the fact that I use spider cognition – insomuch as it is – to explain artificial intelligence concepts, the netcasting spider is also the first thing I thought of when I saw this post over at Engadget: It turns out students at Michigan Tech are developing a drone that, just like the netcasting spider, can throw out a net to catch other drones in midair! How badass is that? Here’s the gif, borrowed from Engadget’s post:
The designers call it ‘Robotic Falconry,’ which makes perfect sense if you’ve ever seen a falcon hunt; they often pluck their prey, if it’s a bird, out of midair. The rogue drone, as it were, is similarly plucked right out of the air via net and hauled away, helpless, to someplace for…well, I’ll say tea and cake, but more likely disassembly.
I like this idea. It seems a less-lethal way of dealing with a rogue drone. If you think that perhaps this is addressing an issue that isn’t a real problem, you might want to read this post from Ars Technica. We don’t want to see anyone get hurt, and this guy was ready to do it. There’s a fascinating follow-up to that whole thing as well that could set law and policy about drones and would necessarily be very wide-ranging, covering ownership, privacy, property, and how all these things interact and overlap where drones are concerned. Additionally, as Engadget’s post also points out, Japan is testing a net-casting drone because shooting them down could be harmful if they are loaded with a dangerous substance, a problem they’ve already had to deal with.
This could all be focused into something productive, though. What we REALLY need is some kind of gladiatorial drone-combat sport thing – that would be fun to watch. Just like the BattleBots competitions they have, drone wars could become a real thing. A real, exciting thing. Drones with nets, drones with lasers, drones that shoot flames and crash into each other. I’d watch that.